poprbx
@pop_rbx
Followers
27
Following
211
Media
0
Statuses
17
Joined March 2021
My first research and tool are finally out. If you want to deep dive into some CLR internals and understand how we can abuse it to blend-in within its own logic go check it out. Hope you'll enjoy the read. https://t.co/FegHkegEE9
ipslav.github.io
Abuse the CLR memory (un)safety
9
72
186
Cool and useful interactive map of the Linux kernel Map: https://t.co/MJodidLmYK Source repo: https://t.co/NgEF6nHkS4
#Linux #kernel #hacking #programming #informationtechnology #kernelinternals
2
126
318
This is your yearly reminder that ALL Udemy Bug Bounty courses are a waste of money. The content you need is out there, completely for free. Don't believe me? Here is a list of the best Bug Bounty Ressources out there 🧵👇 #bugbountytips
#BugBounty
101
508
2K
Ever come across a file running on a Linux box that was deleted from the disk? Did you know you can likely use DD to recover the file without any non-standard tools?
26
587
3K
This book has been published in 2005 and is still one of the best references out there in terms of computer virology. Developing advanced malware and viruses will always be an art.
9
84
531
Bug Bounty Hunting Search Engine - Made by @payloadartist 🔗 https://t.co/FEjf3YlJNY
#bugbounty #cybersecurity #infosec
1
172
388
Firstly make a Full port scanning then run it @pdnuclei
@0xmahmoudJo0 command: rustscan -a 'hosts.txt' -r 1-65535 | grep Open | tee open_ports.txt | sed 's/Open //' | httpx -silent | nuclei -t ~/nuclei-templates/ #bugbountytips #BugBounty #CyberSecurity
7
163
359
If you collected a bunch of alive IP addresses. Don't run @pdnuclei directly on it, Firstly make a Full port scanning then run it, maybe you find some juice stuff on other ports like what I got XD !! The command: https://t.co/cB2zpzZez2
#bugbountytips #BugBounty #CyberSecurity
14
325
879
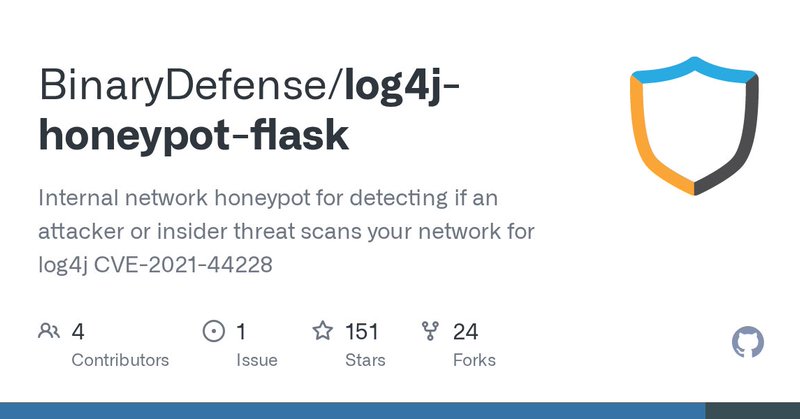
Blue team tool drop: #log4j internal honeypot for active defense. Alerts you by sending a message to your Slack, Teams, or Mattermost channel if it receives a GET or POST with suspicious ${ in headers or form fields. Use to detect scanning from the inside:
github.com
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 - BinaryDefense/log4j-honeypot-flask
4
156
392
I am going to use this image so many times
@a_centrist_15 @ErrataRob The little block the arrow is pointing to has a very serious vulnerability that is fairly easy to exploit.
1
2
16
Red-Teamers: [lazy]People like me use Notepad++ as a note-taking thing. We create a 'new', then never get around to saving them. They get cached here: C:\Users\{username}\AppData\Roaming\Notepad++\backup If you hit a dev/sysadmin, you'll find all kinds of crazy stuff.
29
436
2K