Phish Report
@phish_report
Followers
1K
Following
292
Media
98
Statuses
1K
Takedown tools for small security teams Tweets about phishing kit analysis, takedown tips, and new tools https://t.co/44hDmZ9xnj
Report phishing →
Joined May 2021
We're excited to release IOK, our open source signature format for phishing sites! 🎣 You can write IOK rules to: 🗂 Track specific phishing kits 🪝 Identify obfuscation and evasion tactics 👤 Attribute threat actors All 100% open source 💙 https://t.co/ZiJXv9LLuZ
phish.report
Open source detection rules for phishing site techniques, kits, and threat actors
1
27
108
🎁 Every day this advent, we're releasing a small phishing detection challenge where you can learn: 🎣 Good techniques for finding phishing sites 📝 How to write IOK rules (our open source rule language) Here's today's introductory challenge:
phish.report
Phishing sites often use domains containing the brand name they're impersonating. Let's find a phishing site where the domain contains "stripe"
0
1
4
Every week we're sharing one interesting phishing kit/technique/tactic on the Phish Report community forum Follow along here:
0
0
3
Previously we could use the quirks of each reCAPTCHA implementation to distinguish between threat actors, but here thousands of sites are using an identical implementation (though still possible to gain some intelligence through the re-use of reCAPTCHA API keys)
0
0
2
We've seen a huge increase in the use of LiteSpeed's "Bot Verification" page over the past few months 📈 Using reCAPTCHA isn't a new tactic, but using LiteSpeed makes detection significantly harder
2
1
11
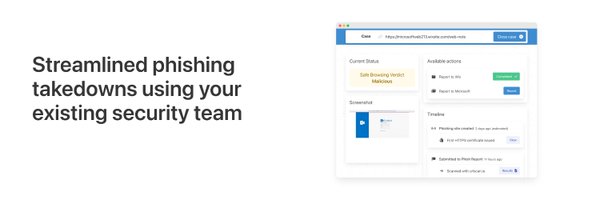
Alerts that don't explain themselves are bad alerts 👎 That's why our new analysis page shows you exactly why we think a website is malicious 💡
0
0
2
During our investigation we: 1️⃣ Identified reliable indicators of when a phishing site is being operated by RedLungfish 2️⃣ Emulated the admin panel to discover its capabilities 3️⃣ Pivoted to identify threat actor infrastructure spanning the last six months https://t.co/7tpEUKU94r
phish.report
0
0
2
❗️ Phish Report has identified a new organised phishing group (codename RedLungfish) who are targeting dozens of financial institutions They employ multiple human operators who interact in real time to trick victims into handing over their credentials https://t.co/7tpEUKU94r
phish.report
1
4
11
Nothing more satisfying than seeing a wall of flags, all of these are scanning locations available through Live Scanning on our urlscan Pro platform 😊 More to come in Q4!
1
1
24
4️⃣ CWE-425: Direct Request ('Forced Browsing') Some more advanced phishing kits have admin panels that the phisher can use to monitor the status of their site. While these are usually password protected the implementation is poor and parts can be loaded without authentication.
1
0
1
3️⃣ CWE-807: Reliance on Untrusted Inputs in a Security Decision IP addresses are commonly checked by phishing sites in an attempt to evade detection by security tools. However, we almost always see this code implemented incorrectly allowing them to be easily bypassed
1
0
1
2️⃣ CWE-548: Exposure of Information Through Directory Listing Open directory listings give us a range of useful information. From discovering log files, to the phishing kit source code, or even just the capabilities of a phishing site, it's all valuable input for defenders
1
0
1
1️⃣ CWE-219: Storage of File with Sensitive Data Under Web Root One of the most common ways phishing sites collect victim's credentials is by writing them to a log file. But, the vast majority of phishing sites that write logs this way, fail to protect the log file!
1
0
1
Combatting brand impersonation is more than just reporting abuse to hosting providers. Here's the top 4 vulnerabilities we find in phishing kits that you can use to disrupt an attack 👇
1
1
7
How does VirusTotal's new Netloc YARA extension compare with IOK for detection malicious websites? Netloc: extensive attributes you can match on, but proprietary and enterprise-only IOK: more limited attributes available, open-source and self-hostable https://t.co/PWp77rD0l4
0
1
4
3️⃣ Don't be generic: if your log-in page is simply titled "Log in" you'll have a hard time distinguishing a clone from all the other login pages out there. Include your brand name to make clones stand out (even if they've changed almost everything else on the page)
1
0
2
2️⃣ Embed high-entropy strings: long, random strings are often overlooked by phishers but they make it extremely easy to detect a cloned page
1
0
2
Most phishing sites aren't created from scratch, they're made by cloning a real webpage. Here's three ways to harden a page against cloning: 1️⃣ Install beacon assets: if done properly these evade the cloning process and will call back to your server with the clone's URL
1
1
5
4️⃣ Building your own integration with our API:
phish.report
Detect, disrupt, and deter consumer phishing attacks. Phish Report gives your team the same capabilities as leading brand protection services.
0
1
2