Nate Guagenti
@neu5ron
Followers
3K
Following
3K
Media
162
Statuses
4K
@therealwlambert @anton_chuvakin 💯 enhance, enable, help, uplift, expedite, alleviate, move forward, etc.. any other words that are absolutes are a red flag.. only a snake oil vendor deals in absolutes
1
0
4
Quick blog post on a new ETW event to monitor "valid" KASLR bypasses through system calls: https://t.co/pK6omsholj
7
101
233
Check out the #opensource #Kafka #sigma interpreter @mpeacock1964 and I built: https://t.co/A6C9xyR0bN Load sigma rules in a topic and the kstreams app will appply them against your streams of observability data in real time! #cybersecurity #cyber inspired by @neu5ron @socprime
2
17
28
.@_humpalum from my team created a @sigma_hq extension for VS Code It's in an early stage but already pretty useful and we've already discussed the cool functions and snippets that he's going to add #Sigma #VSCode
https://t.co/qwN2owJ4Ca
4
47
142
Considering current situation when my country is running down I see no longer future in Russia for me and my family. I open for any job offers relevant to my LinkedIn profile. Pease DM me, for detailed CV. #NoToWar #НетВойне
7
63
203
In the last couple of weeks, we've been working @3CORESec on a little project we're calling MAL-CL. It aims to collect and document real-world/common "malicious" CLI execs of different tools/utilities. Feedback and contributions are much appreciated. https://t.co/G2spnhbrW2
github.com
MAL-CL (Malicious Command-Line). Contribute to 3CORESec/MAL-CL development by creating an account on GitHub.
2
29
84
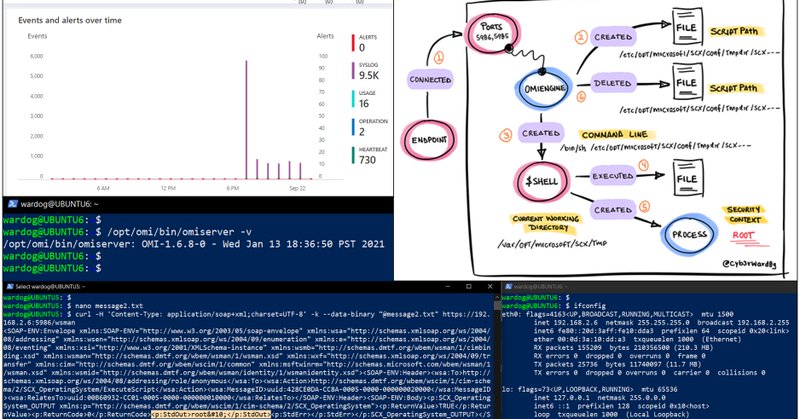
🚨 Sharing how to deploy a lab environment w/ #AzureSentinel , a few Linux 🐧 VMs and Microsoft Audit Collection Tool (AUOMS) set up 📡to identify & map sources of data to the execution context of OMI! #MSTIC #OMIGOD 😎 This has been very helpful 💥 https://t.co/tvEsO5CJia
techcommunity.microsoft.com
In this post, I will show you how to automatically deploy a research lab environment with Azure Sentinel, a...
4
110
310
Sigma rule by @Cyb3rWard0g to detect possible #OMIGOD exploitation attempts in auditd logs https://t.co/X0nbPQNmz5
2
59
172
While this has been used forever to create exploits. It's a very creative way of makng a JIT for architectures that don' allow allocating executable memory. The code can be seen in this commit: https://t.co/6sIbI17KgS (7/7)
github.com
2
4
43
🚨 A few detection opportunities while interacting with local AD hybrid health agent registry keys & Azure AD connect health AD FS services ☁️ 📡SACLs & 🛰️Activity Logs (Directory Activity) FTW 🛡️ #AzureSentinel : https://t.co/DYwUrfaVd0 🌎 @sigma_hq :
github.com
A few detection opportunities while interacting with the local AD hybrid health agent registry keys & Azure AD connect health AD FS service ☁️ 📡SACLs & 🛰️Activity Logs (Directory Activity) FTW
Did you know that local admin can export AD FS Hybrid Health Agent secret and create fake Azure AD sign-in events? 😈 Read my blog "Spoofing Azure AD sign-ins logs by imitating AD FS Hybrid Health Agent" to learn more & how to do it with #AADInternals 🔥 https://t.co/lMiJOOV9w4
1
36
78
Should cover the rest of PrintNightmare RPCalls for remote print driver install.
github.com
Zeek dce_rpc.log Detection of print driver installs over RPC (ie: possible PrintNightmare) using the three existing known RPC functions, as well as few others "discussed" but not ...
1
5
11
in short, some of the RPC methods of #PrintNightmare were within @sigma_hq since early 2020...
0
0
1
The main reason I added Zeek to @sigma_hq & thus w/ it logic of things like @MITREattack BZAR (slides above) was the historical/retro hunting you could do. Data is already being collected & sitting in a DB.. zeek scripts for the future, sigma for the past & those without scripts.
1
1
6
so 2 years before #PrintNightmare I am pretty sure @MITREattack w/ @Zeekurity was on to something ;) https://t.co/W3Wz1Pn7tI
1
9
21
Pull request created. Here is the Jupyter notebook under the forked repo : https://t.co/JXf7AancmA Examples: - Top tactics by number of events - Top 10 Tactics by EventIDs and Event Log Providers - Top 30 RelativeTargetName of EventID 5145 by ShareName - Sankey Diagrams
A project like EVTX-ATTACK-SAMPLES by @SBousseaden can be used not only to detect and replay attacks but also to provide info about most relevant telemetry providers and key events that you might consider enabling in your next SOC data quality assessment (Jupyter notebook soon).
0
14
26
60TBs of zeek logs, only 11 hits - pretty rare and pretty damn easy to weed out.. Zeek still remains one of my favorite sources for East/West (lateral) movement detections..
0
0
7
Detection for #PetitPotam RPC calls in @sigma_hq via Zeek dce_rpc.log (@Zeekurity). This includes many of the other EFS RPC methods, as there were discussions about detections lack of coverage of only 1 RPC call. https://t.co/NQDabBFq7I thanks to @Antonlovesdnb for the assist.
1
12
45
research from 2007 that mentions RPC calls used within PetitPotam as potential attack surface "Vista Network Attack Surface Analysis". if there is one there is more..
0
2
10
Sigma integration in Timesketch. Today we merged a feature to show Sigma rules in the UI. You also have the ability to search your timelines based on the generated query. #DFIR
6
60
202
From MISP to ElastAlert via Sigma MISP > Sigmai > Sigma Rule > Sigmac > ElastAlert a simple Bash Script by @therealwlambert
@MISPProject @sigma_hq @elastic
https://t.co/Ctr8lnD1E2
github.com
Convert MISP events to Elastalert rules. Contribute to weslambert/misp2elastalert development by creating an account on GitHub.
0
47
89