Michaline Todd
@michaline
Followers
676
Following
2K
Media
995
Statuses
3K
Tech Marketing Geek @strongdm, Wanna-be Chef, Urban Farmer, Chicken Mama
Silicon Valley
Joined November 2007
It would be nice if securing K8s had gotten drop-dead simple; it's only gotten more complex. Stay ahead of potential security threats by implementing these best practices for securing your Kubernetes deployments. #Kubernetes #BestPractices #ZeroTrust
strongdm.com
15 Kubernetes Security Best Practices: 1. Implement Role-Based Access Control (RBAC). 2. Use Network Policies to Control Traffic. 3. Secure Secrets Mana...
0
0
0
What's better than Privileged Access Control? Privileged Action Control! Check it out tomorrow.
You. Justin. John. Action Control. LIVE. Wednesday, 9/4. 🎬 . Register here: #databasesecurity #postgres #actioncontrol
0
1
1
BIG things are coming in 2024 and beyond!.
Today, we announce our Series C funding round and our global expansion of Zero Trust PAM in APAC + EMEA! 🎉. Don't just identify; STOP unsanctioned actions in real-time and ensure continuous compliance. Read on: . #zerotrust #startups #seriesc #funding #vc.
0
0
2
RT @strongdm: We're blowing the whistle on Access Madness. 🏀 Join our webinar to learn how to elevate your security game with continuous au….
0
1
0
RT @strongdm: Strong Policy Engine is LIVE! 🏎️ Make dynamic access decisions based on context for continuous authorization + Zero Trust sec….
strongdm.com
Context-based access controls refer to a dynamic and adaptive approach to managing security policies in modern infrastructure. Addressing challenges in ...
0
1
0
I bet your CEO doesn't send out pictures like this in the company pre-Thanksgiving, pre-re:invent email. I don't know how @Auxome comes up with these things.
0
0
1
RT @strongdm: Last call! Join us for a live webinar with @coveo tomorrow (8/23) at 10 AM PT to hear how they achieved zero standing privile….
strongdm.com
Security and usability. Traditional tools aren’t keeping up with the pace of modern work, and when users can’t access what they need, they find workarounds, compromising security and productivity....
0
2
0
RT @strongdm: Infrastructure access is a problem. It's hard to navigate. Hard to manage. Hard to keep secure. Hard to get the resources tha….
0
2
0
Thank you for standing up for women and calling out the inaccurate biases!.
Do you think men are better than women with money? No matter your answer to that question—AI does. The truth is, women are better with money than men in many ways—like their investment portfolios outperform men’s. It’s time to show the reality—help us change the face of finance
0
0
1
RT @strongdm: Join StrongDM's Cofounder and CTO, Justin McCarthy, and guest speaker, Forrester’s, Andras Cser, on June 14 at 11 AM PT for a….
strongdm.com
How do you even approach least privilege knowing the sensitive issues that are going to arise? What do you do when you know the privileges for employees are overflowing? Join featured speaker,...
0
3
0
RT @strongdm: Welcome to storytime with @strongdm. 📚 This week, we are featuring our customer, @cherrecore. Keep reading to find out how th….
0
3
0
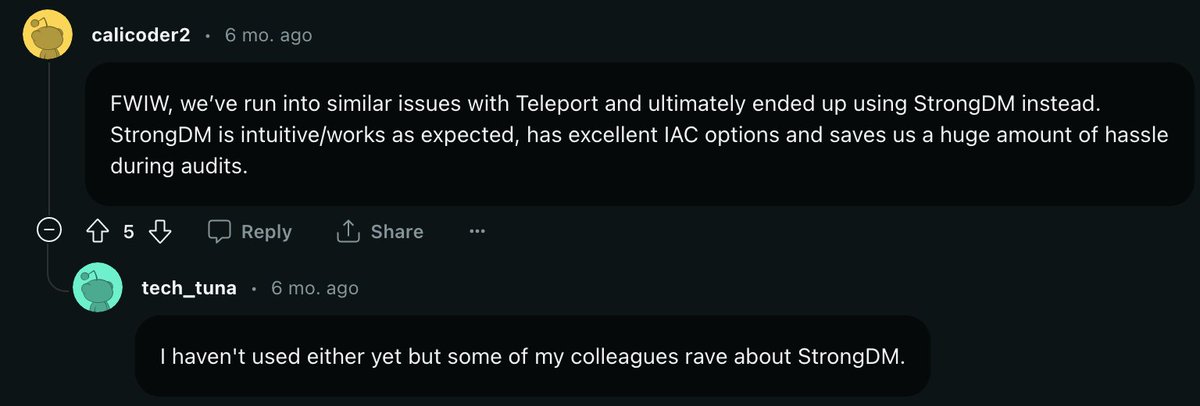
I love it when I stumble on this kind of stuff in Reddit. I love our @strongdm customers, too.
0
0
1
Of course your PAM lets you use whatever secret vault you want. wait. yours doesn't? Lemme guess, it doesn't support cloud, K8s or many databases, either. How did these limited use PAMs get so popular?.
Did you know third-party secrets managers integrate with StrongDM? Zero workflow changes required. 🤐 Keep reading: #secretsmanager #security #integrations.
0
0
2
RT @strongdm: April is #StressAwarenessMonth. Sadly, there's no shortage of stress in #cybersecurity. 😔 Your mental health matters. Did you….
0
2
0
You hear lots about how to set up new resources to align with Least Privilege. but what do you do when you're faced with access-sprawl? The first step is understanding exactly who is using their access grants!.
Answer critical questions + prove security best practices are enforced with Advanced Insights. 🔐.- How effectively are you enforcing least-privilege access? .- How quickly can you complete a recertification campaign?.- Who has access to sensitive systems?.
0
0
1
RT @strongdm: Are your current employees actually using the systems they have access to? 🤔 . If you're like 85% of the organizations survey….
0
1
0
RT @strongdm: Spring is the perfect time for a fresh start. 🌱 . Watch your team’s productivity, company security stature, and happiness blo….
strongdm.com
Eliminating Credentials to Make Users, Admins & Security More Productive (and happier). Watch this webinar to learn how.
0
2
0
RT @strongdm: Truly dynamic access is access that is provisioned and exists while it’s needed (just-in-time), and no longer exists when it’….
strongdm.com
Learn how StrongDM enables you to extend the protections of PAM to all of your technical users, as well as to the cloud and to technologies that may otherwise not be supported.
0
2
0