jinu
@lj1nu
Followers
3K
Following
710
Media
53
Statuses
163
Blockchain Security Researcher : ) jinu.eth
south korea
Joined September 2016
So we used the technique during the event. Because the 16MB padding made everything slow, we couldn’t use it everywhere, but we did hide one web exploit with it. Had a lot of fun experimenting with this during A&D this CTF.
gist.github.com
GitHub Gist: instantly share code, notes, and snippets.
1
0
4
My strategy worked, Tulip completely ignored anything past 16MB, and the exploit didn’t show up in its UI. The day before the competition, I asked the organizers whether sending large packets was allowed, and they said yes.
1
0
0
Checking the rules again, network/system DoS was explicitly banned, but there wasn't any clear restriction about bypassing or confusing another team's internal tools. Kind of a gray area. I let the AI run local packet captures, run Tulip, and generate testcode using sample chall.
1
0
0
While discussing it with AI, it suggested a clever idea: Tulip can’t process flow items larger than maxFlowItemSize (default 16MB). If we made the response bigger than that before triggering the exploit, Tulip should ignore the actual payload.
1
0
0
So I wondered: “What if we attack Tulip itself so our exploit doesn’t get detected?” I dug into Tulip and the Go libraries it relies on. There was an old gopacket bug, but it wasn’t practical to use inside A&D traffic.
1
0
1
While preparing for A&D, I got curious about what tooling other teams were using. After asking Gemini to do some OSINT, we found the us-cyber-team GitHub and another repo that looked like it belonged to ECSC, they were using Tulip to analyze packets, just like our Asia team.
1
0
0
I participated in ICC 2025. ICC is a CTF where teams compete by continent, with both Jeopardy-style and Attack & Defense CTFs. I wanted to share a fun story from the A&D, where I tried exploit other teams internal tools. Thanks to the organizers and players @icctokyo2025
1
7
71
If you're using Cursor and search for "solidity" in extensions, you'll see many results — but be careful, one of them added yesterday is spreading malware.
2
1
7
When CTF meets Bug Bounty At WACON CTF Finals 2023 I created an Opera challenge. Only one solver: @lj1nu . Turns out his unintended solve uncovered a real UXSS in Opera Browser that could leak URLs & takeover any account that uses OAuth flow! https://t.co/xUYr4OfZOB
medium.com
CTF challenge led to discovery of a critical Opera GX UXSS bug enabling URL leaks and OAuth account takeover. Reported, patched, rewarded
6
26
166
I played two ctfs, CCE and ACSC, and my weekend disappeared 😇 CCE: 9am~6pm 3rd ACSC: 12pm~12pm 2nd 27 hours of ctf
4
0
53
We came 3rd at this year's DEFCON CTF Finals as @SuperDiceCode! Thanks to @SuperGuesser , CodeRed, and @SquidProxyLover for playing with us, and @Nautilus_CTF for organising.
0
19
105
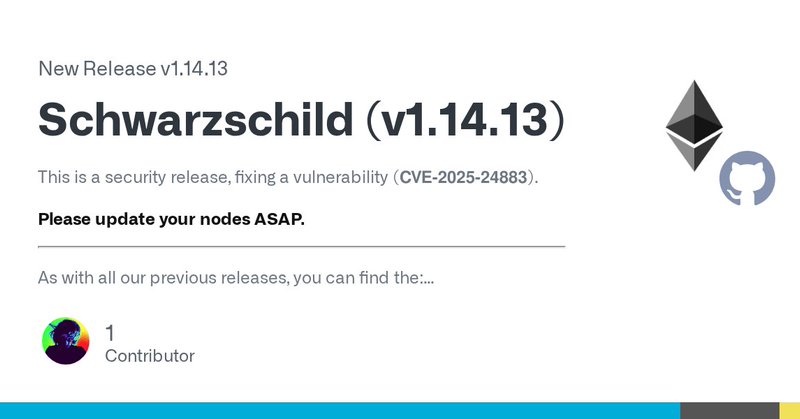
🚨PSA: go-ethereum emergency release🚨 We released v1.14.13 today which fixes an issue introduced in 1.14.0. If you are running a version of geth that 1.14 or later, please update to the newest version. Nodes running v1.13.x are not affected #ethereum
https://t.co/mXqkbIEziv
github.com
This is a security release, fixing a vulnerability (CVE-2025-24883). Please update your nodes ASAP. As with all our previous releases, you can find the: Pre-built binaries for all platforms on ou...
5
58
167
🎉The KimchiPremium took 3rd place at Remedy 2025! 🎉 We're a Korean CTF team that plays for fun. Many thanks to the @xyz_remedy @hexensio for hosting such a fantastic CTF with fun challenges. Looking forward to the next one!
The biggest Web3 CTF is over: 🥇 @ChainLight_io 🥈 A-Team 🥉 @Web3Kimchi The Remedy CTF 2025 was @hexensio's first-ever competition. Check out all the highlights 🧵
1
9
28
Is the @_kaitoai Yapper Leaderboard Launchpad launching? A new domain related to the launchpad was added yesterday. Looks like something new is being created! https://t.co/gISOYjs06r
8
0
21
The @virtuals_io vulnerability was patched shortly after it was disclosed on X, and they've just paid a bounty for it. Timeline 1. I took a quick look at the Virtuals structure and found a vulnerability. 2. I tried to report it on discord, but there was a problem. 3. I posted
9
27
231
https://t.co/xRe0v9lG6j Inspired by this post, I took a look at the code for @SuiAIFun, a project similar to Virtual Protocol. Thanks to Move's powerful decompiler, analyzing code deployed on SUI and Aptos is relatively straightforward.
I took a quick look at the code and found the vulnerability in @virtuals_io They seem to have been audited, but when I contacted them, the team replied that they were not running a bug bounty. And they closed the discord channel I created to report the vulnerability.
1
1
17
Thank you @lj1nu for bringing this to our attention - a patch has been pushed. Security is of the utmost importance to us - we're working on a bug bounty program and will announce full details soon.
@virtuals_io After posting on X, I got in touch with the @virtuals_io team. They patched it very quickly. https://t.co/VywvsdFcxV
https://t.co/jd3Mmcxq43
66
48
467