Barak Sternberg
@livingbeef
Followers
291
Following
6K
Media
28
Statuses
289
🔊 "Wild IoT Tales" Talk is OUT! Learn about Latest Hackers' TTP's, Reverse-Engineer Industroyer2, Learn about New Conti Ransomware Strains and astonishing recent attack stories over critical infrastructures! 🔊 REC: https://t.co/t6LVWxlsCu 🔊 SLIDES:
lnkd.in
This link will take you to a page that’s not on LinkedIn
0
1
4
This was the random link I found on LinkedIn, which contains the BugBounty guide! Source: https://t.co/CgbjdQ4GSr I don't know about the quality of the material, just sharing coz maybe it helps #infosec #bugbountytips #Resource #Hacking #infosecurity #CyberSecurity
9
242
789
For those of you who are finding #SharePoint Pre-Auth #RCE ( #CVE-2023-29357 + CVE-2023–24955 ) too technical to understand, here's a simplified version. 🧵(0/n)
4
77
267
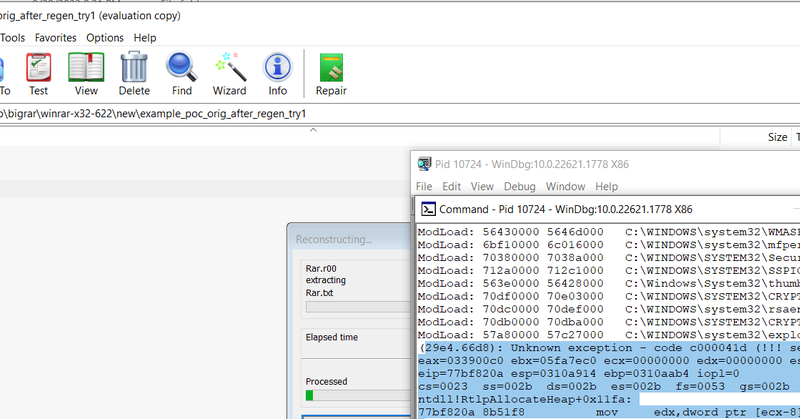
Excited to publish our PoC & analysis for Winrar's CVE-2023-40477 https://t.co/gVKehxiTM9 Interested in More Research? contact us @ wild pointer - contact@wildptr.io #winrarvulnerability #securityresearch #winrar #cve_2023_40477 #cve202340477 #winrarvuln #recvol3
wildptr.io
CVE-2023-40477 WinRAR Vulnerability: In-Depth Analysis, Proof of Concept, Exploitation Techniques, Impact, Security Mitigations and Source Code Analysis.
1
20
39
Critical RCE flaw (CVE-2023-29017) discovered in popular #JavaScript sandbox module vm2. All versions, including 3.9.14 and prior, affected. Learn more: https://t.co/WTT6JtMFx8
#cybersecurity #informationsecurity
thehackernews.com
Critical RCE flaw (CVE-2023-29017) discovered in popular JavaScript sandbox module vm2. All versions, including 3.9.14 and prior, affected.
1
32
53
Played with Outlook CVE-2023-23397. Made a simple PoC email builder & sender featuring malicious reminder (just a Msg, no need to use a Task or Cal. Ev.). Critical 0-click account takeover on internal networks even after MS patch, no need to open the message on the victim side.
15
361
1K
you see, `syscall` actually calls `do_syscall`. which in turn calls `_do_syscall`. got it? and that turns around and calls `____syscall`. which is basically a wrapper for `__syscall`, that's where the magic happens. it does `arg->ops->syscall` which was set in a diff code path.
30
112
1K
lol
2
0
0
1/ חלאס עם cyber product feature parity 🥱 הגיע הזמן ל cyber VC startup parity 💡 יצאתי לבדוק 5 קרנות סייבר ישראליות עם 71(!) סטארטאפים 💪 ❓איזו קטגוריה ייחודית לכל קרן? אילו קרנות עם פורטפוליו דומה? 💰 ממי יוצאים הכי הרבה אקזיטים? 🦄יוניקורנים? כל הפרטים בסוף 👇 עושים סדר🧵
10
4
80
Me and Billy ( @st424204 ) created a series of pwn challenges called Fourchain for this year's HITCON CTF. Here are the posts about the Browser & Hypervisor part of the challenge: Browser : https://t.co/8S1jAc5ADo Hypervisor: https://t.co/u5JI8Riilv Enjoy ! #HITCONCTF2022
bruce30262.github.io
Intro
0
75
226
Prerequisite knowledge before starting to learn about web vulns: * Can you explain from start to finish what happens when a URL gets placed into the URL bar? * Do you know how DNS works? * Do you know about TCP connections? * Do you know how to read HTTP requests and responses?
13
127
515
This weekend I built =GPT3(), a way to run GPT-3 prompts in Google Sheets. It's incredible how tasks that are hard or impossible to do w/ regular formulas become trivial. For example: sanitize data, write thank you cards, summarize product reviews, categorize feedback...
327
3K
20K
Another appliance vuln down... CVE-2022-40684, affecting multiple #Fortinet solutions, is an auth bypass that allows remote attackers to interact with all management API endpoints. Blog post and POC coming later this week. Patch now.
17
438
1K
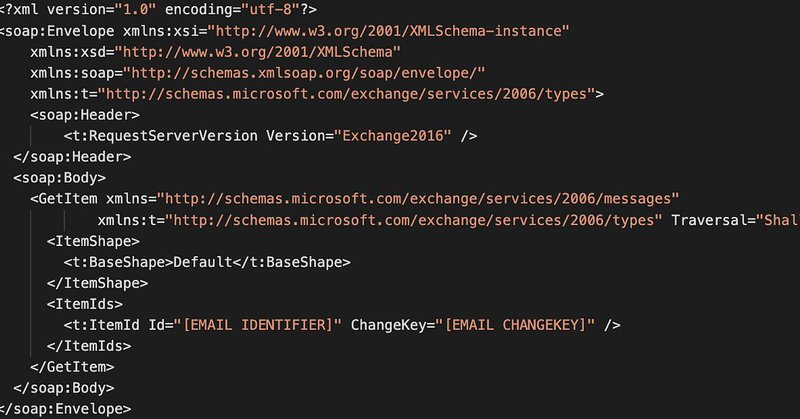
I've seen also samples remind of these https://t.co/KNQlA96NT9
vanshal.medium.com
Exploitation of Microsoft Exchange SSRF to read all the confidential emails of a company. (CVE-2021–26855)
0
0
0
*Instead of writing full emails like with .com and such: %XX@%YY.%ZZ..%WW etc
0
0
1
Lower Casing powershell as well: */powershell/ instead of Powershell
0
0
0
Probably WAF Bypasses Observed IN-THE-WILD for Exchange Zero-Days (CVE-2022-41040, etc..) #ProxyNotShell #exchangerce *Instead of writing Email / autodiscover: Em%61il=%61utodiscover/%61utodiscover.json? *Instead of writing ".json": %61utodiscover.jso%6E?
3
3
2
The latest Google Pixel 6 pwned with a 0day in kernel! Achieved arbitrary read/write to escalate privilege and disable SELinux without hijacking control flow. The bug also affects Pixel 6 Pro, other Pixels are not affected :)
40
269
1K