João Vitor(Keowu)
@keowu
Followers
388
Following
483
Media
3
Statuses
36
Reverse & EDR Dev | Jesus Follower | My RE friends discord server: discord dot gg/fWhvHXtzxy | https://t.co/cPfrnwC6jN | I just know that idk anything | 🇯🇵 🇺🇸 🇧🇷
Shizuoka-JP
Joined April 2022
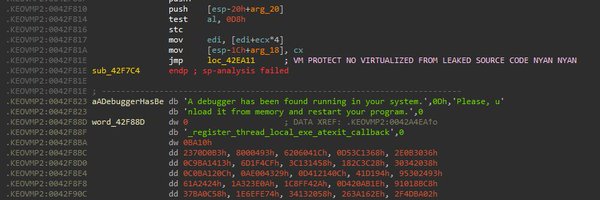
My new article using HexRays IDA. to deal with obfuscated code. comercial like VmProtect and OpenSource like Alcatraz:.
keowu.re
Analyzing Mutation-Coded - VM Protect and Alcatraz
2
78
223
My new article, "Writing a Full Windows ARM64 Debugger for Reverse Engineering," covers the topic in detail, including its internals and the core differences between Windows on Intel and ARM64:.
keowu.re
Author: João Vitor (@Keowu) - Security Researcher
4
84
270
It's great to be part of this with the Maldec Labs team.
Koidbg is a powerful tool designed for binary analysis and debugging. It is designed with a focus on simplicity and efficiency, offering an intuitive interface for exploring compiled programs. @Microsoft .@MicrosoftBr . #Windows11 .#Windows .#Microsoft
0
0
9
That's my PoC(I've been forced to publish, after the disclosure timeline), sorry for that. please blacklist this driver to avoid problems.
RansomHub ransomware operators have been spotted deploying new EDRKillShifter malware to disable endpoint detection and response (EDR) security software in Bring Your Own Vulnerable Driver (BYOVD) attacks - @serghei.
1
1
5
You can check the result final result and a cool stuff here:.
github.com
A Completely reversed from scratch Gamespy SDK 2000-2005 Emulator for Halo CE, Battlefield 1942 and Vietnam with full docs and papper. - keowu/gamespy
0
0
1
My new article. completely reversing the implementation of Gamespy from 2000-2004, reverse-engineering EA and Bungie games on original collector's editions to create our own emulator of the protocol used by it and play:.
keowu.re
Author: João Vitor (@Keowu) - Security Researcher
3
14
45
Também disponível em português para quem preferir ler no meu idioma nativo.
keowu.re
Analisando códigos com mutação - VM Protect e Alcatraz
0
1
6
RT @Unit42_Intel: #APT #AgonizingSerpens (aka #Agrius) has upgraded their capabilities. Analyzing a series of cyberattacks targeting #Israe….
0
16
0
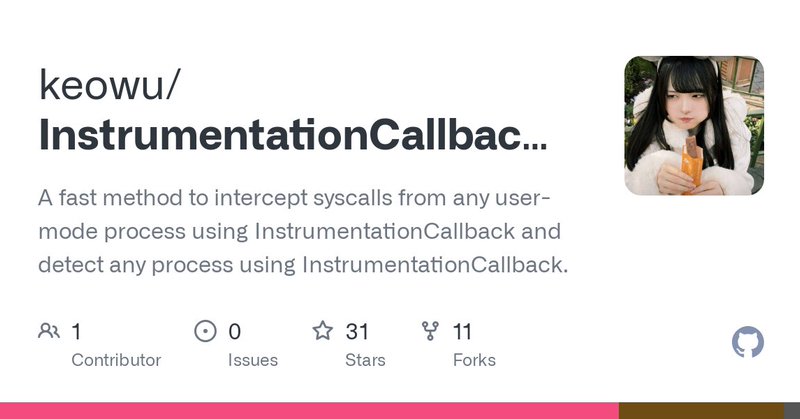
My project is able to detect syscall calls from a process (by installing an instrumentation callback) and retrieves their name, I also provided a way to detect this feature in any operating system process, I hope you like it.
github.com
A fast method to intercept syscalls from any user-mode process using InstrumentationCallback and detect any process using InstrumentationCallback. - keowu/InstrumentationCallbackToolKit
0
0
3