Mehta
@kartik_mehta8
Followers
520
Following
2K
Media
123
Statuses
806
Engineering @NovosLabs | Member @SuperteamIN | Builder @awscloud | Formerly @AIxBlock @pushchain @Social3Club
Delhi, India
Joined September 2020
I started digging deeper into what we can build with @SelfProtocol, and that turned into a series called "Self-Taught." It’s an end-to-end walkthrough of using Self Off-chain Verification complete with write-ups, architecture diagrams, workflows, and full code. Blogs: 1.
5
2
46
Free trials are frequently abused by users rotating emails or phone numbers. Companies could solve this by using protocols like @SelfProtocol to verify that it’s the same real person.
0
0
8
A passwordless authentication flow on @SelfProtocol would be awesome... imagine logging in just by scanning a Self QR code.
0
0
3
The dev urge to buy a domain for every project I create... Now I somehow own 7 domains 🫠
0
0
2
Developer question: have you ever created your own tool that ended up replacing a paid tool everyone else uses?
0
0
1
It happens we often have to keep track of our clipboard when we’re dealing with different features in the same repo. You’re fixing a bug in file A, refactoring file B, grabbing a helper from file C… then you switch branches or projects and the snippet you just copied is gone.
1
0
9
Why the gap? Rust’s scheduler keeps HTTP I/O cheap and bounded; the worker pool keeps Self SDK calls isolated so a slow verification doesn’t stall the loop. I broke down the Axum setup, the worker orchestration, and the next step, in a longer write-up: https://t.co/FMI0g9yfXD
writer.mrmehta.in
Combine Rust performance with Self Protocol's JavaScript SDK using worker pools. Learn the architecture for privacy-first verification in polyglot backends.
0
0
16
The metrics show a little improvement, but… when traffic spikes, Axum keeps the sockets breathing while a worker-pool manager fans requests out to Node threads that run selfxyz/core code. It hands work to a pool of pre-warmed Node workers; each worker talks to the Self SDK
1
0
16
Headline numbers: → Node averaged 1,607 ms. → The Rust + Node-worker combo averaged 1,373 ms. Even with the @SelfProtocol NPM code still executing in the worker, Rust shaved roughly 10–14% off the end-to-end path.
1
0
16
I fired 10 verification runs through each path (POST request on /api/verify). Every request wrote JSONL logs, so I pulled timings straight from `test/node` and `test/rust` without massaging the data. Pure stopwatch-style latency per request, no synthetic smoothing. If you
github.com
This repo compares a Rust + Node worker backend against a pure Node backend, captures per-request timings, and visualizes them in a Next.js client. - kartikmehta8/self-benchmark
1
0
16
I built a polyglot backend: an Express/Node service and an Axum/Rust service that still called into the @SelfProtocol NPM package via a tiny Node worker pool. Same Self flows, same payloads, just two language hosts vying for the front door. Here's what I found... 🧵
1
0
18
This is a POC, but it proves a powerful idea: Parental controls don’t need passwords or creepy tracking. They can use privacy-safe identity proofs. Kids stay protected. Parents keep control. No data gets leaked. If you want to explore the entire series where I’ve implemented
0
0
15
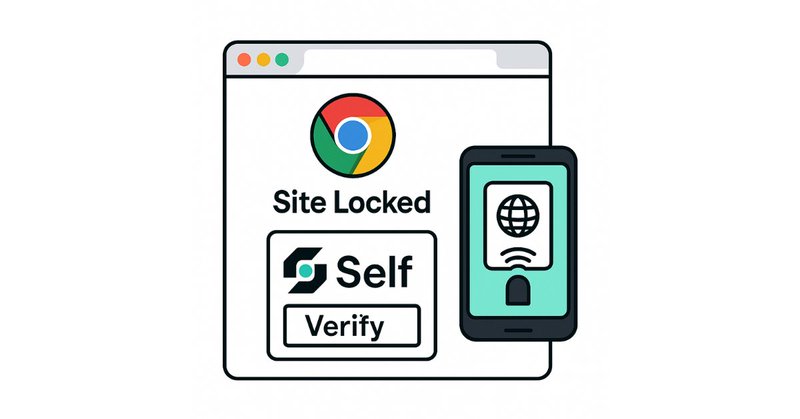
Now, why @SelfProtocol? Self uses zero-knowledge proofs to let a parent prove they’re the adult in the room, without exposing a single byte of personal passport data. That makes it ideal for secure, privacy-first Chrome parental controls. Imagine adding: – Time-based rules –
writer.mrmehta.in
A Chrome extension that locks websites behind real identity verification. Scan your passport with Self Protocol to get temporary access. No easy bypasses.
1
0
15
So I built Self Lock, a Chrome extension powered by @SelfProtocol: 1. Kids open a blocked site → page instantly blurs 2. Extension shows a QR 3. Parent scans it with the Self app 4. Phone reads their passport via NFC 5. Self generates a zero-knowledge proof (mock in dev) 6.
1
0
16
Most parental controls are weak: → Kids see you type the password. → They disable extensions. → They bypass DNS rules. → They outsmart every “blocker.” I wanted a system where only the parent can unlock a site, and even they need real identity verification, not a password
1
0
15
I built a Chrome extension that turns any website into a parental-control vault. Kids can’t open YouTube or Instagram unless you unlock it using @SelfProtocol 👇
3
3
27
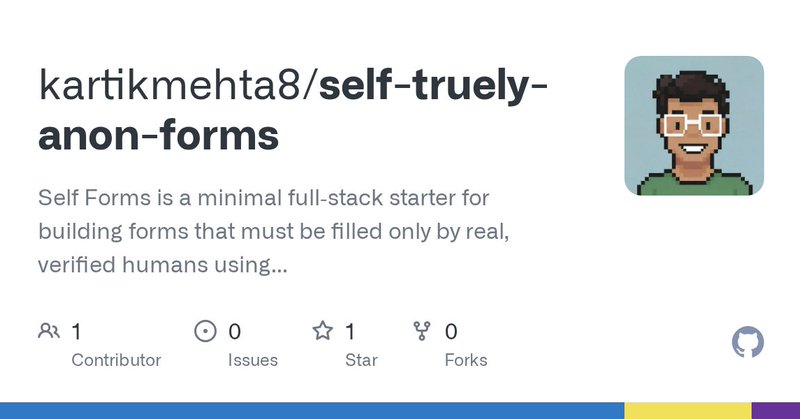
@SelfProtocol proves something important: we can verify humans, enforce rules, and meet compliance without harvesting identity or violating privacy. It flips the model, from “collect everything just in case” → to “prove only what’s needed, reveal nothing else.” Curious about
github.com
Self Forms is a minimal full‑stack starter for building forms that must be filled only by real, verified humans using the Self app. - kartikmehta8/self-truely-anon-forms
0
0
15
How It Works: 1. User opens the form 2. Sees a Self QR code 3. Scans → Self app does NFC passport reading 4. Generates a zero-knowledge proof 5. Backend verifies cryptographically 6. If valid → form unlocks 7. Submission stored with an anonymous hash ID Read full blog,
1
0
15
I created Self-Forms (PoC). My form unlocks only after you cryptographically prove: 1. You’re a real human 2. You’re 18+ 3. You’re NOT on OFAC sanctions 4. You’re a unique individual (1 person = 1 submission) But it collects: ❌ No name ❌ No passport number ❌ No nationality ❌
1
0
14
When you fill out an “anonymous” form, whether it’s a Google Form, Typeform survey, HR feedback form, or a company whistleblower form - they quietly collect: → Your IP address → Browser & device fingerprint (uniquely tracks you) → Cookies + tracking pixels → Device
2
0
15
Most company “anonymous” forms are NOT anonymous. They track your IP, device fingerprint, location, and metadata. So I built an anonymous, spam-proof form system using @SelfProtocol, where you prove you’re human but share zero personal data. 👇
1
0
17