Jan Kopriva
@jk0pr
Followers
692
Following
571
Media
29
Statuses
392
Just one of the infosec crowd.
Between red team and blue team
Joined July 2019
You may find links to new content I've published on https://t.co/mkRumnLeWW at @UntrustedNet.
0
0
0
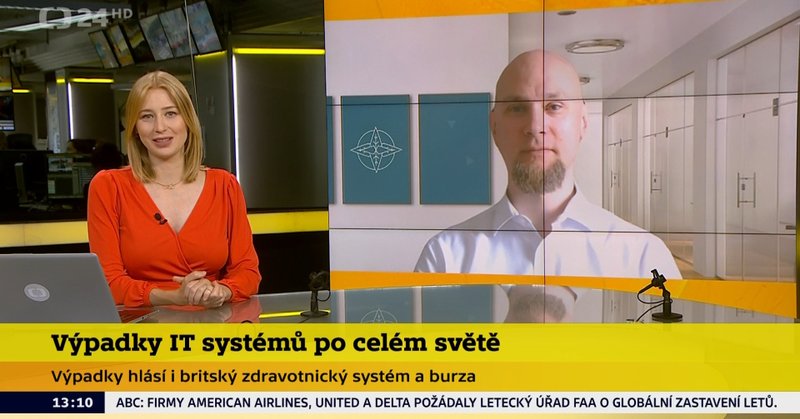
Dnes jsem byl pozván do vysílání odpoledního Studia ČT 24, kde jsem odpovídal na otázky spojené s aktuálními výpadky spojenými s chybnou aktualizací pro senzory CrowdStrike Falcon pro Windows... https://t.co/rF7GFHceXB
untrustednetwork.net
Dnes jsem byl pozván do vysílání odpoledního Studia ČT 24, kde jsem odpovídal na otázky spojené s aktuálními výpadky spojenými s chybnou aktualizací pro senzory CrowdStrike Falcon pro Windows, v...
1
1
1
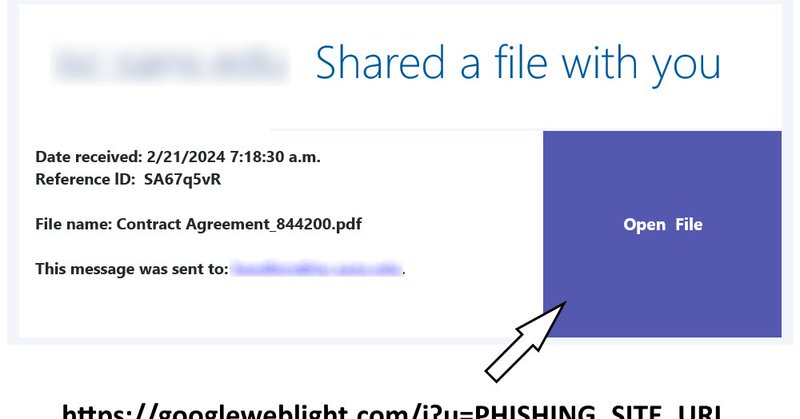
Few weeks ago, I came across a somewhat unusual phishing message that used a slight twist on the "reply-chain" theme to make it through e-mail filters. It is not new, but since I didn't find any write-ups of it anywhere, I wrote a short article, which you may find bellow...
0
0
2
It appears that the number of ICS accessible from the internet has risen by 30 thousand over 3 years
0
5
6
It occurred to me that the current situation surrounding the xz-utils backdoor might present a good opportunity for a quick analysis to see if national or governmental CSIRTs/their host organizations/similar entities publish security advisories during holidays...
0
0
2
An open redirect vulnerability exists in what remains of the Google Web Light service, and it is being actively exploited by threat actors in multiple phishing campaigns... #phishing #Google #vulnerable
https://t.co/JzdNQusSPN
untrustednetwork.net
An open redirect vulnerability exists in the remains of Google Web Light service, which is being actively exploited in multiple phishing campaigns. Google decided not to fix it, so it might be...
0
2
1
Threat actors generally like to use legitimate third-party online services to host malicious content, since it makes their job significantly easier. And - unfortunately - even the Internet Archive is no exception in this regard...
Phishing pages hosted on https://t.co/PlDWCzNEma
0
0
0
Computer viruses are celebrating their 40th birthday (well, 54th, really)
0
9
14
The smallest and largest #malware samples that were "caught" by my e-mail trap in 2023 were a small (<2 kB) VBScript file and a very large (350 MB) EXE... And what might come as a surprise is, that these two samples were pretty much functionally identical.
isc.sans.edu
Interesting large and small malspam attachments from 2023, Author: Jan Kopriva
0
0
3
Phishing page with trivial anti-analysis features
0
3
2
Co se stalo v září?🤔 Novinkami a událostmi z kyberprostoru vás tradičně provedou @StanleyNovo a @jk0pr. Tentokrát se věnovali novinkám, jako: 👉Ransomware Útok na MGM a Caesars 👉Severokorejští Hackeři a Kyberloupež 👉Čína vs USA 👉Microsoftu Unikly Desítky TB Dat
0
1
2
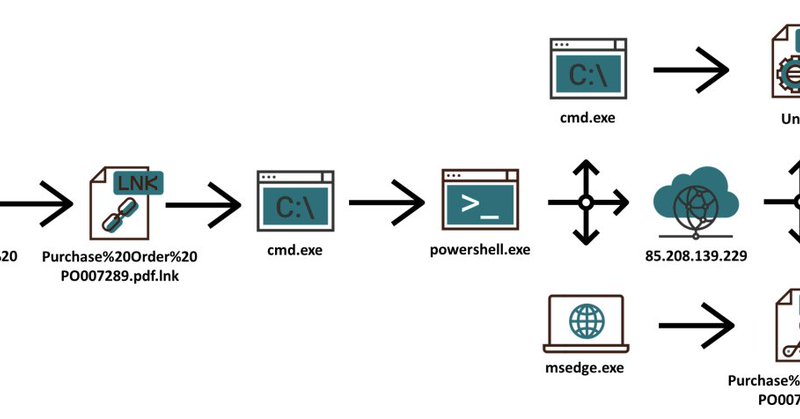
One doesn't often find malware with 0 detections on VirusTotal, especially if it isn't completely new... Nevertheless, it seems I was “lucky” - a malicious batch file, which was used in a last week's phishing campaign I came across is still at zero… https://t.co/dUDYI2DTj1
isc.sans.edu
From small LNK to large malicious BAT file with zero VT score, Author: Jan Kopriva
0
4
10
It can be quite surprising to find out what devices accessible from the internet still support SSLv2. It seems that in Kazakhstan, where such devices are most common, over 166 thousand SSLv2-enabled devices are last-mile network boxes used by the largest national ISP...
1
1
6
Although SSLv2 is not completely "dead" yet, support for it seems to be dying off at a reasonable rate... Hopefully, this trend will continue in the futre.
After 28 years, SSLv2 is still not gone from the internet... but we're getting there https://t.co/5i8nKjOXWz
0
0
2
I’m looking forward to this very much - if everything goes well, it should be a fun, relaxing talk for the attendees, even though we’re going to be talking about security… :)
🎯 Jan Kopriva is going to change the way you think about modeling threats, #secure #softwaredevelopment and analogies with small children or pets. Don't miss his ignite talk at #DevOpsDays Prague! #DevOps #SRE #cybersecurity #modelingthreats
0
0
3
I came across a Facebook phishing campaign recently, which turned out to be quite interesting - one unusual aspect of it was that due to an incorrectly set "From" field, it appeared as if the sender didn't have an e-mail address...
Ongoing Facebook phishing campaign without a sender and (almost) without links https://t.co/IAHlY2Z0LJ
0
2
4