johds
@j_o_h_d_s
Followers
24
Following
195
Media
9
Statuses
28
RT @sysdream: 🔍 Que cache un domaine comme chippotle-sso[.]com ?.L’équipe CTI de SysDream a enquêté sur le groupe Scattered Spider : usurpa….
0
1
0
APT38 (Bluenoroff) infrastructure. #Bluenoroff #apt38 #threatintel #shodan #lazarus. 🔎 ssl.jarm:3fd21b20d00000021c43d21b21b43d76e1f79b8645e08ae7fa8f07eb5e4202 org:"Hostwinds Seattle"
0
1
5
on #FOFA
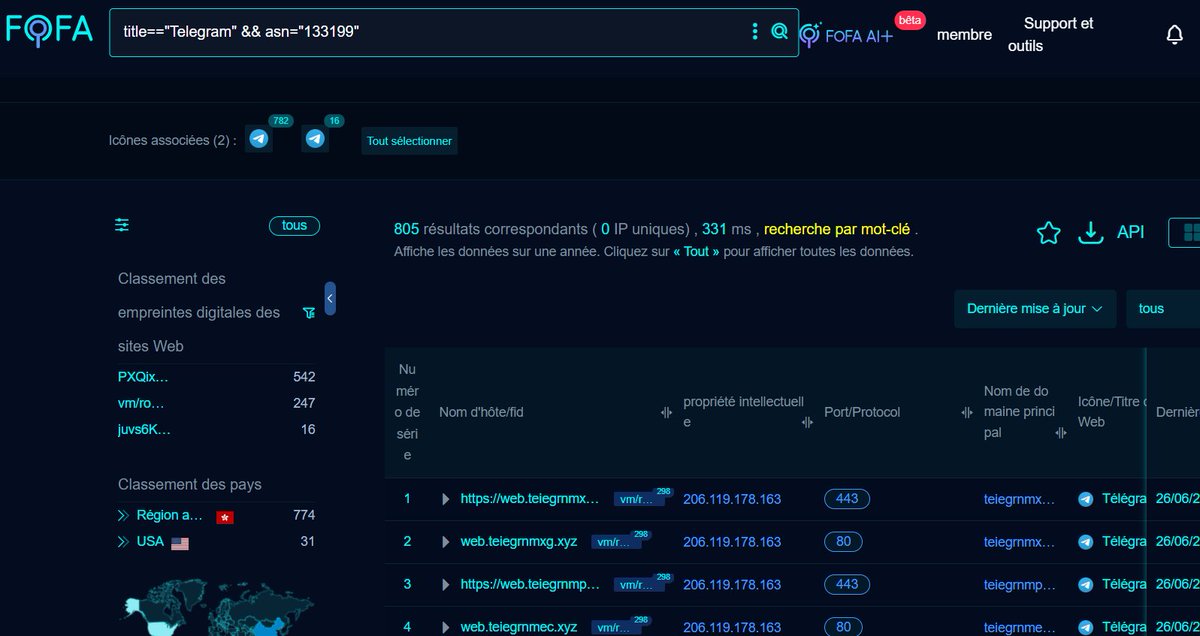
This one is nice. Hard work to find it haha. 🔎 title:"telegram" country:"HK" Server: nginx. ☣️ telegram credentials theft. ♟️ impersonating telegram + hijacking users + Domain Generation Algorithms (DGA). #telegram #hijack #threatintel #shodan
0
0
1
This one is nice. Hard work to find it haha. 🔎 title:"telegram" country:"HK" Server: nginx. ☣️ telegram credentials theft. ♟️ impersonating telegram + hijacking users + Domain Generation Algorithms (DGA). #telegram #hijack #threatintel #shodan
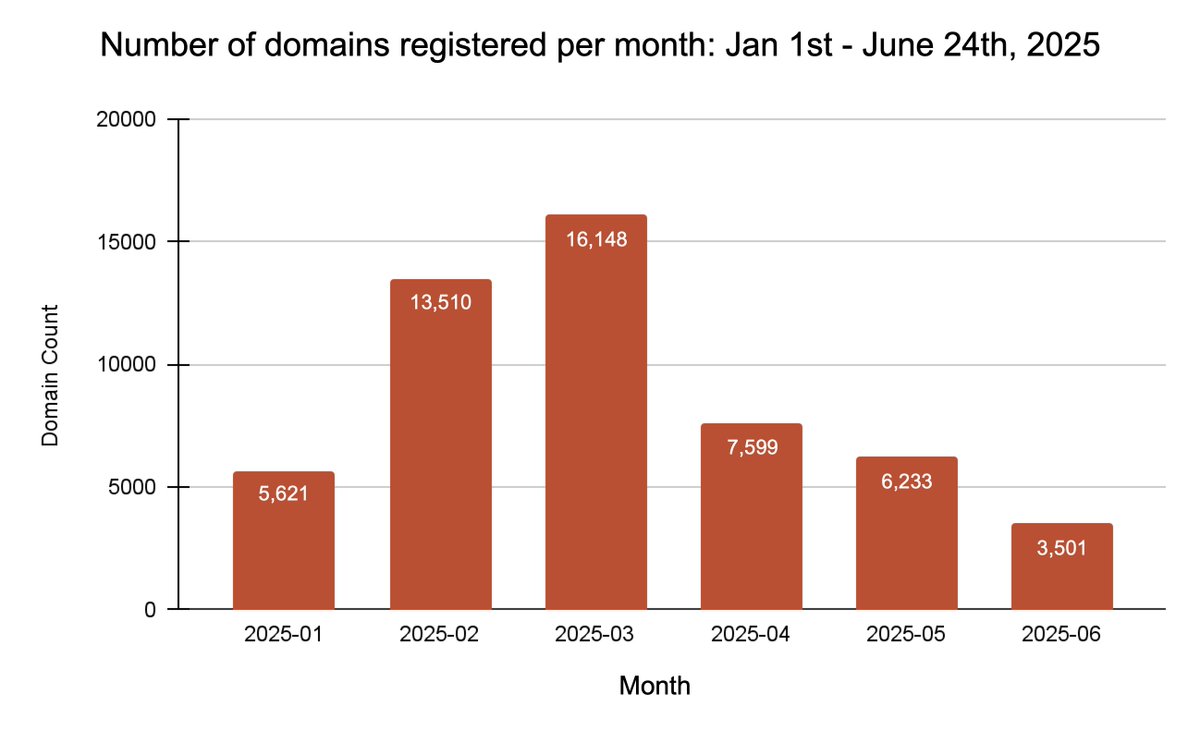
We discovered 54K+ domains in a #phishing campaign hosting sites that impersonate Telegram. These pages steal user-submitted login credentials and one-time passcodes (OTPs) to hijack user accounts. Details at
0
0
0
🔎 shodan : http.html_hash:-51903740. ☣️ Broomstick C2 actively exploiting Oyster backdoor . ♟️SEO poisoning + SEO poisoning + DLL sideloading + Scheduled task + Web C2 + Credential keylogging + SSH access + Data encryption . #ThreatIntel #backdoor #Broomstick #Rhysida #C2
Low detection pre-ransomware.Signed "TOLEDO SOFTWARE LLC". C2: 45.86.230.77, 185.208.158.119, 85.239.52.99. VT: 3d6da75764c043cd2ceb7b35028ec79b. https[:]//bazaar.abuse.ch/browse.php?search=serial_number:33000373da29c35a6ac0484d690000000373da
1
5
8
here it is : http.component:"microsoft httpapi" port:3389,5985 FQDN: WIN-F6NF7R6I6PJ country:"PL" org:"MEVSPACE sp. z o.o.". AsyncRAT (now)/Radhamentys (before) ecosystem
SONGIJIANGFLEX SRL pedido 2303003_docx.6df2615924c8a53a41c958261e216a94. C2: 95[.]214[.]54[.]172:7703.AS201814 MEVSPACE sp. z o.o. 🇵🇱. 👇. #malware @JAMESWT_WT @CERT_Polska
0
2
2
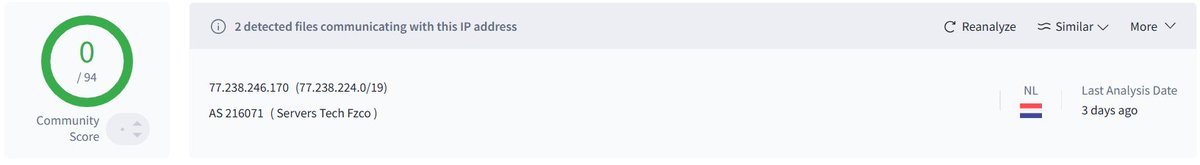
city:"Amsterdam" org:"SERVERS TECH FZCO" asn:"AS216071" os:"Windows Server 2012 R2 Standard 9600"
495ed385329324b54a62ae90da06654e.blog[.]tequide[.]com/lifeisgood[.]zip. C2: 77[.]238[.]246[.]170.AS216071 Servers Tech Fzco 🇳🇱. #NetSupportRat #c2 @JAMESWT_WT @500mk500
0
2
2
"HTTP/1.1 302 Moved Temporarily Server: playit-cloud Location: https://playit[.gg". njrat/quasar already seen using playit/.gg servers
0
0
0
More here after pivoting on censys,.77[.]91.78.192 (6/89).78[.]46.200.68 (5/89).85[.]209.11.185(15/89).91[.]103.252.217 (11/89).95[.]215.108.29 (6/89).#qakbot #Qbot #ThreatIntel .
search.censys.io
Censys helps organizations, individuals, and researchers find and monitor every server on the Internet to reduce exposure and improve security.
An embedded configuration EPOCH timestamp indicates the payload was generated on December 11. The campaign code was tchk06. Most notably, the delivered Qakbot payload was configured with the previously unseen version 0x500. Observed Qakbot C2:.45[.]138.74.191.65[.]108.218.24.
0
0
0
Identified additional IP addresses sharing characteristics with the campaign IP, including the use of OpenSSH version 7.4, belonging to the same autonomous system (ASN 399629), and listening on port 22. The complete list can be found here.
search.censys.io
Censys helps organizations, individuals, and researchers find and monitor every server on the Internet to reduce exposure and improve security.
#APT #Donot.Application to Consulate General.doc.URL: hxxp://speedrugg[.]info/ZKlVWfynYHjd1nm7/aXFwQpdVsYmKbkoWi9y9ZBzIkFE6GHxv0ePSSilV3Ai6F2Ir.(ico|png|mp3|mp4). Jaca sample (PE32+).C2: trigershop[.]info
0
0
0
I find this #C2 #Redline #Stealer 213.248[.]43[.]54 (1/88) on MalwareBazar and I have discovered two more from the same infrastructure by pivoting around the name, ASN number, and OS. New C2 :.213.248[.]43[.]53 (1/88).213.248[.]43[.]60 (1/88). #OSINT #ThreatIntelligence
0
0
0