Hunt.io
@Huntio
Followers
3K
Following
157
Media
46
Statuses
697
https://t.co/9I6nRUiFjm is a service that provides threat intelligence data about observed network scanning and cyber attacks.
United States
Joined June 2023
🔥 Our new eBook is out: Modern Threat Hunting - 10 Practical Steps to Outsmart Adversaries. IOC pivots, SSH key tracking, ASN abuse, C2 clustering, all backed by real examples and HuntSQL™ queries. Grab your free copy 👇. #ThreatHunting #CyberSecurity.
hunt.io
Download our free eBook and learn how to uncover adversary infrastructure at scale in 10 practical, repeatable steps.
0
18
55
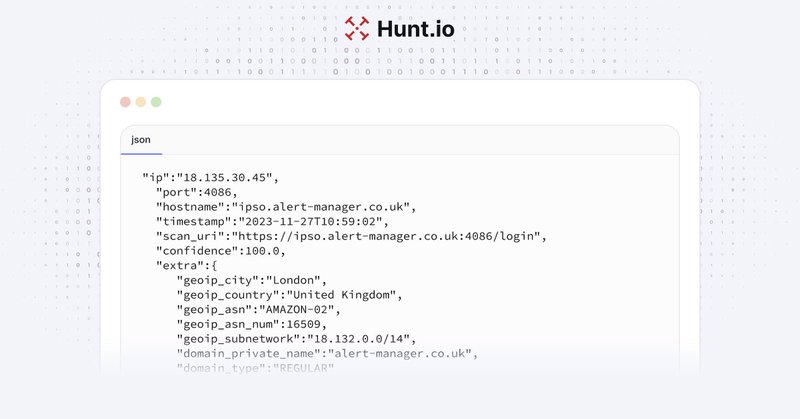
🔍 Monitor Active Malware Infrastructure with Hunt’s C2 Feed API. . C2 servers are the backbone of attacker operations, used to control infected systems, exfiltrate data, and deploy payloads. Our C2 Feed API gives you real-time, high-confidence.
hunt.io
Enhance your cyber intelligence with Hunt.io's Cyber Threat Enrichment API. Access high-confidence C2 feeds and streamline your threat intelligence today
0
0
1
⚠️ WinRAR Zero-Day (CVE-2025-8088) Actively Exploited by Russian-Linked Group RomCom. A critical directory traversal vulnerability in WinRAR (versions before 7.13) is being weaponized by the RomCom group (also known as Storm-0978). Exploits disguise.
infosecurity-magazine.com
A flaw in WinRAR, tracked as CVE-2025-8088, has been exploited by the RomCom group to deploy malware
0
2
8
🚩 Researchers Discover XZ Utils Backdoor Still Hiding in Docker Hub Images. Binarly recently revealed that 35 Docker images, many based on Debian, still contain the #XZUtils backdoor (CVE‑2024‑3094) that was inserted into versions 5.6.0 and 5.6.1 in.
thehackernews.com
Researchers found 35 Docker Hub images, including Debian builds, still carrying the XZ Utils backdoor a year later, highlighting supply chain risks.
0
6
7
Threat hunting in action with Hunt. We uncovered a deceptive malware campaign aimed at Chinese‑speaking users, distributing backdoored installers for Signal, Line, Gmail, and BitBrowser via fake download pages. Domains such as z1.xiaowu[.]pw,.
hunt.io
Read how attackers distribute backdoored Signal, Line, and Gmail installers through fraudulent download pages and how to defend against this campaign.
0
4
19
🚩 Critical WordPress Plugin Vulnerability Affects 70K Sites. A PHP Object Injection flaw (CVE‑2025‑7384) in the “Database for Contact Form 7, WPForms, Elementor Forms” plugin allows unauthenticated attackers to inject PHP objects. With #ContactForm7.
searchenginejournal.com
WordPress vulnerability affecting up to 70,000 websites using contact form submissions database plugin.
0
2
7
RT @BleepinComputer: ERMAC Android malware source code leak exposes banking trojan infrastructure - @billtoulas. ht….
bleepingcomputer.com
The source code for version 3 of the ERMAC Android banking trojan has been leaked online, exposing the internals of the malware-as-a-service platform and the operator's infrastructure.
0
12
0
🧭 Why a Structured Threat Hunting Framework Elevates Cyber Defense. A Threat Hunting Framework isn't just bureaucracy, it’s the engine turning intuition into strategy. It sharpens investigations, improves consistency, and evolves with each hunt, helping.
hunt.io
Learn what a threat hunting framework is and explore essential strategies, components, and best practices for building a powerful and effective threat hunting framework
0
9
36
🚩 SocGholish Malware Spread via Ad Tools Delivers Access to LockBit, Evil Corp & Others. Researchers at Silent Push have uncovered a sophisticated campaign where the #SocGholish malware, known for fake browser-update lures, is now being distributed.
thehackernews.com
SocGholish malware spreads via fake updates, impacting major threat actors through TDS systems and JavaScript loaders.
0
6
12
Attackers move fast, hide well, and blend into the background noise of the internet. . To stay ahead, you need more than static IOCs and generic alerts, you need a repeatable way to discover, map, and track adversary infrastructure before it’s used.
hunt.io
Download our free eBook and learn how to uncover adversary infrastructure at scale in 10 practical, repeatable steps.
0
0
5
🚩 Threat Actors Weaponize Go Packages for Persistent Malware Delivery. Security teams uncovered 11 malicious Go modules, many typosquatting legitimate libraries, embedded with obfuscated code that launches payloads on both Linux and Windows. These.
cybersecuritynews.com
Sophisticated malware hits Go ecosystem via 11 obfuscated packages, delivering payloads to compromise Linux servers & Windows systems.
0
3
6
🚩 Critical “Vault Fault” Flaws in CyberArk & HashiCorp . Expose Secrets Managers.Researchers at Cyata disclosed 14 logic bugs across #CyberArk Conjur and #HashiCorp Vault that enable unauthenticated attackers to bypass authentication, escalate.
thehackernews.com
Vault Fault and ReVault flaws in CyberArk, HashiCorp, and Dell expose systems to takeover risks.
0
2
2
Your data sources should work for you. Our APIs deliver enriched IOCs, live C2 feeds, and open directory intel, direct to your tools. → Integrate once, hunt forever.
hunt.io
Enhance your cyber intelligence with Hunt.io's Cyber Threat Enrichment API. Access high-confidence C2 feeds and streamline your threat intelligence today
0
0
1
⚠️ Threat Actors Abuse Microsoft 365 Direct Send to Send Internal-Style Phishing Emails. . Since May 2025, over 70 organizations have been targeted with phishing campaigns that exploit the Direct Send feature in Exchange Online. This method bypasses SPF,.
cybersecuritynews.com
Hackers exploit Microsoft 365's Direct Send to spoof internal emails, bypassing security and boosting phishing success without credentials.
1
8
15
RT @volrant136: 🚨 #Phishing the Forces: #Sidewinder Targets #SriLanka’s Defence Sector. Using @Huntio, I searched for webpages having POST….
0
9
0
🚩 ClickFix Malware Campaign Exploits CAPTCHA Lures to Spread Cross-Platform Malware. A new #ClickFix variant is evading downloads entirely, now targeting macOS, Android, and iOS through browser redirects and fake shortener pages. On Android/iOS, the.
thehackernews.com
ClickFix malware replaced ClearFake in 2024, infecting users via fake CAPTCHAs and trusted platforms.
0
7
19
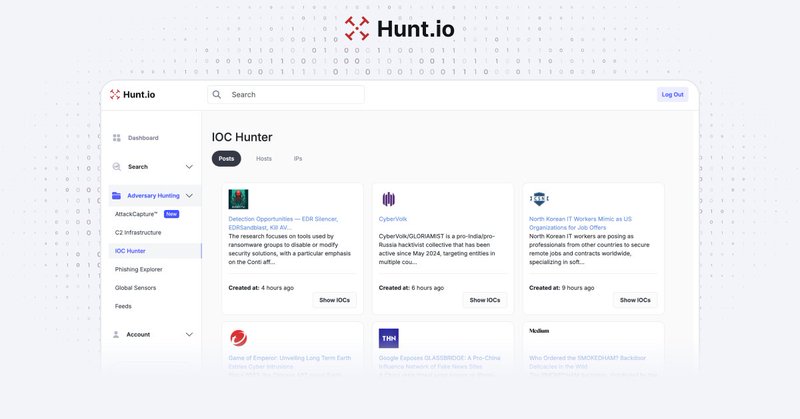
🔍 IOC Hunter As Your Key to Smarter Threat Detection. . Hunt’s IOC Hunter uncovers hidden links between domains, IPs, and certs, processes massive datasets, and delivers context you can act on. From hunting to incident response, get the precision you.
hunt.io
Automate and validate IOCs from top cyber research. Kick-start investigations with Hunt.io's fast, accurate, and expandable IOC Hunter tool. Book your demo today.
0
0
4