Hunt.io
@Huntio
Followers
4K
Following
222
Media
62
Statuses
890
https://t.co/9I6nRUiFjm is a service that provides threat intelligence data about observed network scanning and cyber attacks.
United States
Joined June 2023
🚩 New SAP NetWeaver Bug Lets Attackers Access Sensitive Data and Execute Commands https://t.co/1Acs20Ztbt Researchers report a critical flaw in SAP NetWeaver that can be abused to read sensitive configuration and business data and, in some cases, achieve remote command
securityaffairs.com
SAP addressed 13 new flaws, including a maximum severity vulnerability in SAP NetWeaver, which could lead to arbitrary command execution.
0
6
9
🚩 Threat Actors Abuse Blockchain Smart Contracts to Spread Malware via WordPress Sites https://t.co/4GbzLlm7Ty Threat actor UNC5142 is leveraging smart contracts on public chains (via an “EtherHiding” technique) alongside compromised WordPress sites to distribute
0
2
6
💡 What is The Value of Threat Hunting Playbooks? https://t.co/OBdH8m7zvu For experienced defenders, the challenge isn’t knowing what to hunt; it’s executing hunts consistently, efficiently, and with measurable outcomes. Threat hunting playbooks solve this by providing a
hunt.io
Explore the best threat hunting playbooks built from real operations to speed up detection, improve workflows, and strengthen defense.
0
1
4
@HackingLZ @ex_raritas @Huntio +1 for huntio. Especially after Censys changed its business model to exclude us poors.
1
2
3
🚩 Researchers Expose TA585’s “MonsterV2” Malware Campaign https://t.co/WZviXNnYxG A sophisticated cybercrime actor TA585, has been found running end-to-end phishing campaigns that deliver the high-end “MonsterV2” stealer/RAT/loader, managing its own infrastructure and
infosecurity-magazine.com
A newly identified cybercrime group TA585 is running an advanced cyber operation distributing MonsterV2 malware
0
5
7
⚠️ Two New Windows Zero-Days Exploited in the Wild https://t.co/McHJNHNkOw Microsoft has confirmed two actively exploited zero-day vulnerabilities: CVE-2025-24990 (a privilege escalation in the Agere modem driver present in all Windows versions) and CVE-2025-59230 (an
thehackernews.com
Microsoft’s October 2025 Patch Tuesday fixes 183 flaws, including three exploited zero-days and two 9.9 CVSS bugs.
0
53
168
🎯 𝗙𝗿𝗼𝗺 𝗠𝘂𝗻𝗶𝘁𝗶𝗼𝗻𝘀 𝘁𝗼 𝗠𝗮𝗹𝘄𝗮𝗿𝗲: 𝗝𝗼𝘀𝗲𝗽𝗵 𝗛𝗮𝗿𝗿𝗶𝘀𝗼𝗻 𝗼𝗻 𝗧𝗵𝗿𝗲𝗮𝘁 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 & 𝗗𝗶𝗴𝗶𝘁𝗮𝗹 𝗙𝗼𝗿𝗲𝗻𝘀𝗶𝗰𝘀 From the Air Force munitions field to leading threat detection ops at EY, Joseph Harrison’s journey shows how discipline,
hunt.io
In this interview, Joseph Harrison shares how his Air Force-minted discipline fuels his work in threat detection and digital forensics, and how he leverages Hunt.io’s data (especially JA4) to catch...
0
4
7
#APT #Sidewinder using #New #Exfiltration #Server in Phising Campaign Targeting #Srilanka 1/ @Huntio tracked a new collection server "mailsserver-lk[.]com" in recent sightings in 3 attacks. Observed PDF: WPS NAP 5th Core Steering comm -Meeting Minute.pdf
1
8
14
🚩 North Korean Hackers Merge BeaverTail & OtterCookie into a Single Advanced JS Malware https://t.co/mc5inLhJ6e Researchers at Cisco Talos found a North Korea-aligned actor refining its tool-kit by combining features of the BeaverTail info-stealer and the OtterCookie backdoor
thehackernews.com
OtterCookie v5 merges BeaverTail features with new keylogging and blockchain-based C2 tactics.
0
2
4
⚠️ WatchGuard Fireware Vulnerability Permits Unauthenticated Code Execution (CVE-2025-9242) https://t.co/Mycm9VYD6m A critical out-of-bounds write vulnerability in the Fireware OS iked process allows remote, unauthenticated attackers to execute arbitrary code on Firebox
securityaffairs.com
A critical WatchGuard Fireware vulnerability, tracked as CVE-2025-9242, could allow unauthenticated code execution.
1
2
3
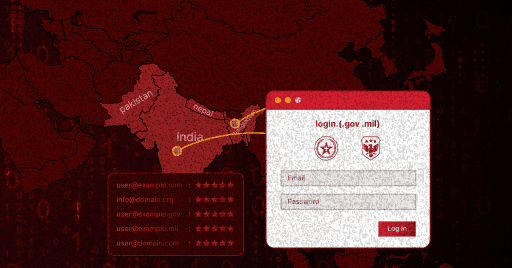
These sites were designed to harvest credentials by mimicking login pages, especially Zimbra webmail panels, and then sent captured data to centralized collection infrastructure such as mailbox3-inbox1-bd[.]com. Read our findings ➡️ https://t.co/H3uDmGmIDA
#ThreatHunting
hunt.io
APT Sidewinder targets South Asian government and military portals using Netlify-hosted phishing pages to harvest credentials. Learn more.
0
1
6
🌐 Two months ago, we uncovered APT Sidewinder’s use of Netlify and Pages[.]dev hosting platforms to deploy phishing portals that impersonated government and defense agencies throughout South Asia. ⬇️ https://t.co/H3uDmGmIDA
#MalwareAnalysis #SecurityResearch
hunt.io
APT Sidewinder targets South Asian government and military portals using Netlify-hosted phishing pages to harvest credentials. Learn more.
2
10
35
Each directory listing reveals the malware type, file count, country, size, and hosting provider. From there, researchers can pivot deeper, analyzing associated MITRE ATT&CK techniques or identifying related malware families like Meterpreter or Bulz. See how Hunt detects live
hunt.io
Book your free Threat Hunting platform demo with Hunt today. Help your security team expose attackers, find C2 servers, IOCs, and malware in directories.
0
0
2
📌 𝗙𝗶𝗻𝗱𝗶𝗻𝗴 𝗖𝗼𝗯𝗮𝗹𝘁 𝗦𝘁𝗿𝗶𝗸𝗲 𝗶𝗻 𝘁𝗵𝗲 𝗪𝗶𝗹𝗱 𝘄𝗶𝘁𝗵 𝗔𝘁𝘁𝗮𝗰𝗸𝗖𝗮𝗽𝘁𝘂𝗿𝗲™ Hunt’s AttackCapture™ feature continuously monitors open directories to identify active malware infrastructure. Using advanced signature detection and tagging, it flags Cobalt
1
7
17
🚩 New .NET “CAPI Backdoor” Targets Russian Auto & E-Commerce Firms via Phishing ZIPs https://t.co/2EylQ7OuL7 Security researchers at Seqrite Labs uncovered a novel backdoor written in .NET that abuses the Windows Cryptographic API (CAPI) and uses instances of rundll32.exe to
thehackernews.com
Seqrite Labs reveals CAPI Backdoor malware targeting Russian firms via phishing ZIPs and rundll32.exe.
0
4
12
📖 If you’re still relying on static IOCs, you’re missing the real picture. Our free eBook, Modern Threat Hunting, provides a repeatable framework for uncovering adversary infrastructure at scale, utilizing methods such as certificate tracking, IOC pivoting, C2 detection, and
hunt.io
Download our free eBook and learn how to uncover adversary infrastructure at scale in 10 practical, repeatable steps.
0
9
26
You can query by tags, malware names, ports, or host providers and instantly return captures with detailed metadata: file structures, timestamps, confidence scores, and enrichment data. Book a demo and get access to your API ➡️ https://t.co/YJzGDkh8LJ
#ThreatHunting
hunt.io
Book your free Threat Hunting platform demo with Hunt today. Help your security team expose attackers, find C2 servers, IOCs, and malware in directories.
0
0
1
📌 𝗔𝘁𝘁𝗮𝗰𝗸𝗖𝗮𝗽𝘁𝘂𝗿𝗲™ 𝗟𝗶𝘀𝘁𝗶𝗻𝗴 𝗔𝗣𝗜 𝗘𝗻𝗱𝗽𝗼𝗶𝗻𝘁 𝗧𝗼 𝗙𝗶𝗹𝘁𝗲𝗿 𝗪𝗵𝗮𝘁 𝗠𝗮𝘁𝘁𝗲𝗿𝘀 When investigating, context is everything. The AttackCapture™ Listing endpoint lets you filter Hunt’s dataset to find exactly what you’re looking for - malware
1
1
3
⚠️ Chinese Threat Actors Exploit ArcGIS Server Zero-Day for Geo-Spatial Data Theft https://t.co/bQu1Z8H4Oy Nation-state actors have been exploiting a critical vulnerability in ArcGIS Server to gain remote code execution and extract sensitive infrastructure-mapping data used for
thehackernews.com
Chinese hackers used a modified ArcGIS server to maintain hidden access for over a year.
0
12
27