Hiren Sadhwani
@hir3n_s
Followers
253
Following
10K
Media
49
Statuses
789
Threat Hunter | #ThreatHunting | #DFIR | #ThreatIntelligence
Joined May 2018
🎤 Thrilled to have spoken at the SANS #RansomwareSummit 2025! Big thanks to @rj_chap & @maridegrazia for hosting, @MindsEyeCCF for the awesome graphic recording, and all the attendees for being a fantastic audience! Grateful to the @sansforensics team for the opportunity.
1
1
6
So, these threat actors successfully phished an author of multiple open source NPM packages with a total of 2 billion weekly downloads – including debug, chalk, and ansi-styles. Since most companies run at least one React or Angular app, they had the opportunity to execute code
19
119
595
ICYMI: Was just perusing the latest CrowdStrike 2025 Threat Hunting report ( https://t.co/B4t726AnSJ) and check this wild timeline for Scattered Spider - from account takeover to Entra ID bulk user export in <5 minutes 👀
5
75
225
Thoughts on LLMs writing detection rules, and why I’m not impressed: LLMs are good at one thing – predicting the next most plausible word in a sentence. That’s why most AI-generated detection rules are only good at one thing as well: looking plausible. On first glance they seem
21
58
278
#HuntingTipOfTheDay: you know how to spot/decode Base64 or XOR in PowerShell… but what about SecureString? This AES-based encryption is native to PowerShell; attackers have been seen to use this for PowerShell obfuscation. 🔍 Hunt for known SecureString decoding commands
0
20
99
My talk at SANS #RansomwareSummit 2025 is officially uploaded now on YT https://t.co/C8nrH0TbEj
🎤 Thrilled to have spoken at the SANS #RansomwareSummit 2025! Big thanks to @rj_chap & @maridegrazia for hosting, @MindsEyeCCF for the awesome graphic recording, and all the attendees for being a fantastic audience! Grateful to the @sansforensics team for the opportunity.
0
2
5
OSINT tool that can allow you to have a good opsec https://t.co/KXK0UHnnPc Dangling accounts can lead to you being exposed. What is your favorite tools that are similiar to this one?
3
20
114
A teammate of mine worked on an interesting incident where the attackers connected to the backup server via RDP, launched the Chrome browser, and searched on Google for "VirtualBox". The VirtualBox installer was then downloaded to the home directory of the compromised user:
17
43
360
#PakistanStabsIran The famous unprecedented lunch between POTUS & Munir on 18 June 2025 21 June 2025 #PakistanNominatesTrump for Nobel Peace Prize Here is the move towards Peace 22 June 2025 So, finally #America has joined #IranIsraelConflict Let's wait and watch what is
2
5
23
If I were to start a new job at a company, and if I have one (security-related) wish .. If I could pick anything, I’d ask for a clear naming convention for all computers and servers. Additionally, I’d want DHCP and security logs to be stored centrally in a SIEM system. That way,
12
11
114
"Real Time Detection & Response" - Something happens on the system a log gets generated. (fraction of milliseconds are lost) - An local engine matches on it and generate something to send (a couple more milliseconds / seconds are lost) - Time to send that thing to the other
6
26
165
"But in Q1, we also saw a new social engineering lure where the attackers started using fake website cookie banners to spread malware. A cookie banner, which is required for GDPR compliance, is a pop-up message displayed on a website to inform users about the use of cookies and
3
41
131
Yes, LLMs don’t think. Apple’s paper shows they fail at logic. But they guess so well, they already outperform mediocre white-collar work – junior coding, copywriting, design, even legal boilerplate. The risk isn’t in jobs that require real thinking. It’s in the ones where
5
63
239
Windows SMB Client Elevation of Privilege Vulnerability CVSS Score: 8.8 Attack Vector: Network Attack Complexity: Low Privileges Required: Low User Interaction: None Do I have to say more? https://t.co/SbFqsTWTSN
13
125
414
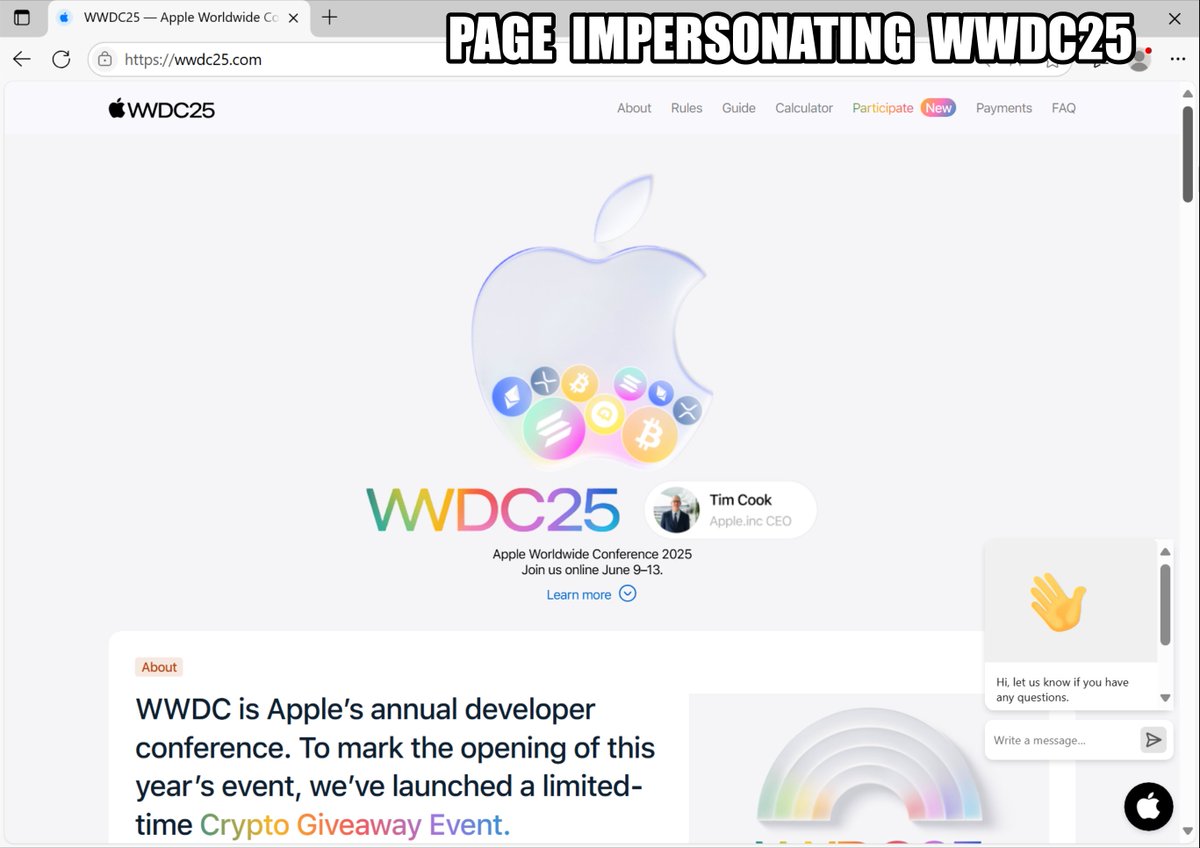
Cybersecurity Alert: Registered on June 7th, wwdc25[.]com hosts a #scam site impersonating the official WWDC25 event. It promotes a fake #cryptocurrency giveaway to steal funds. Do not send any cryptocurrency to the wallet addresses listed! Details at https://t.co/CmEvXoJ2u0
3
16
44
📢 Next up | Hiren Sadhwani is showing how to spot #Malware like Lumma Stealer & Bumblebee before #Ransomware operators get their hands on your network. ➡️ Join FREE online: https://t.co/Q4hlPMuHWQ
#RansomwareSummit #ThreatHunting #DFIR
0
3
15
👉 Hiren Sadhwani shares traditional TTPs like #Phishing & RDP exploits still work, but attackers are getting creative with: ‣ ClickFix / fake CAPTCHAs ▸ Email bombing + MS Teams spoofing ▸ Quishing (QR code phishing) ▸ SEO poisoning #RansomwareSummit #ThreatIntel #DFIR
0
7
15