Guanxing
@hhj4ck
Followers
836
Following
67
Media
9
Statuses
58
A sophisticated scam with a simple trick: capturing seed phrases in person. CertiK’s Guanxing Wen spoke to @WIRED about how social engineering and a single moment of exposure can get your wallet drained. Read more in the article👇 https://t.co/4FTshL9i7Z
wired.com
Sophisticated crypto scams are on the rise. But few of them go to the lengths one bitcoin mining executive experienced earlier this year.
3
15
39
New teardown: took apart an ‘iris-secured’ hardware wallet and found a bootloader issue plus a zero-biometric unlock path. https://t.co/4xLzduQ5OE
5
36
323
A fun journey that started with bypassing Google's Play Integrity and ended with a vulnerability in the @myBraavos "Gasless" mechanism on @Starknet Here’s the full write-up on how it could have been exploited: https://t.co/k4qV3uGDVq
3
3
10
✅ Just wrapped up my deep-dive on exploiting an unfused Qualcomm QCM2150 POS device (BootROM → root). https://t.co/c3TpJvAQHh Flying to Vegas in the morning stress-free for #BHUSA & #DEFCON33. Catch me in the hallways!
1
40
125
Ever wonder what DePIN projects are really doing behind the AI-generated docs and endless hype? I dug into the code, found some wild vulnerabilities, and showed some pretty amazing backend stuff. Slides and demos:
github.com
Contribute to hhj4ck/CrackDePIN development by creating an account on GitHub.
0
1
8
Just wrapped my talk on DePIN security! Huge thanks to Mark, Jimbo, and Dawn from @SummerC0n for an incredible experience, and to the amazing audience! You all rock!
0
0
3
Thrilled to speak at @SummerC0n—America’s oldest hacker con—about the massive DePIN ecosystem. See you in July! 🚀👾
Decentralized Physical Infrastructure Networks (DePIN) are designed to manage and govern physical infrastructure assets in a decentralized manner. And it sounds promising... but there’s a problem. https://t.co/8p5TiVu0Vw
0
0
7
Honoured to join Ledger’s 2025 Hall of Fame (first entry since 2022)! Hardest gadget I’ve ever probed—tough for attackers too. Huge thanks to Vincent (@b0l0k_) and the @DonjonLedger / @Ledger crew for the recognition. https://t.co/yScWiefQe3
3
3
31
#CertiKInsight 🚨 Security is a collective effort, and we appreciate Starknet’s swift response and transparency throughout the process. It's great to see such professionalism in the Web3 space. Read more about the security update here:
community.starknet.io
Ello! Posting a summary by the security team 🙂 Starknet Security Update: potential full node vulnerability At Starknet, we strive to maintain the highest security standards for our ecosystem. On...
5
8
23
Great working together with the @Starknet Their transparency, professionalism, and quick response throughout the process were truly impressive—something rare in the Web3 industry. Glad to contribute to strengthening the ecosystem:
community.starknet.io
Ello! Posting a summary by the security team 🙂 Starknet Security Update: potential full node vulnerability At Starknet, we strive to maintain the highest security standards for our ecosystem. On...
0
0
2
New experience unlocked! Feeling inspired as a long-standing idea in my mind finally gets confirmed. Eagerly awaiting the final report!
The results of the $170,000 Kakarot competitive audit are in! Big congrats to everyone who submitted valid findings, especially to RadiantLabs (@0xEV_om & @3DOCsec) for securing over half of the total prize pool! Much respect to @KakarotZkEvm for their unwavering commitment to
0
2
10
Great research work by @Josep_Pi on reverse engineering and exploiting contactless payment terminals Slides: https://t.co/Q52vhGEfQW YT video: https://t.co/X2hyOF0Y7z
#nfc
6
109
330
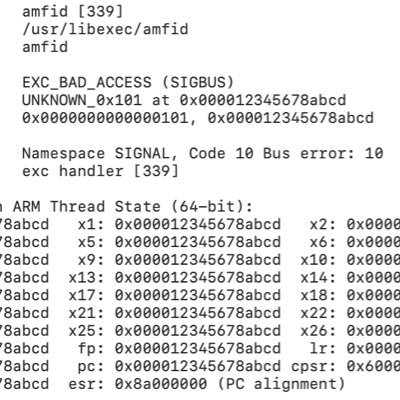
Still interested in exploiting IPC memory corruptions on Apple devices? Try this one: CVE-2024-27801, UAF in the low level implementation of NSXPC that has been present since the initial release of NSXPC (over decade ago). POC:
github.com
Contribute to wangtielei/POCs development by creating an account on GitHub.
1
41
176
The @CertiKSkyfall team identified and collaborated with @Apple to fix a vulnerability (CVE-2024-27801) in the low-level implementation of NSXPC, affecting all Apple platforms. This vulnerability could have potentially allowed malicious apps to gain unauthorized access to
794
927
1K
The slides and demo of my talk "Decrypting Crypto PoS"
github.com
Contribute to hhj4ck/CryptoPoS development by creating an account on GitHub.
0
3
9
CertiK was thrilled to be part of the 2024 @Qualcomm's Product Security Summit today. We demonstrated critical vulnerabilities in Crypto POS systems, highlighting how security can be easily compromised. 🛡️ Check out our Vulnerability 1 & 2 videos to see our findings! 👇
28
26
154
We REPRODUCED one RCE attack to the latest TG Desktop on Windows (release version 4.16.6 x64). All credits go to the original security researchers (github: el-garro) who reported the issue first.
31
29
68
https://t.co/w5ZXs266CU this doesn't have nice pictures to explain things but I think other than that is very good @hal
1
2
1