hextree.io
@hextreeio
Followers
8K
Following
119
Media
60
Statuses
165
🌱 Grow your cybersecurity skills with concise and well-edited video courses - in early-access, sign-up now! Created by @LiveOverflow and @ghidraninja.
Joined March 2021
Our Android courses are out a month now 🎉. These courses aim to teach you everything you need to know to get started with Android Bug Bounty - specifically the Google Mobile VRP.
1
27
168
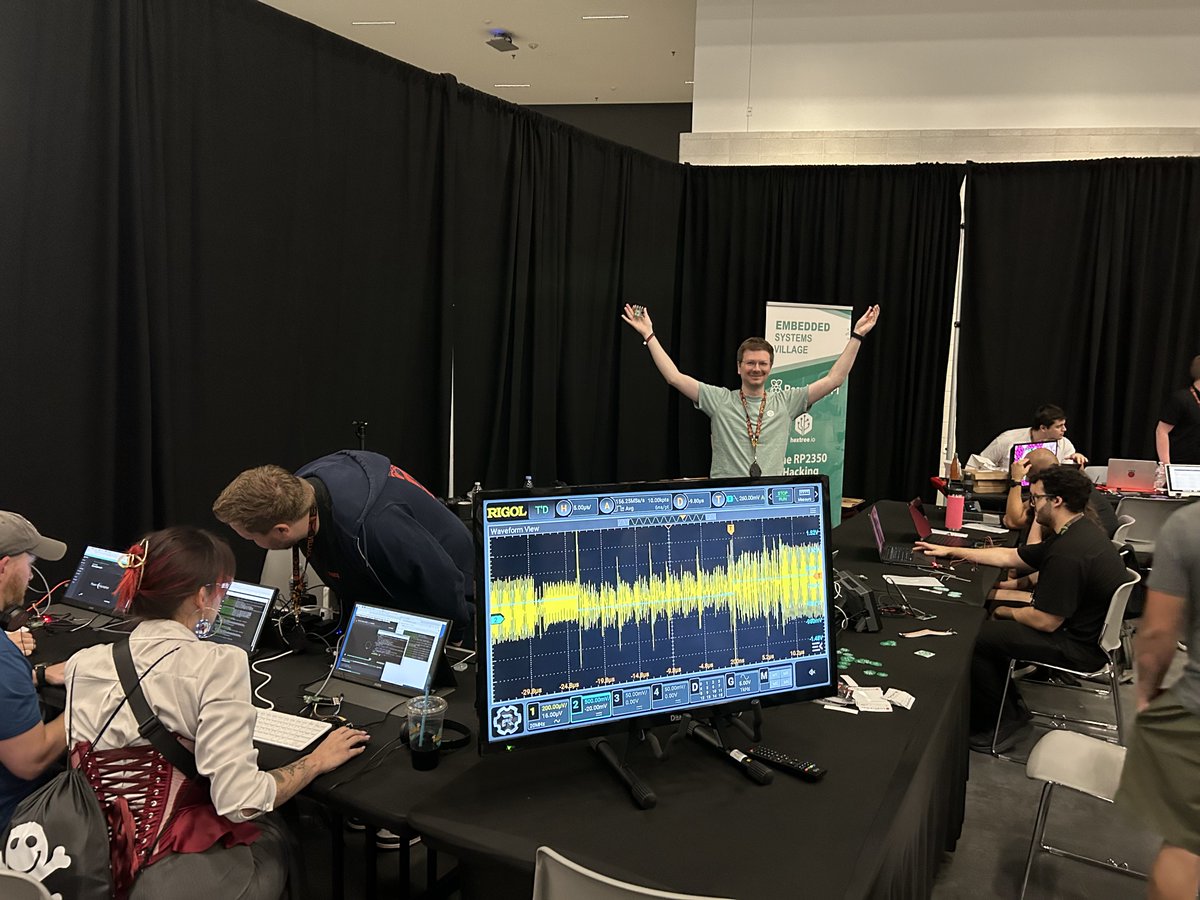
Interested in learning fault-injection?. Visit our glitching lab at DEF CON! We are at the amazing @EmbeddedVillage
1
8
55
The new @Raspberry_Pi RP2350 Hacking Challenge: Second Edition just went live!. The first one was a huge success, with amazing attacks on the OTP secrets!. Now we want to see your side-channel attacks: Can you break the new, hardened AES implementation?.
1
16
61
RT @Raspberry_Pi: A new A4 stepping of our RP2350 microcontroller is now available, with fixes and improvements. Plus: another RP2350 Hac….
0
89
0
Looking to take your first steps in hardware hacking?. @BlueHatIL invited us to bring the magic of bit-flipping & instruction corruption to our own classroom at their conference!. Participation is free for all conference attendees
2
9
68
@Raspberry_Pi If you are interested in taking your first steps with fault-injection, check out our voltage fault-injection content at - with more coming very soon🤠
1
0
27
We would also like to thank @Raspberry_Pi for the great corporation on both the audit as well as the hacking challenge - being this transparent about security is a great step for the microcontroller industry overall.
2
0
29
You can read more about our - but also about the successful attacks by folks such as @nSinusR - in Raspberry Pi's latest blogpost:. Security through transparency: RP2350 Hacking Challenge results are in.
raspberrypi.com
All chips have security vulnerabilities, and most vendors' strategy is not to talk about them. In contrast, we aim to find and fix them.
1
10
56
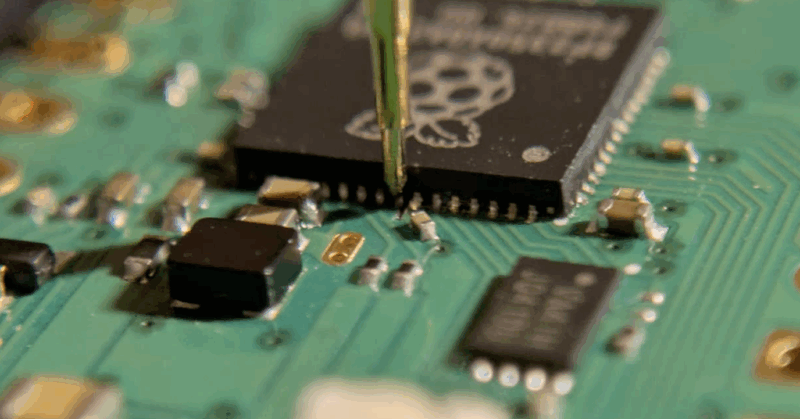
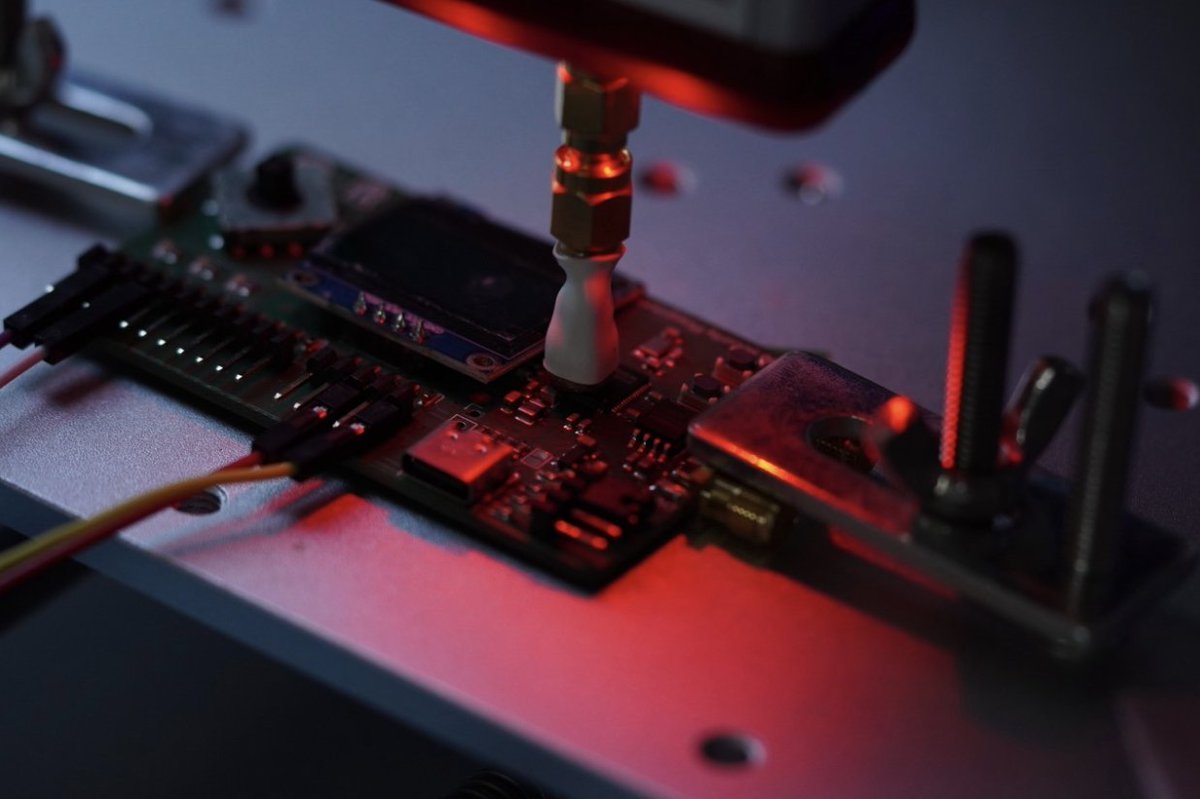
Last year, @Raspberry_Pi hired us to test the security of the RP2350 - and using electro-magnetic fault-injection we were able to successfully bypass the OTP security measures!. This allowed us to read and modify the OTP locks, essentially bypassing the RP2350 secure-boot.
2
59
441
RT @1bitsquared: Hey everyone! We have some great news! The @hextreeio ( aka. @ghidraninja and @LiveOverflow ) Faultier and GlitchTags are….
0
22
0
We have a few seats left at our in-person training at @hardwear_io 2024: Applied Fault Injection 2.0. We've added new targets (including a RISC-V target) & new challenges, and you get FI targets & equipment to take home. Learn how to hack chips with us!.
0
2
23