Explore tweets tagged as #decryption
Nothing bro, just thinking about Ice Spice and Latto's 'Gyatt' video. 🤌▶️
0
0
3
DeCryptions: Greens 15.25 x 22.9cm | 6” x 9” watercolor on paper 2022
0
1
3
just love writing about cryptography with eg (wherever possible) preparing something for Threshold Decryption inside TEEs
3
2
28
Multidimensional Decryption of Metallopolymer at Single-Chain Level https://t.co/PvPMq3KGUy
#chemistry #openaccess #science #chemtwitter
1
9
34
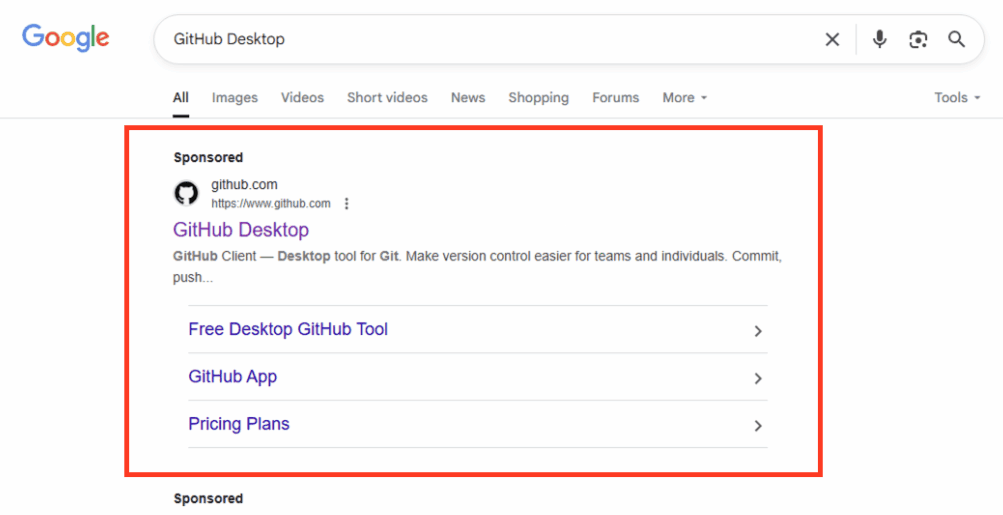
GPUGate malware abuses Google Ads and GitHub to split users to a spoofed download. The 128 MB installer uses GPU-gated decryption to evade sandboxed environments and then gains admin rights. Trust at scale can be weaponized. #CyberSecurity #GPUGate #Malware #ThreatIntel
0
0
4
New blog on #Sinobi ransomware! They used an MSP's compromised SonicWall SSL VPN creds for initial access. Decryption is impossible w/o the attacker's private key, unless of course you hooked CryptGenRandom😜 https://t.co/fHphAm8ldy
4
57
162
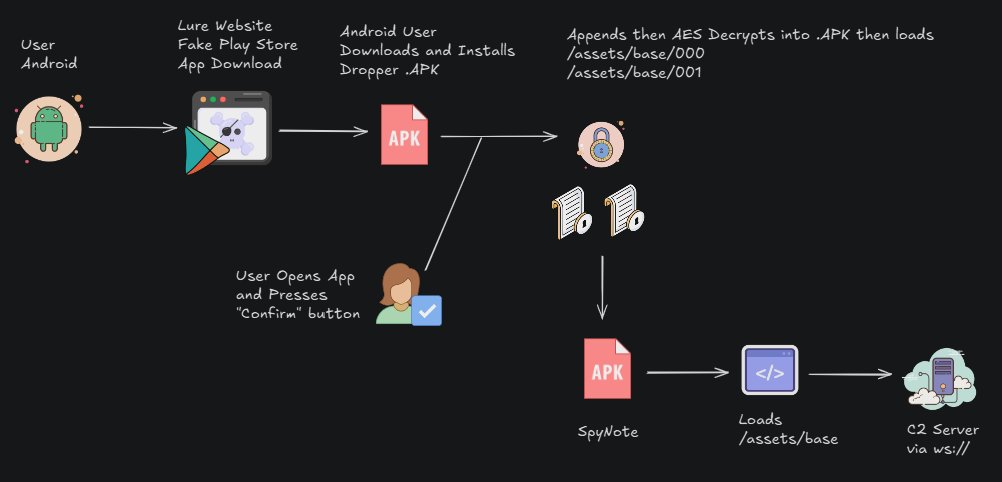
A new #SpyNote report is out! 🚨 Dive into the tactics of this Android RAT campaign, from dynamic payload decryption to new obfuscation methods. Learn how threat actors are using deceptive Google Play Store clones to target users https://t.co/XmxKAgUAHV
0
7
22
.@zama_fhe is making encrypted data handling as simple as sending a meme. No decryption stress, only confidential computing. It’s like a secret dinner party where everyone’s invited but no one spills the beans. @cryptoverse_ @defiprivacy @FogoChain @GiveRep
1
0
4
Processing without borders, and without the chargeback cost. Curious how it works in practice? Let’s talk. Initiate Decryption. #C13VER13E #fintech #web3payments #chargebacks #cryptoprocessing #blockchain #globalbusiness #onchain
0
0
2
Bootloader vulnerability and firmware decryption in TP-Link (Tapo) C210 cloud cameras https://t.co/jUb9a1NTpd Credits @Watchful_IP
#embedded #infosec
3
86
378
Diving deeper into the @anoma stack lately, and I have to say - I haven’t been this bullish in a long time Here’s what’s lining up: 1) Intentnet + solver-based matching 2) Threshold decryption + ZK privacy 3) DA retention incentives 4) NAM + XAN fueling the app layer
1
0
2
@Decrypting_xyz | $DCRYPT Decryption goes beyond breaking codes—it's a mindset. It’s about stripping away distractions, noise, and deception to uncover truth. In a world flooded with information, hype, and superficial signals, real value hides beneath complexity. Decrypting
2
1
2
The #GPUGate malware, distributed via GitHub and Google Ads, uses GPU encryption. Targets users in Western Europe. #GPUGate @AWNetworks
https://t.co/GnwddGlP2A
4
13
56