Explore tweets tagged as #VShell
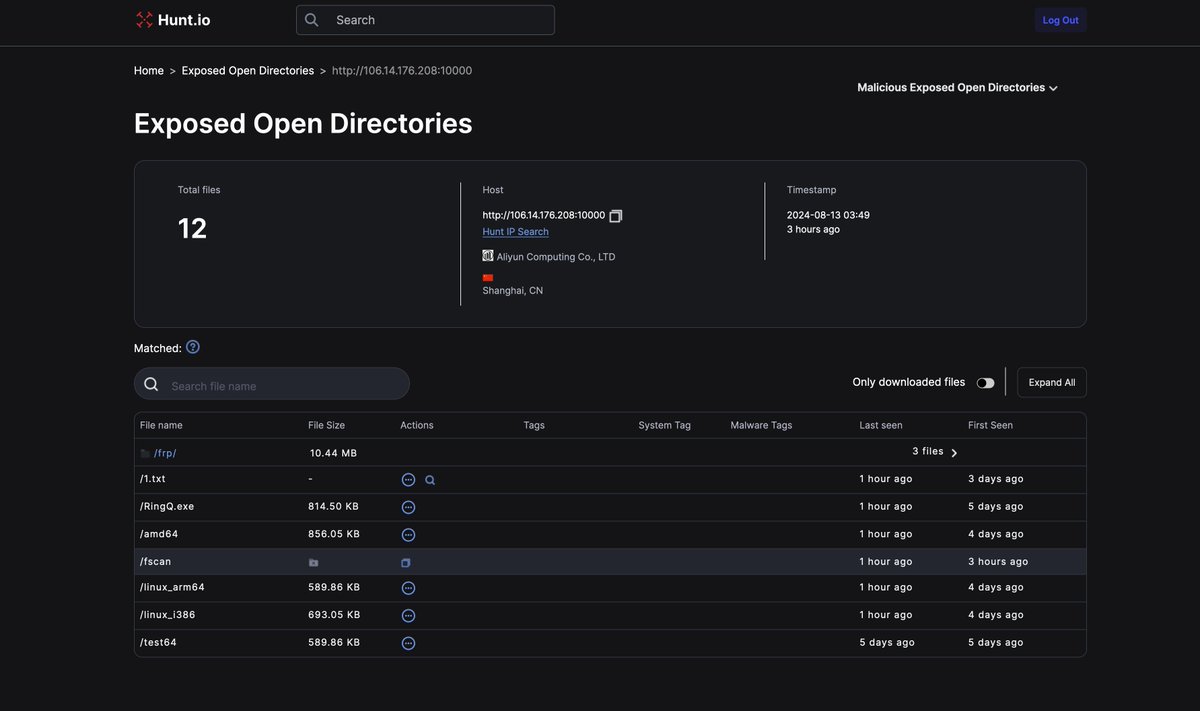
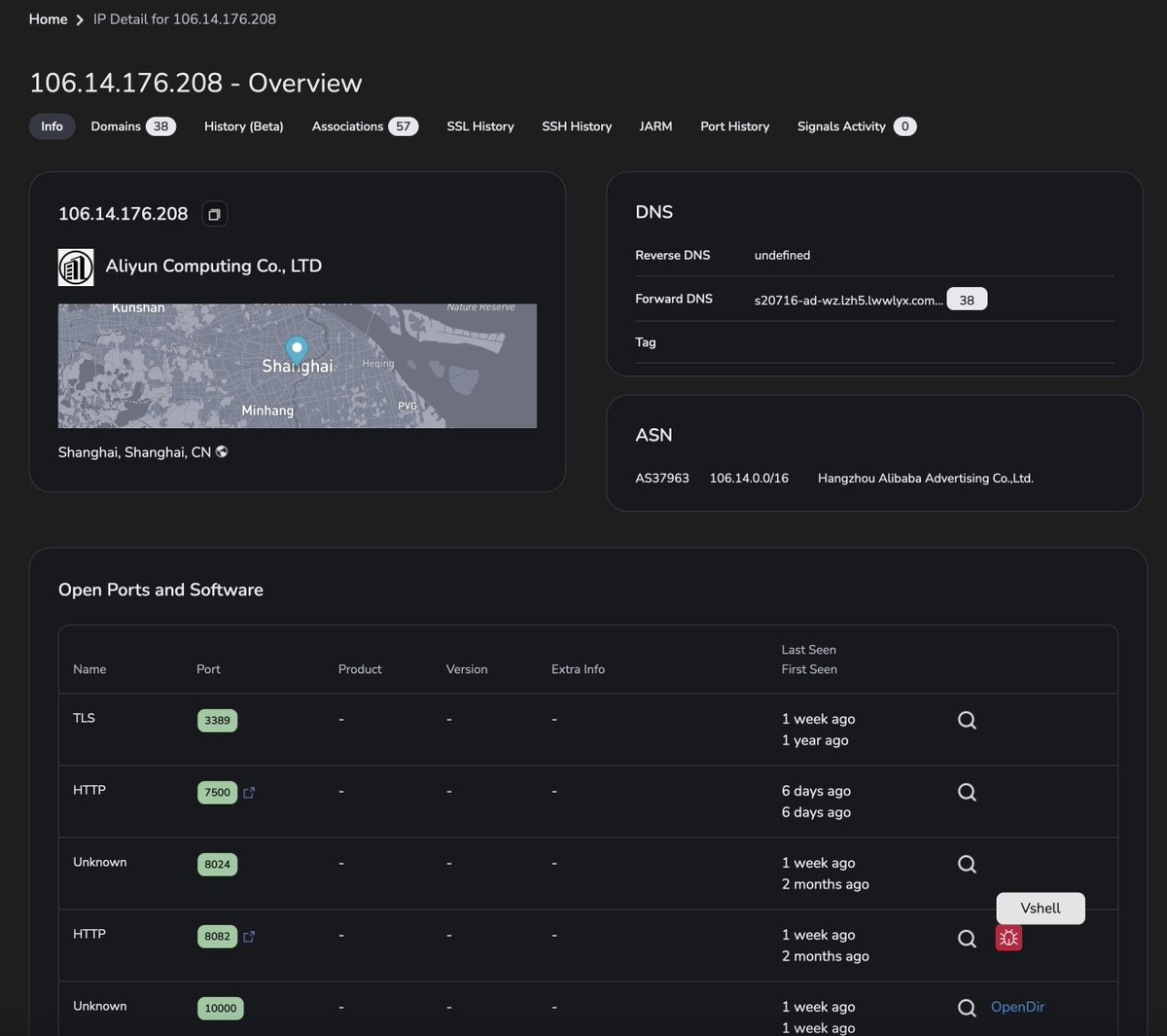
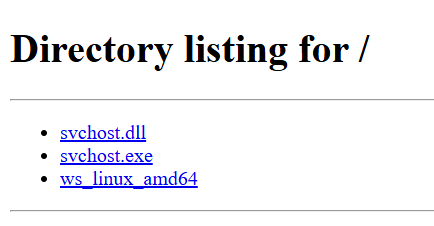
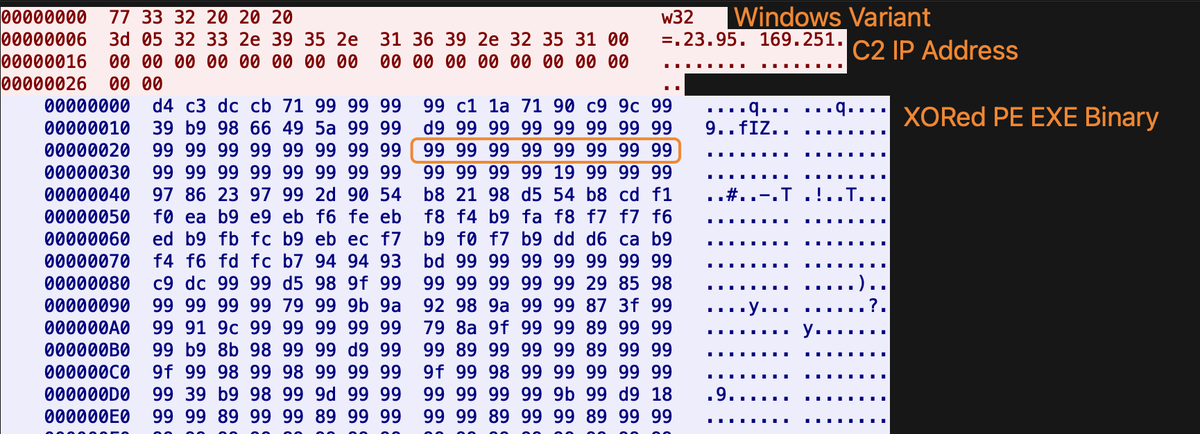
#opendir 106.14.176.]208. Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic. RingQ, an open-source Windows shellcode generator, is also present. A week ago, Vshell was also detected on this IP on port 8082.
3
8
33
▪ http://148.135.120[.]162:8443/
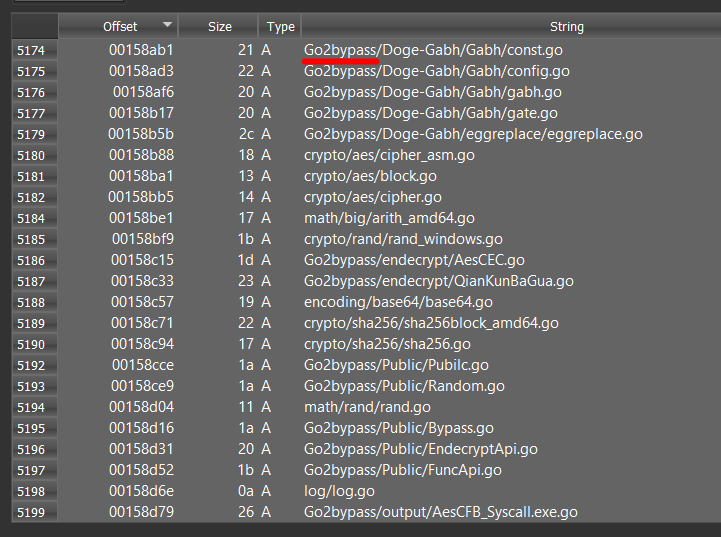
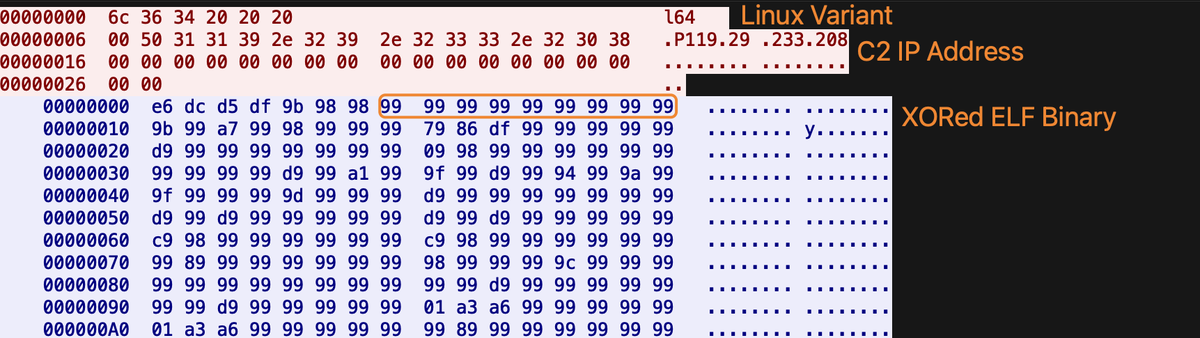
#opendir with Go2bypass and something else 🤔. 🔸 "svchost.exe": 28e318a9ed1580a14ef9b6a71d6a0ec5031aae9d2b748b2ed70c67cfa24a85b4 (Go2bypass).🔸 "ws_linux_amd64": 6ce0e2df1698a965627bd7afa2cf58a86cdb3cc691a150b0ad0e19eaa49c0481 (VShell?).🔸
1
7
27
#threatreport #LowCompleteness.Hunting China-Nexus Threat Actor | 13-07-2025.Source: Key details below ↓. 🧑💻Actors/Campaigns:.Earth_alux.Dragonclone. 💀Threats:.Cobalt_strike_tool, Vshell, Supershell, Havoc, Sliver_c2_tool, Brc4_tool, .🏭Industry: Telco,
0
0
0
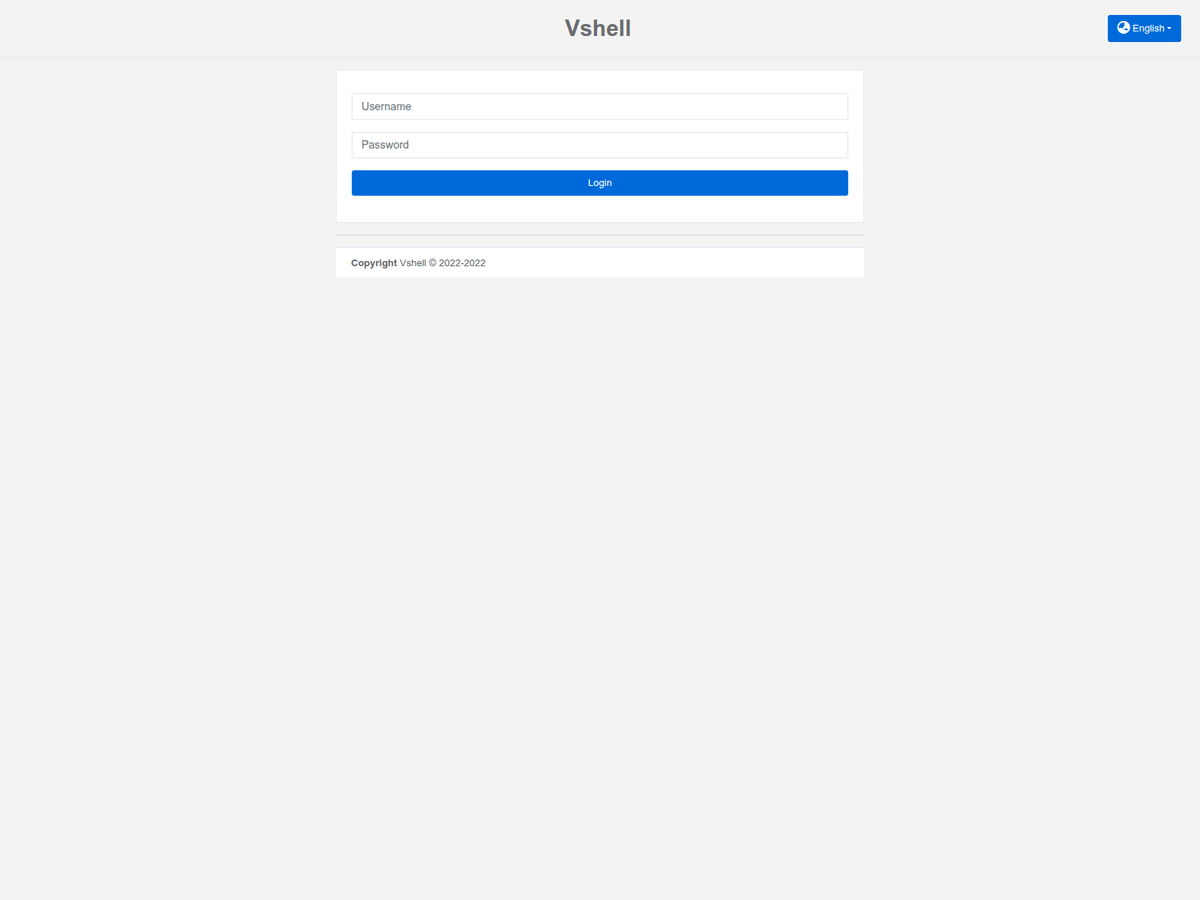
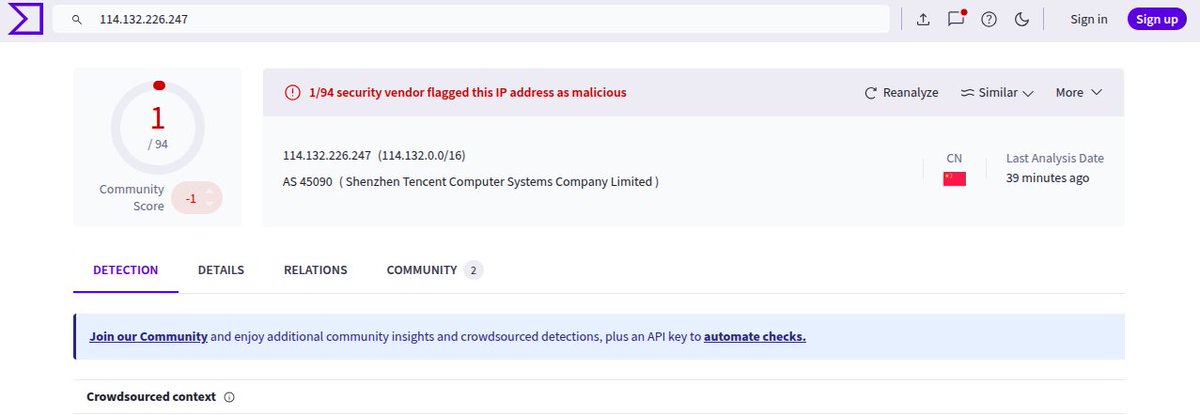
👹 Vshell web panel . IP : 114.132.226[.]247 .AS 45090( Shenzhen Tencent Computer Systems Company Limited ). Low detection on @virustotal . more Vshell panels detected by #C2Watcher on
1
0
1
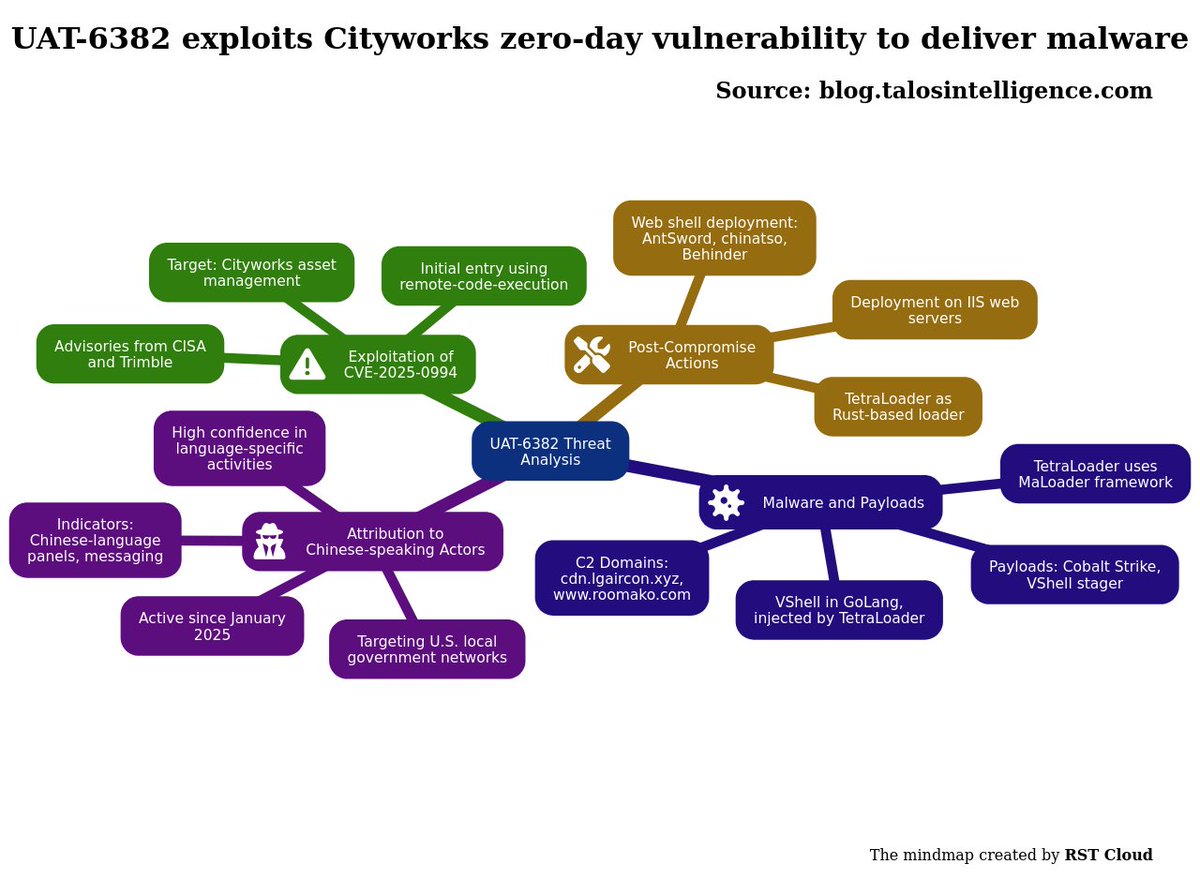
#threatreport #MediumCompleteness.UAT-6382 exploits Cityworks zero-day vulnerability to deliver malware | 22-05-2025.Source: Key details below ↓. 🧑💻Actors/Campaigns:.Uat-6382. 💀Threats:.Antsword, Chinachopper, Cobalt_strike_tool, Vshell, Tetraloader,
0
0
1
JPCERT/CC details a sophisticated, ongoing malware campaign exploiting Ivanti Connect Secure (CVE-2025-0282, -22457) using MDifyLoader, Cobalt Strike, vshell, and Fscan for stealthy persistent access. #IvantiHack #Cybersecurity #MalwareCampaign #APTAttack.
0
3
10
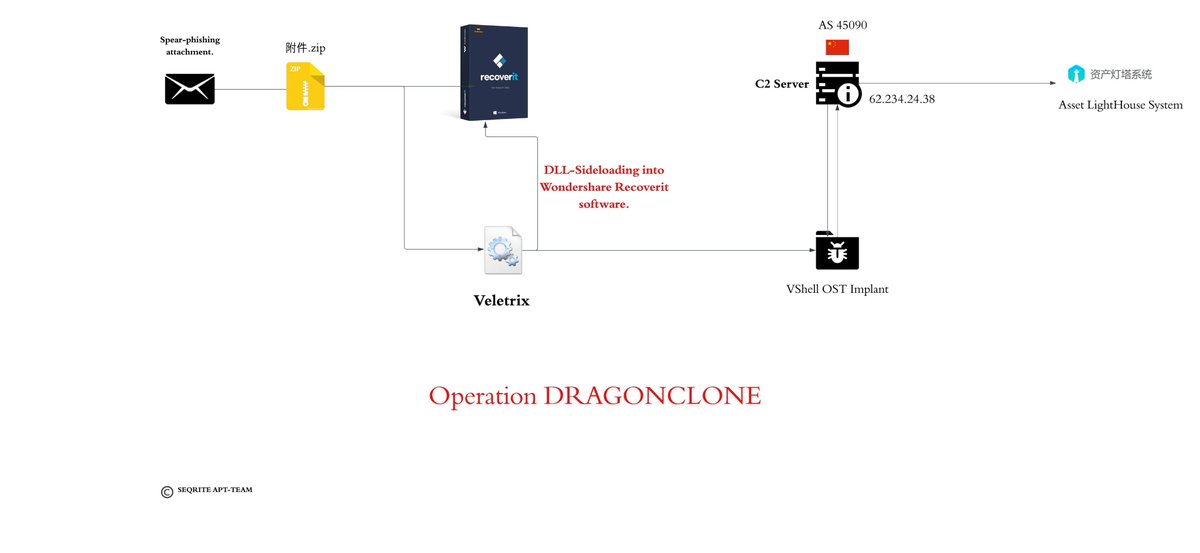
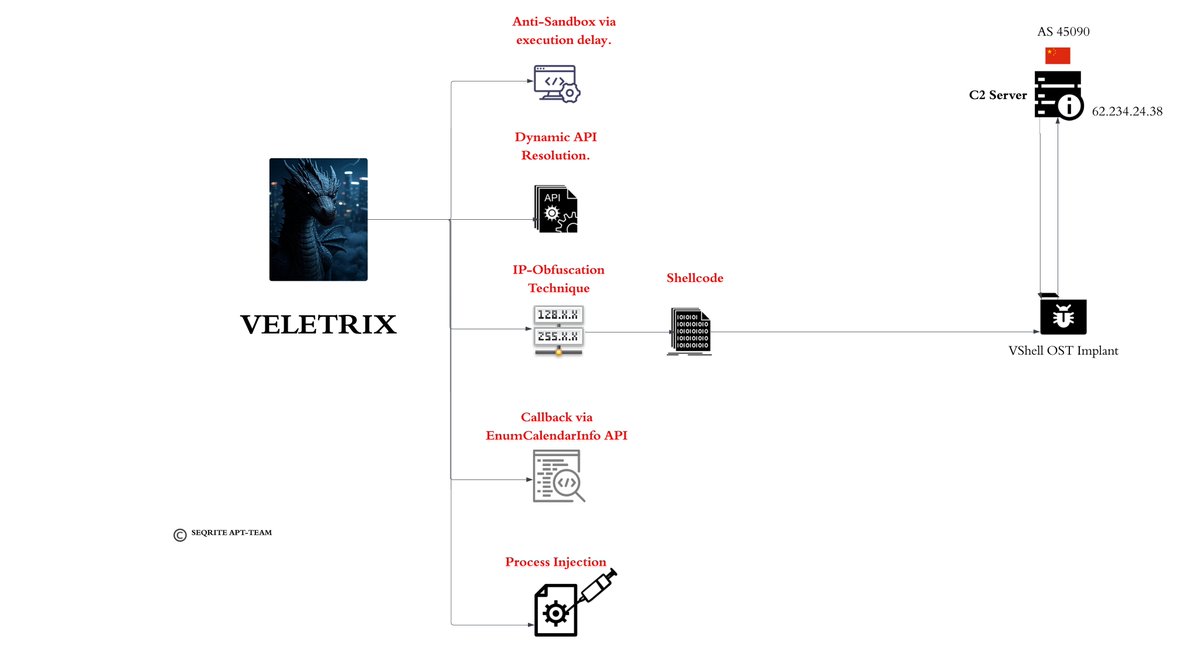
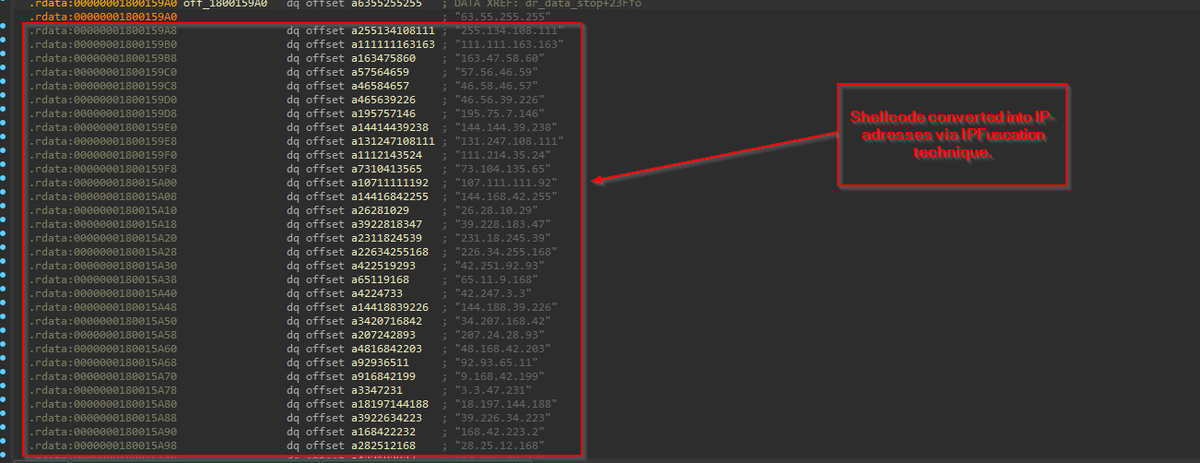
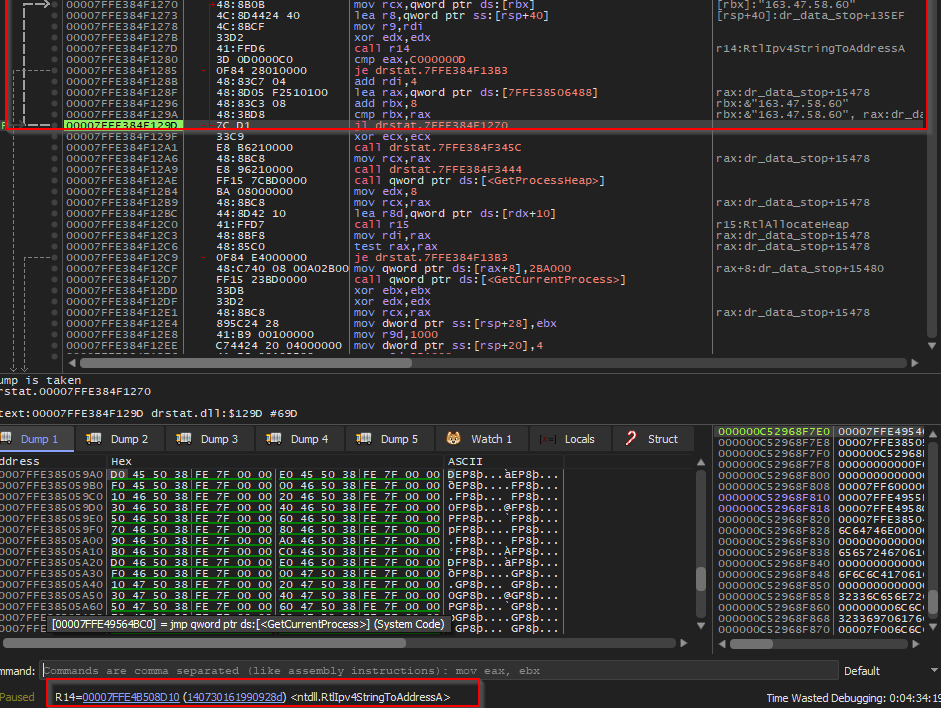
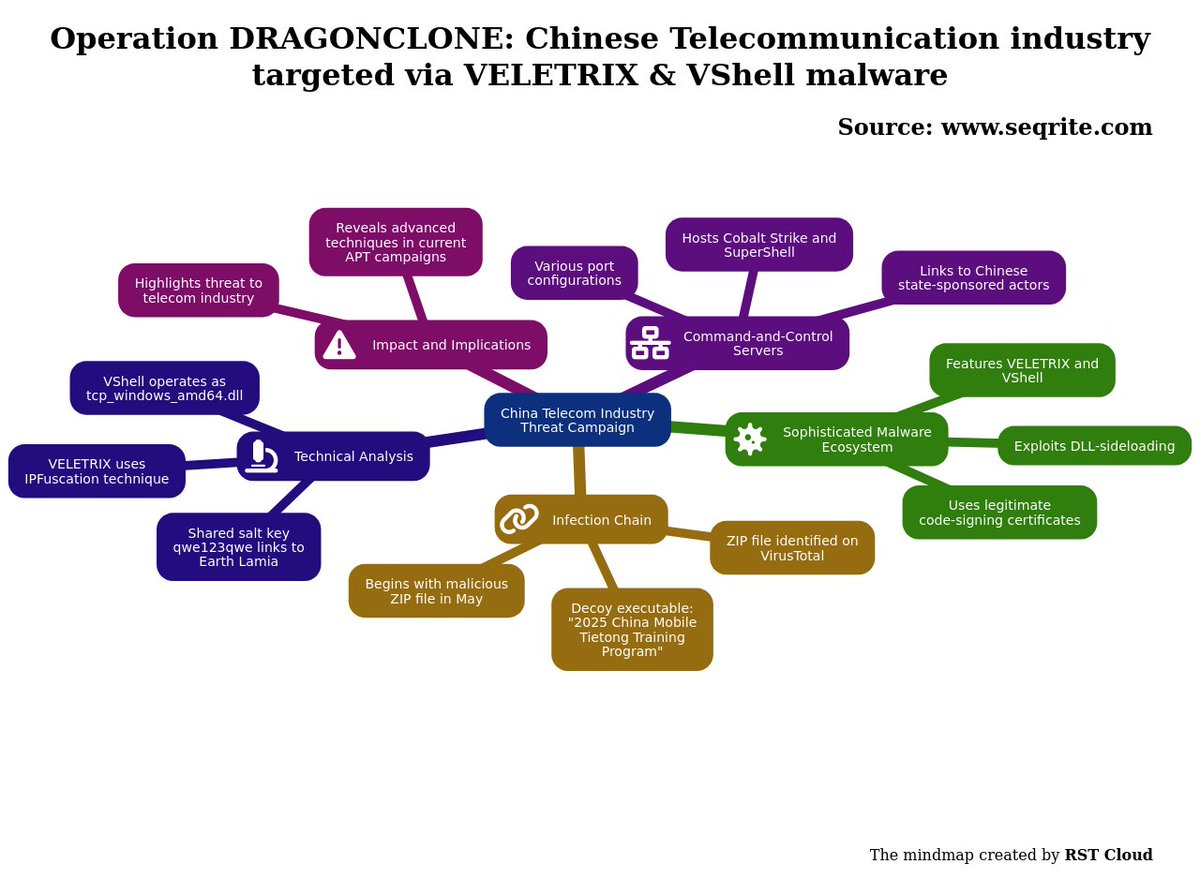
#threatreport #HighCompleteness.Operation DRAGONCLONE: Chinese Telecommunication industry targeted via VELETRIX & VShell malware | 06-06-2025.Source: Key details below ↓. 🧑💻Actors/Campaigns:.Dragonclone.Unc5174.Earth_lamia. 💀Threats:.Veletrix, Vshell,
1
1
0
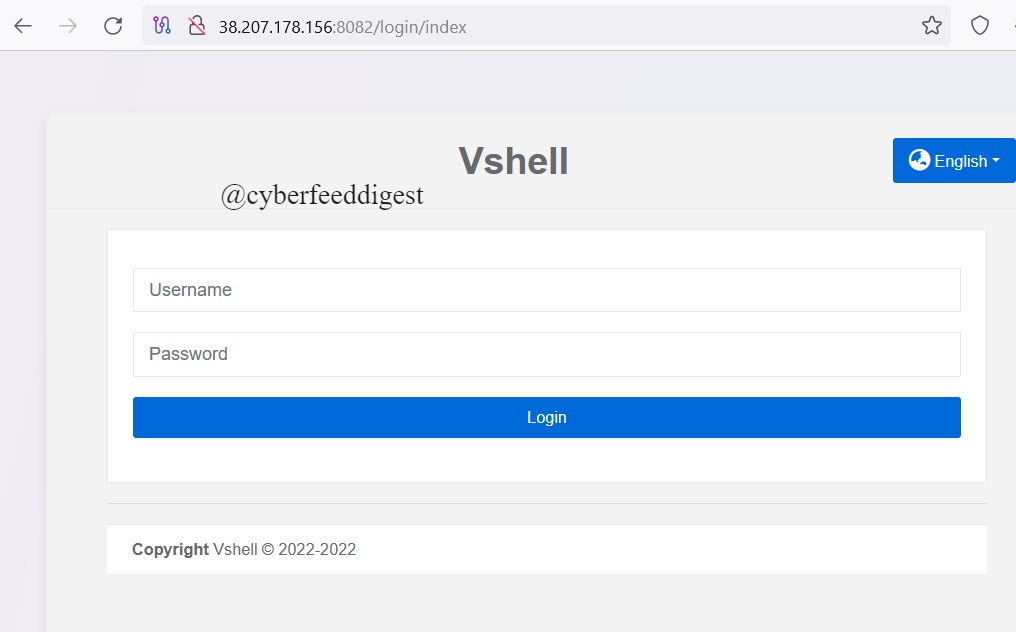
🚨 #C2 #Malware alert! #Vshell detected:. hxxp://38[.]207[.]178[.]156:8082/login/index . cc:@abuse_Ch . #CyberSecurity #Infosec #ThreatAlert #C2 #Malware
0
1
1
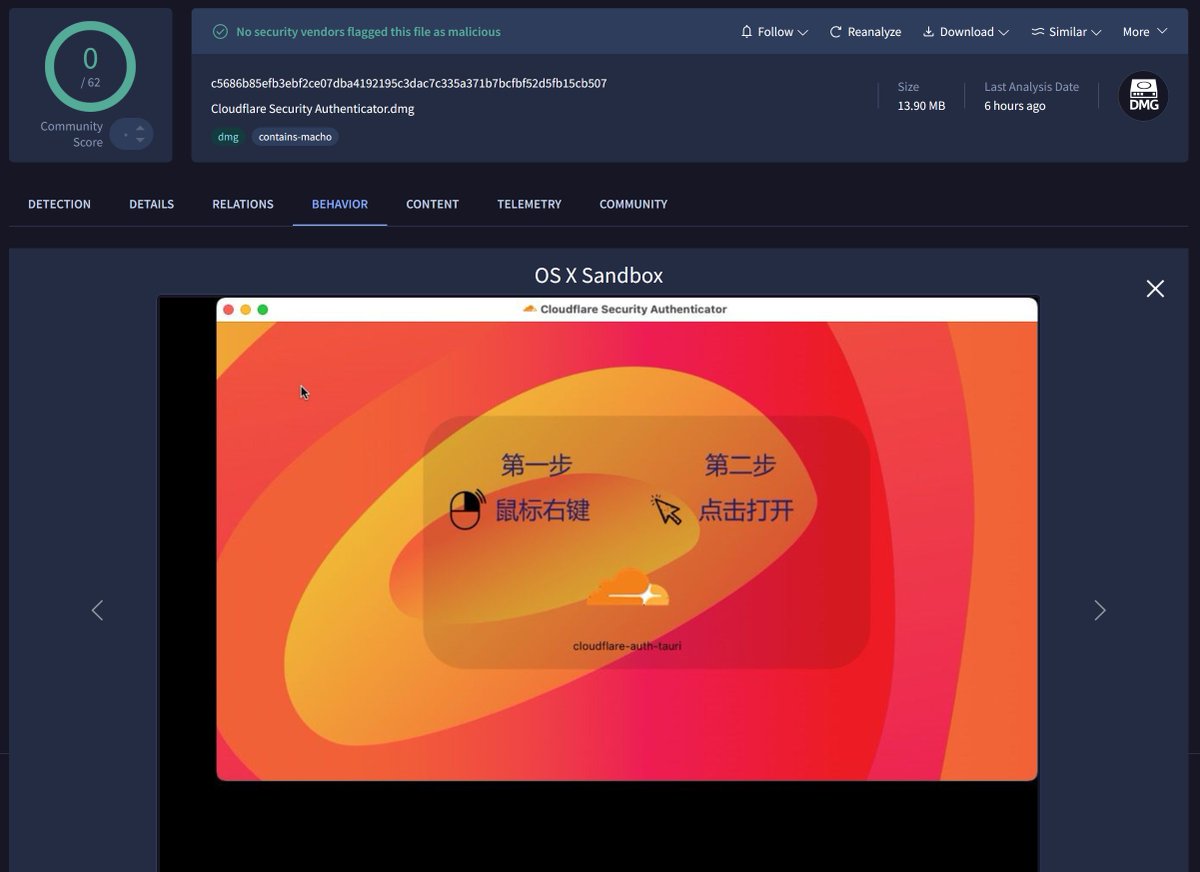
0 detection.Cloudflare Security Authenticator.dmg.c5686b85efb3ebf2ce07dba4192195c3dac7c335a371b7bcfbf52d5fb15cb507.#vshell
1
2
21