Explore tweets tagged as #SecurityLoggingandMonitoringFailures
Security logging and monitoring failures. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign #securitymisconfiguration #vulnerableoutdatedcomponents #IdentificationAndAuthenticationFailures
0
1
1
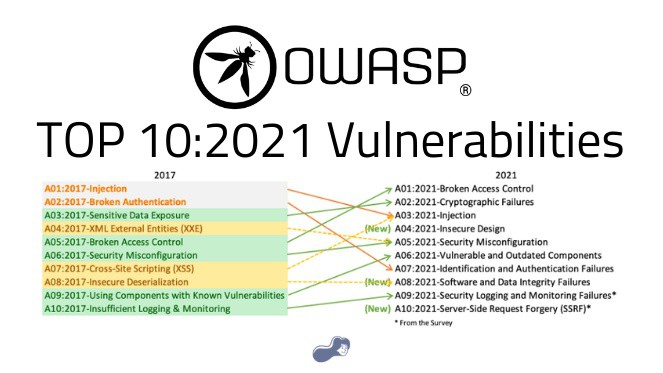
One vulnerability includes all the vulnerabilities that occur due to deficient or incorrect use of authorization mechanisms. Read the full article: OWASP Top 10:2021 Vulnerabilities.▸ #SecurityLoggingandMonitoringFailures #owasp2021
0
0
0
Identification and authentication failures. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign #securitymisconfiguration #vulnerableoutdatedcomponents #IdentificationAndAuthenticationFailures.
0
1
3
Hardening, incorrect configuration, using the default password, and leakage of information from error messages are included in this category. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign.
0
0
1
Software and data integrity failures. Read the full article: OWASP Top 10:2021 Vulnerabilities.▸ #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign #securitymisconfiguration #vulnerableoutdatedcomponents.
0
0
0
Previously, it used to be at 10th place, but it's currently at 9th place in OWASP's 2021 top 10 list. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign #securitymisconfiguration.
0
0
0
Server-side request forgery is one of the new vulnerabilities on OWASP's 2021 top 10 list. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign #securitymisconfiguration #vulnerableoutdatedcomponents.
0
0
0
One of them is a newly added vulnerability to OWASP's top 10 security vulnerabilities. Read the full article: OWASP Top 10:2021 Vulnerabilities.▸ #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign.
0
0
0
Any vulnerability originated from the use of the data received from a user without being filtered in a piece of code processed in the backend. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign.
0
0
0
Previously occupying 9th place, "Using components with known vulnerabilities", was put at 6th place after adding "the use of unsupported software" to its list of vulnerabilities. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021.
0
0
0
Vulnerabilities such as pages lacking frequent control, bypassing access control due to parameter changes in the delivered requests, and CORS misconfiguration can be shown as examples. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021.
0
0
0
Previously occupying the 2nd place as "Broken authentication", this category includes the vulnerabilities originating from authentication errors. Read more 👉 #SecurityLoggingandMonitoringFailures #owasp2021 #cryptographicfailures #insecuredesign.
0
1
1