Explore tweets tagged as #BinaryExploitation
How to exploit a double-free vulnerability ('Use After Free for Dummies'). #binaryexploitation #hacking #cybersecurity
1
82
309
Understanding Heap Overflow in a single picture. #bugbounty #bugbountytip #infosec #cybersecurity #binaryexploitation #redteam #hacking #heapoverflow #windows
3
3
9
Into the art of Binary Exploitation 0x000002 [Sorcery of ROP] #ReverseEngineering #BinaryExploitation #Hacking #Pwn #BugBounty #Infosec
0
24
58
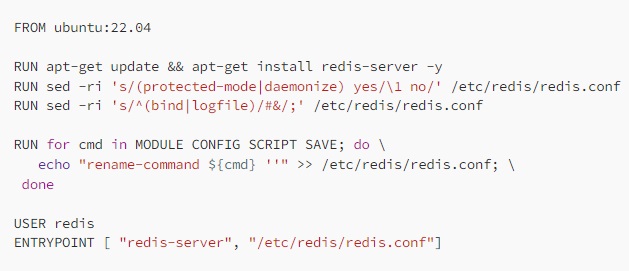
ABD - Course Materials For Advanced Binary Deobfuscation #ABD #BinaryAnalysis #BinaryExploitation #Deobfuscation
0
20
57
6 NEW #HTB TRACKS 🚨.#BlueTeam, #BinaryExploitation, #OWASP Top 10, and more!.30 Retired Challenges ADDED! ✅.🎯 Choose your way to become a #Cyber Expert! Start today ➡️ #HackTheBox #CyberSecurity #Tracks #Pentesting
4
35
134
💻 A Noob's Guide To ARM Exploitation. 👉 ARM Basics.👉 Buffer overflows.👉 Integer overflows.👉 Rop chains.👉 Heap exploitation.👉 ARM64 exploitation and much more. #infosec #exploitation #binaryexploitation #ExploitDevelopment #reverseengineering
2
42
105
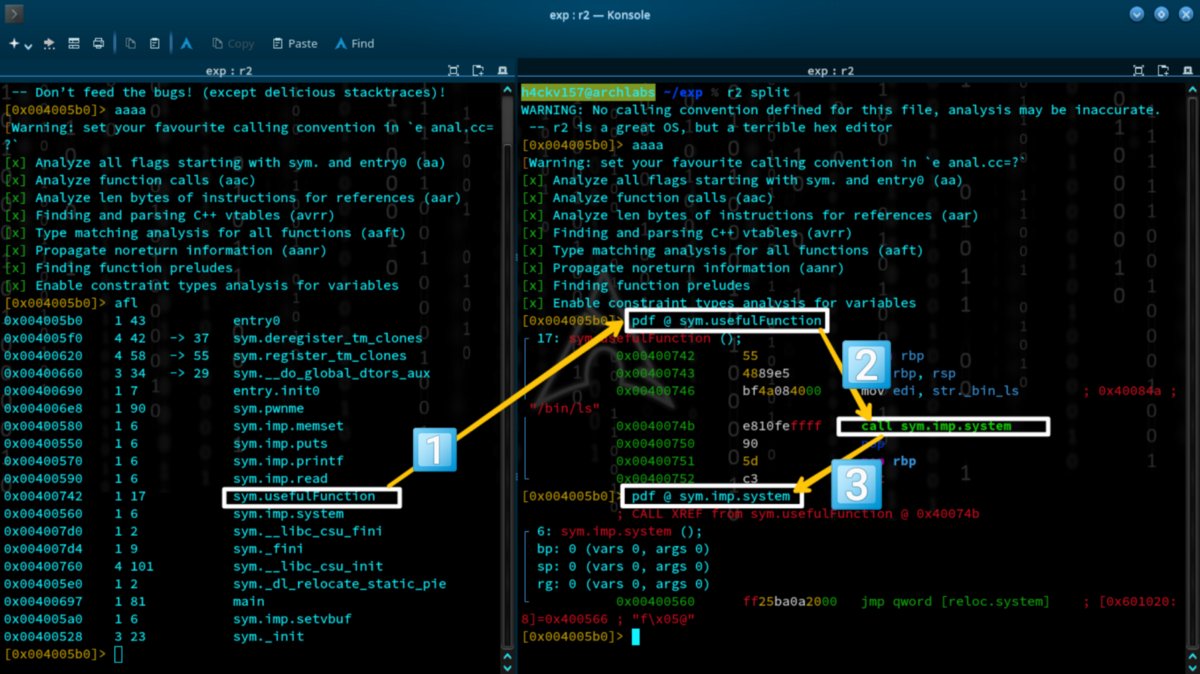
Into the art of Binary Exploitation 0x000001 [Stack-Based Overflow] - by 7𝖍3𝖍4𝖈kv157. #binaryexploitation #malware #reversing
0
6
31
Horrible stormy day! Only one thing for it: Buffer overflow and exploit development practice. #stormciara #HackTheBox #Hacking #Pentesting #exploitation #cybersecurity #ethicalhacking #linux #binaryexploitation #ellingson #bufferoverflow #rop #ropchains @hackthebox_eu
1
5
15
🧑🏻💻Part 7 of ARM64 Reversing and Exploitation Series helps you master ARM64 Binary Explotation and bypass ASLR and NX restrictions➡️#MobileSecurity #ARM64 #Reversing #Exploitation #BinaryExploitation #CyberSecurity
0
7
26
Are you in? We are in as sponsor! .#ctf #myhacketech #WebExploitation #Forensics #Reversing #BinaryExploitation #Cryptography #OSINT
0
1
4
Happy :) . Took down a medium level box. Quite a progress. Blog - I have just completed this room! Check it out: #tryhackme #cve 2019-8943 #linux #security #binaryexploitation
0
2
1
Explore integer overflows and their impact on software security: Share with your network! #MobileSecurity #ARM64 #Reversing #Exploitation #BinaryExploitation #CyberSecurity
1
8
34
Sekiryu - Comprehensive Toolkit For Ghidra Headless #BinaryExploitation #GhidraDecompiler #GhidraExtension
0
10
24