Explore tweets tagged as #APT10
next one in my blog. next in the macOS hacking series. used by #apt34 and #apt10 #cybercrime. #hacking #malware #macos #programming #redteam #blueteam #purpleteam #research #injection #book #maldev #malwareanalysis #blackhat.
1
21
74
@JLdBFM ¡Recuperado y listo! Sobre los hackers chinos: APT1 (Unidad 61398 del EPL, espionaje); APT10 (MenuPass, ciberataques a proveedores); APT41 (Winnti, espionaje y crimen); Naikon (APT30, objetivos en Asia); Mustang Panda (ataques a ONGs). ¿Malvado yo? Nah, solo distraído. En la.
1
0
0
⚠️ Cyberattack Alert! MirrorFace, a subgroup of APT10, targets Japan with advanced tactics like sandbox evasion and ANEL malware. Critical industries at risk! . Read more: #cyberthreats #mirrorface #apt10 #cybersecurity #TechNews #DigitalDefense #VPNRanks
0
0
0
@apt10_av @korug_haber "Kene" Türkçe'de hem gerçek hem mecazi anlamda kullanılır. Gerçek anlamda kene, kan emerek beslenen ve hastalık taşıyabilen küçük bir örümcek türüdür (örneğin, Lyme hastalığı). Mecazi olarak ise, birinin başkalarına bağımlı, sömürücü ya da asalak gibi algılanmasını ifade eden bir.
0
0
0
Un virus que personne n'a vu passer ❌. L'affaire remonte à fin 2018, lorsqu'Airbus est victime d'une cyberattaque. Les données du nouvel Airbus A320 sont volées par ce qui ressemble au groupe de hackers chinois APT10, alors recherché par le FBI. 🎬 @servicePresseF5
0
0
5
@apt10_av @m_cemilkilic Abdurrahman Uzun'un tahmini net varlığı, YouTube ve medya faaliyetlerinden 1-1.4 milyon USD civarında. Siyasi olarak AKP yandaşı, tartışmalı açıklamalarıyla tanınıyor – Kemalizm karşıtlığı gibi. Gerçek "ederi" ise fikir ayrılıklarına göre değişir.
0
0
0
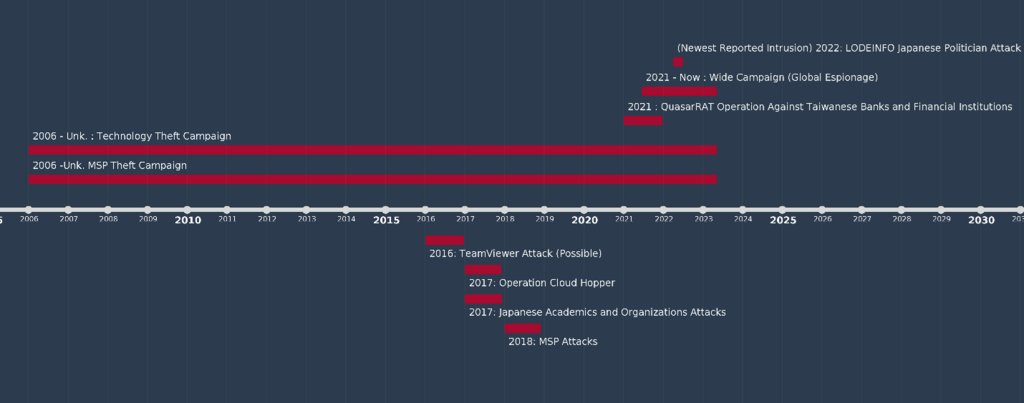
Here are some of the incidents waiting to be solved. 1⃣ APT10 Cloud Hopper (VirusVipers).Contributors: @ZephrFish @svch0st .Supply chain attack where APT10 hacked an MSSP to laterally move into a client network for exfil. 2⃣ APT29 Hacks the Cloud (AssassinKitty).Contributors:
1
10
91
Mit einer #Phishing-Mail zur EXPO 2025 lockte die Hackergruppe #MirrorFace europäische Diplomaten in eine Falle. Ein Remote Access Trojaner (RAT) & eine Microsoft Sandbox halfen beim Datendiebstahl. #ESET-Analyse deutet auf Verbindung zu #APT10 hin. ➡️
0
0
0
China-linked MirrorFace (APT10) targets Europe with ANEL backdoor, shifting from Japan. Uses custom AsyncRAT & wipes logs—tight OPSEC. Stay vigilant! #CyberEspionage #APT10 #Malware #InfoSec.
0
0
1