Asger.jpg
@hackerkartellet
Followers
654
Following
2K
Media
27
Statuses
213
🇩🇰 living in 🇩🇪 Principal IR dude trying to do IR stuff at @InfoGuardAG https://t.co/odU86jtnLL… @hackerkartellet.bsky.social
Munich, Bavaria
Joined January 2011
RT @malmoeb: Yesterday, I presented "Anti-Forensic" techniques for Windows and Linux at the Troopers conference in Heidelberg. This morning….
0
17
0
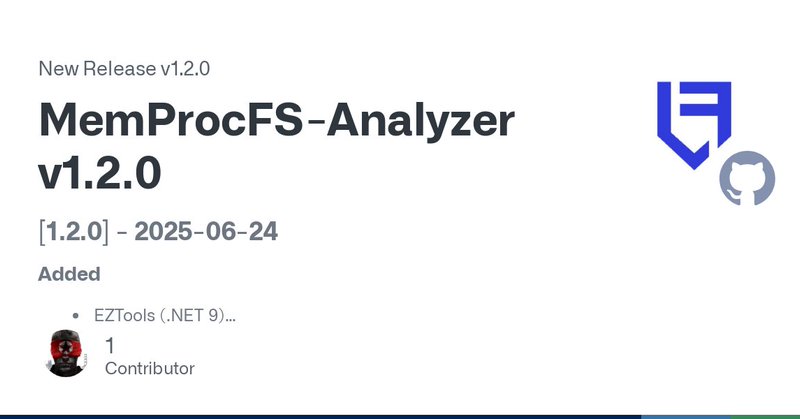
RT @LETHAL_DFIR: We just released MemProcFS-Analyzer v1.2.0 with various enhancements. Check out the changelog for more information. Happy….
github.com
[1.2.0] - 2025-06-24 Added EZTools (.NET 9) DFIR RECmd Batch File v2.11 (2025-03-31) 423 YARA Custom Rules FS_Process_Console FS_SysInfo_Network: DNS Information Digital Signature Fixed Minor fi...
0
19
0
RT @malmoeb: Some people commented on my post below, asking, "But isen't the domain legitimate?" Well. maybe? . Take a moment to visit th….
wizer-training.com
This is why you should NEVER copy paste commands directly into your terminal. Ask any developer or Admin if they have ever copied a command line or code snippet from the web. T
0
6
0
RT @LETHAL_DFIR: We just released Microsoft-Analyzer-Suite v1.5.1. This update includes bug fixes and a new version of RiskyDetections-Anal….
0
9
0
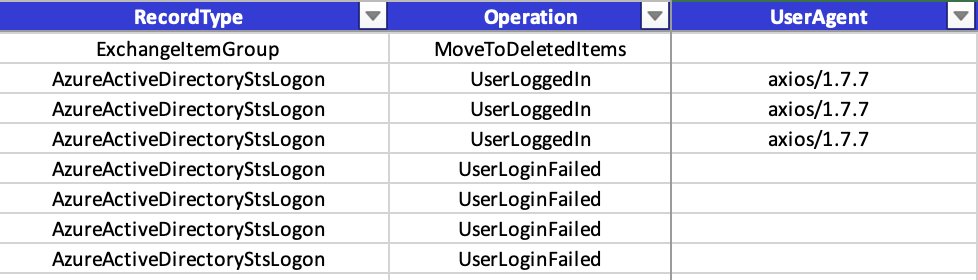
I am reposting my old post as a reminder to regularly check which UserAgents are logging into your tenant. In more recent instances, we have noticed that TAs are using tools with the following as part of their toolkit: .'node-fetch/1.0 (+'.'GuzzleHttp/7'.
github.com
A light-weight module that brings the Fetch API to Node.js - node-fetch/node-fetch
Analyzed a phishing case in M365: attacker bypassed MFA using axios HTTP client, leaving a telltale "axios/1.7.7" in sign-in logs. Lesson: regularly check sign-in logs for unusual user-agents to spot suspicious activity.
1
20
89
My big boss man is having a party writing awesome blogs. Take a look!.
New blog post: Tear Down The Castle - Part 2. I analyzed 250 PingCastle Reports, grouping the findings along the categories I used for my 10 AD Commandments series. The number of affected domains is stated within each finding, i.e., in how many domains we
1
1
3
RT @malmoeb: New blog post: Tear Down The Castle - Part 2. I analyzed 250 PingCastle Reports, grouping the findings….
0
49
0
RT @Evild3ad79: I just released Microsoft-Analyzer-Suite v1.3.0. UserAgent Blacklist added, ClientInfoString and Mailbox Synchronization de….
0
28
0
RT @malmoeb: New blog post: Tear Down The Castle - Part 1. I analyzed 250 PingCastle Reports, grouping the findings….
dfir.ch
Technical blog by Stephan Berger (@malmoeb)
0
69
0
RT @malmoeb: New blog post: Analysis of Python's .pth files as a persistence mechanism. I dig into Pythons Path Con….
0
14
0
RT @Evild3ad79: Teaser: Microsoft-Analyzer-Suite v1.2.0 will detect the new Device Compliance bypass technique via Microsoft Intune Company….
0
57
0
RT @SecurityAura: For those using the full User Agent in their queries, detection, hunt, etc . Time to increment the last number. Or ev….
0
1
0
RT @malmoeb: Did you know about the Windows Notifications database? While investigating suspicious behavior on a computer, I discovered evi….
0
48
0
RT @malmoeb: "A system administrator noticed that the user account kiosk had an active SSL-VPN connection to the corporate network. However….
0
25
0
RT @malmoeb: "The attacker successfully gained unauthorized access to the organization’s internal network through an SSL VPN endpoint hoste….
0
11
0
Throwback to a case I had in June.
When a user connects to a PC via the GetScreen software generates a session log file on the receiving computer. This log file records the source IP address of the connecting user and a timestamp. During an incident this past June, @hackerkartellet.
1
0
1
RT @malmoeb: Who actively monitors the Application Event Log for the Event ID 15457, containing the string xp_cmdshell?. The screenshot bel….
0
70
0
RT @malmoeb: I was looking through older Incident Response reports from our team and came across this paragraph here: . "The attackers were….
0
7
0
Lessons learned: Only allow approved external tenants to contact your tenant and lock down unused RMM tools. 3/3 . Ref: and
learn.microsoft.com
How to set up proxies and necessary endpoints
0
4
33