Matthew
@embee_research
Followers
14K
Following
3K
Media
496
Statuses
1K
Security Researcher, Creating and Sharing Educational Content.
Australia
Joined July 2022
A Beginners Guide to Tracking Malware Infrastructure . New post with 11 Examples (Including Cobalt Strike and Qakbot) that you can use to query and track C2’s, Open Directories and More🔥. (Special thanks to @censysio 🥳). #threatintel #malware.
censys.com
10
295
817
RT @silentpush: Firefox has a cool hidden feature for phishing investigations 😄. CTRL+SHIFT+M opens up responsive design mode, a menu for s….
0
29
0
RT @cyb3rops: I’ve noticed that some people misread my posts about AI. So let me try to be as clear and sober as possible:.I’m not saying t….
0
49
0
RT @felixm_pw: With some guidance from @DebugPrivilege I've found a way to easily dump clear text implants even while they sleep. Bad day f….
blog.felixm.pw
Dumping implants in a decrypted state
0
106
0
RT @thezedwards: Our team at Silent Push has been hard at work on the largest report we’ve ever made public – and along with Reuters – toda….
0
40
0
RT @silentpush: Did you know that registration emails can be used to hunt for #malware infra?. If an actor uses a unique email when registe….
0
15
0
RT @silentpush: We're seeing lots of similar #phishing domains to those reported by @_JohnHammond 🚨. The actors are using consistent naming….
0
6
0
RT @silentpush: Quick Tip for Hunting #LegionLoader Domains With #WHOIS Records🏹. LegionLoader actors have recently been creating #C2 domai….
0
13
0
RT @silentpush: Hunting Tip - Tracking #ValleyRAT Delivery Domains via ICP License Codes🔥. ValleyRAT has recently been reported using fake….
0
10
0
RT @silentpush: Quick Tip for Hunting #Lumma Domains By Checking WHOIS Records 🏹 . Lumma actors often create #C2 domains in (likely automat….
0
27
0
RT @vxunderground: Hi, I've seen a lot of noobies lately discussing their productivity. They're comparing their work ethic or research skil….
0
39
0
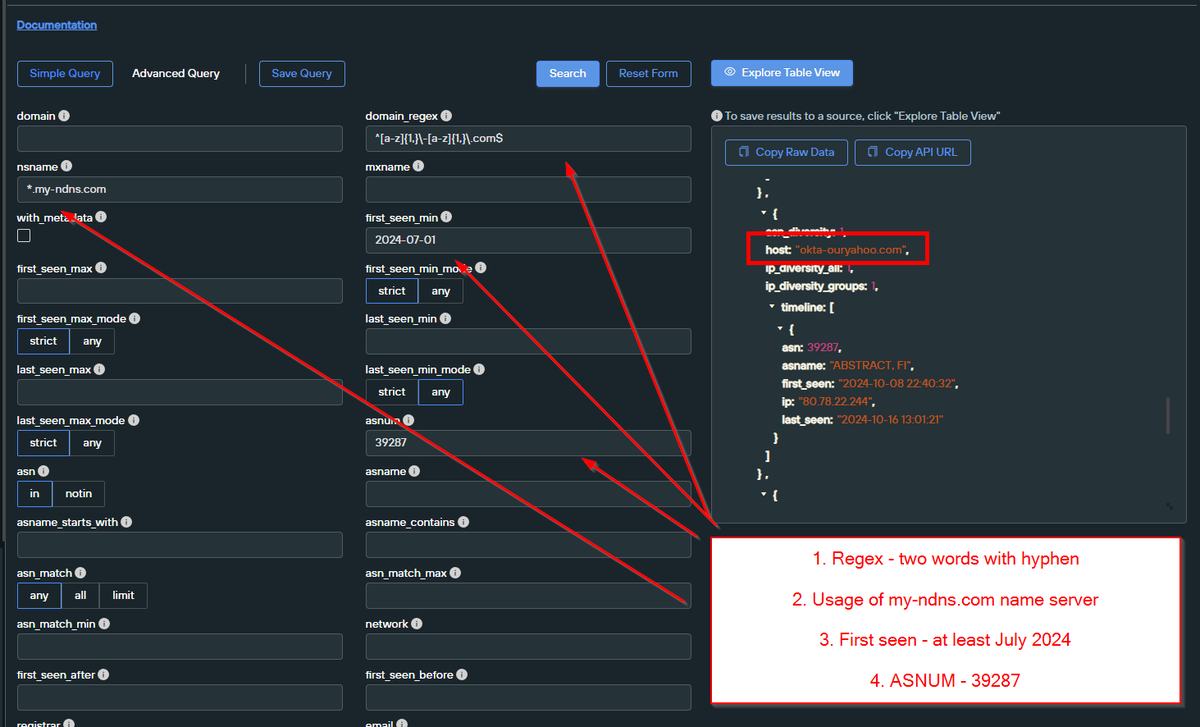
Nice and Simple Scattered Spider Pivots - Thanks to Initial Intel and previous posts from @TLP_R3D . 1⃣ Regex Pattern And Server Header .2⃣ Regex, Server Header and ASN .3⃣ Regex, Dates, ASN and Name Server . Utilising Domain Search and Web Scanner from @silentpush
🔥After a Long Break - New #ScatteredSpider . Domain: revolut-okta[.]com.IP Address: 80.78.27.6.AS Owner: ABSTRACT, FI
0
24
114
10/ The payloads appear to be zip files containing a legitimate exe and a (likely) sideloaded dll. Sadly, the sample wasn't publicly available, and VT didn't have a clear verdict on what it was. So we'll leave the analysis here and continue another day :)
2
0
3
9/ We can continue to apply the same concepts (identifying and searching strings) to locate additional pieces of the infrastructure. We can also search on the final URLs and determine the payloads.
1
0
2
8/ This leads to a bunch of new and interesting results. Some of them are almost identical (but with different file names) and others follow the same general logic but with quite different code.
1
0
2
7/ Pivoting on the Second Stage Content 👀. The second stage downloader contains a relatively unique combination of strings. We can pick some and query them to find similar code. I chose to use bitstransfer, expand-archive and start-process.
1
0
3
6/ We can find out more by searching the domain found in the downloader code. This reveals that the payload is another downloader. The code tries to download a zip and exe via bitstransfer, and then creates a run key for persistence.
1
0
1
5/ This works well - and shows many sites hosting similar suspicious content. Here we can see another site hosting the same text, but with a slightly different payload. The download function is the same, but the URL in the downloader is different.
1
0
2
4/ Now let's try and find similar sites. The previous text is relatively unique - so we can use it as a pivot point. Anything in the text tab can be searched - so let's try the "Press Windows Button "" + R" string.
2
0
2
3/ The "malicious" code can be found inside of the DOM content tab. This reveals that the payload is a simple powershell downloader
1
0
2