DarkShadow
@darkshadow2bd
Followers
2K
Following
1K
Media
96
Statuses
255
Ethical Hacker | Penetration Tester | Security Researcher | Bug Hunter | Exploit Developer. 🔥~For more Join my New telegram Channel👉🏼 https://t.co/9p1yvzluA4 ✨
ㅤㅤㅤㅤㅤㅤ404 Not Found ㅤㅤㅤㅤㅤㅤㅤㅤㅤㅤ
Joined September 2024
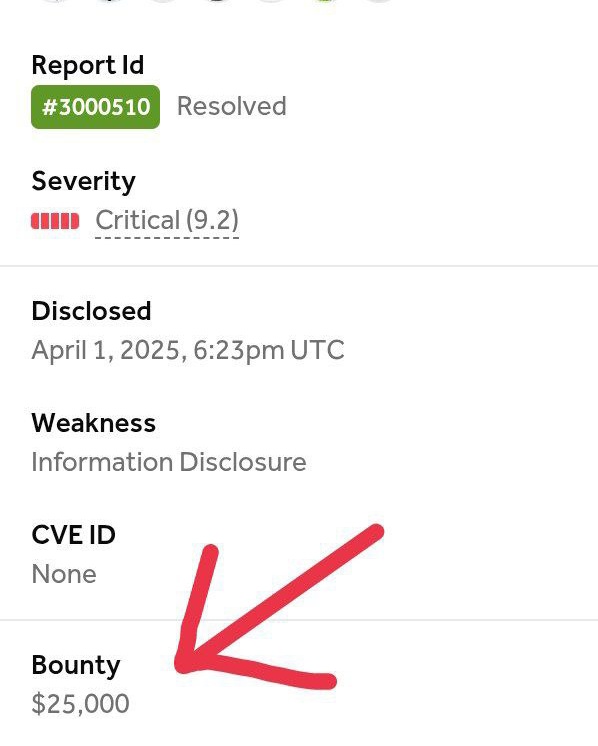
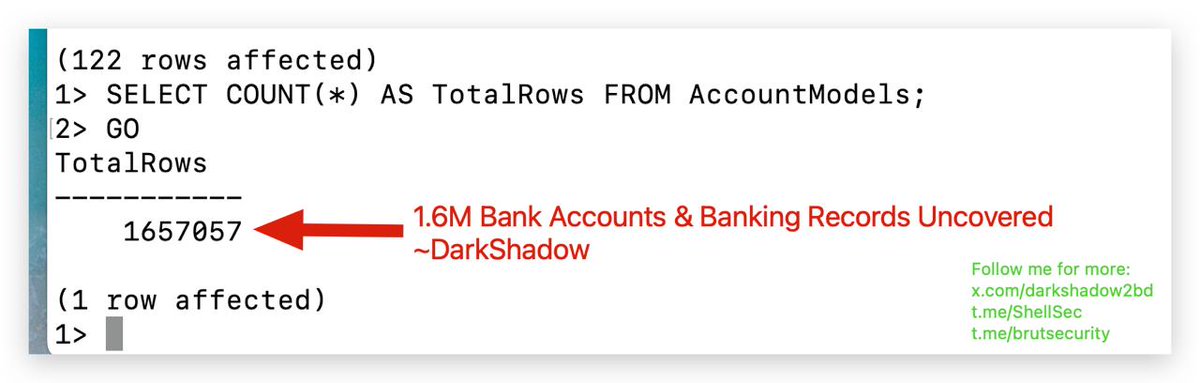
Recently disclosed hackerone critical bug, leaking sensitive informations which can exploitable under few minutes! Rewarded $25,000😏. Read the full POC in my telegram channel 👉🏼
7
23
358
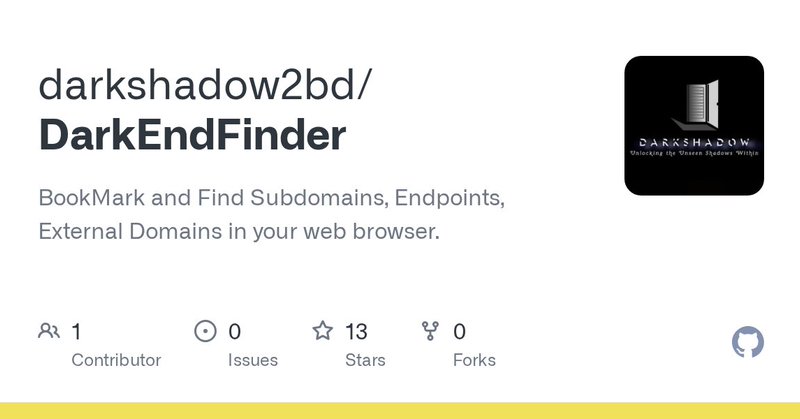
ㅤ.𝘿𝙖𝙧𝙠𝙀𝙣𝙙𝙁𝙞𝙣𝙙𝙚𝙧 my own private tool which i used to extract endpoints from browse through passive recon. ✨ Features:.✅ Extract subdomains. ✅ Extract categories endpoints from subdomains. ✅ Extract external domains.
github.com
BookMark and Find Subdomains, Endpoints, External Domains in your web browser. - GitHub - darkshadow2bd/DarkEndFinder: BookMark and Find Subdomains, Endpoints, External Domains in your web browser.
1
0
9
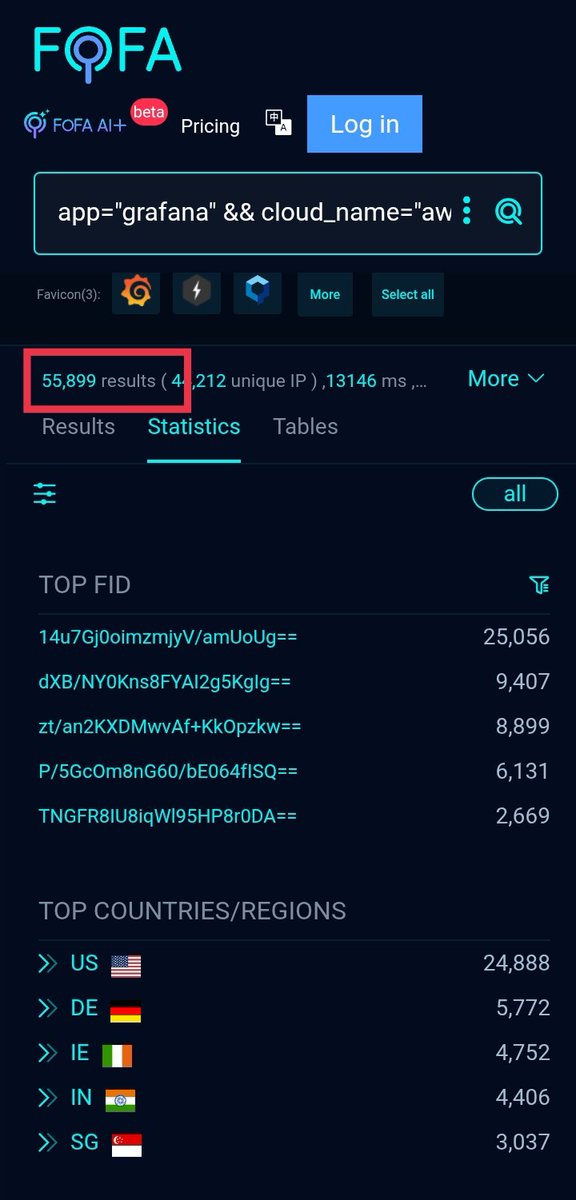
ㅤ.✨Grafana CVE-2025-4123 AWS SSRF @fofabot dork that find all vulnerable versions💯. 👀 Very big Dork:. app="grafana" && cloud_name="aws" && (body="Grafana v10.0.0" || body="Grafana v10.0.1" || body="Grafana v10.0.2" . [and more]. 🌀Get the full dork:
1
15
63
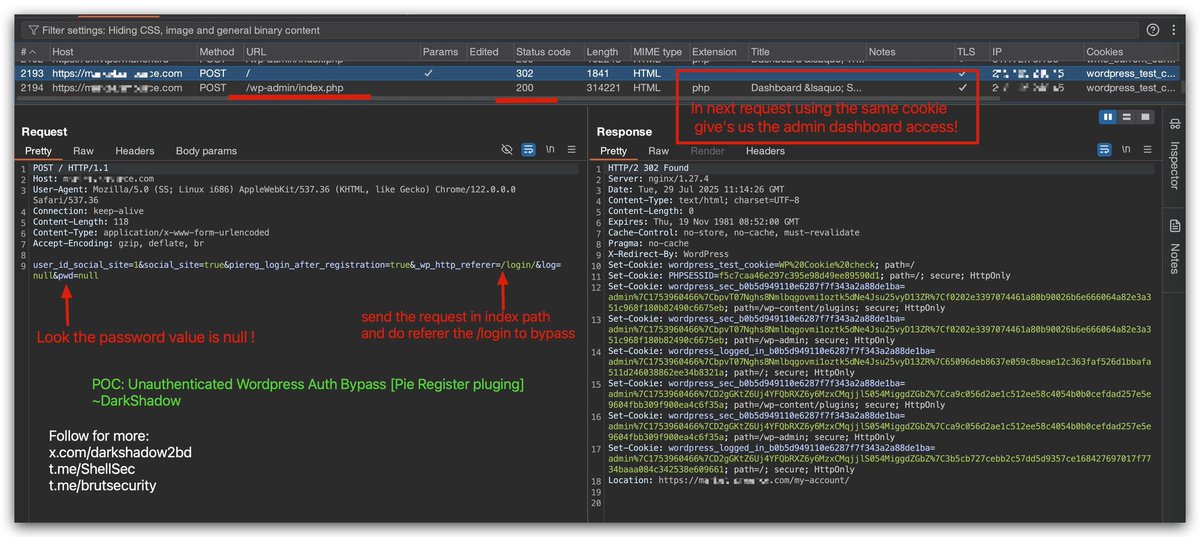
Using FOFA @fofabot Dorking you can see the content behind 401 unauthenticated🤯. Dork:.domain="401_subdomain" && (body=".php" || body=".pdf" || body=".xls" || body=".html" || body=".js" || body=".json" || body=".jpg" || body=".conf").Read full on telegram.
6
53
283