Daniel Cid
@danielcid
Followers
5K
Following
829
Media
145
Statuses
3K
Founder of CleanBrowsing, Trunc, Sucuri, and OSSEC. Former VP, GoDaddy. Builder & breaker by heart. https://t.co/zTP7IAqAIO / https://t.co/fk6P2mJON2 / https://t.co/DvBxP9yQch Temecula,Big Bear
Canada
Joined February 2009
My 7yo: "When I grow up, I want to be just like my daddy. He doesn't work and just spends his day at the computer doing nothing.".
13
34
177
RT @riper81: Today I published a personal project around #WordPress #security awareness. Please test and send me your feedback 🙏 . https://….
0
3
0
Interesting. First scan for CVE-2025-53771 (latest Sharepoint vuln) on our logs was on July 16th, a few days before public disclosure. 172.174.82.132 16/Jul/2025:07:31:10 +0000 "GET /_layouts/15/ToolPane.aspx HTTP/1.1" "
http://localhost" "Mozilla/5.0". From a Microsoft IP.
1
2
5
Pretty big issue:. Google and Microsoft Trusted Them. 2.3 Million Users Installed Them. They Were Malware. Extensions that get hijacked/bought are a common source of malware these days. Found some additional domains in the same IP address as them ( cc.
blog.koi.security
TL;DR - Our investigation of a single color picker exposed a coordinated campaign of 18 malicious extensions that infected millions
0
6
16
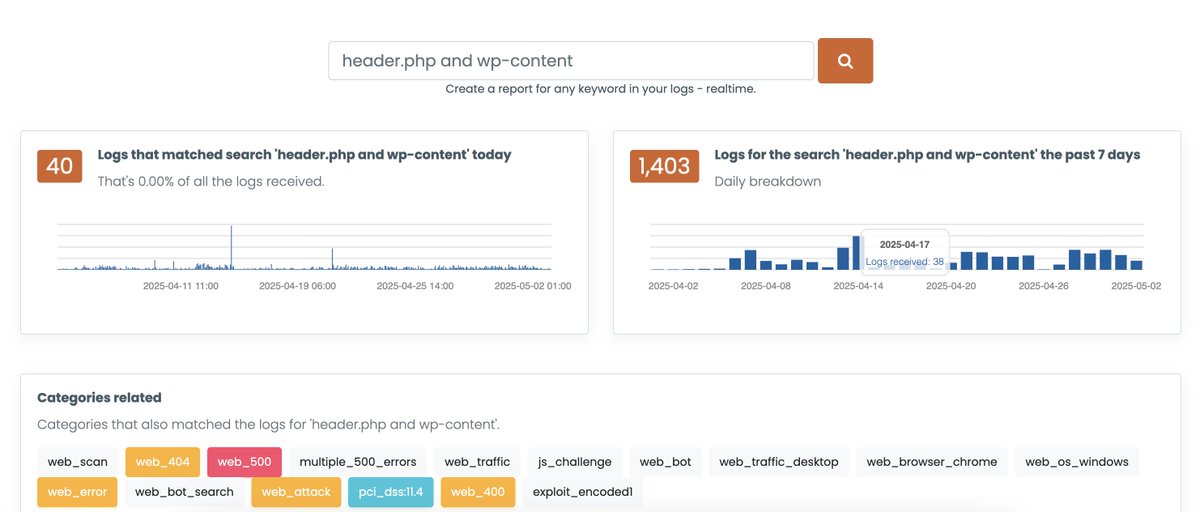
Expanded DNSArchive to also add web headers, CMS versions, links , css files, etc. You can now search for it here (in beta):. Ex:. All sites using PHP/5.2:. And you can still do DNS specific search here:.
dnsarchive.net
Web metadata search results for keyword: 'PHP/5.2'
0
5
12
RT @logwithtrunc: Have you noticed this "?slince_golden=test" requests on your logs? . It is for a WordPress Backdoor. We wrote a small sum….
trunc.org
What is the slince_golden WordPress backdoor? Detailed analysis of repeated attacks targeting fake WordPress files using the 'slince_golden' backdoor parameter.
0
3
0
RT @perezbox: 🚀 @logwithtrunc just got a fresh redesign. 🧑💻 Built for developers who care about clean, fast, secure log management. 🔍 Ch….
trunc.org
Trunc is a cloud-based SIEM and Log Management platform in the cloud. All your logs. One place. Simple. Affordable.
0
4
0
We put up a list with the top domains (most visited) via our DNS intelligence:. top 100.top 1,000.top 10,000.
dnsarchive.net
Explore the most queried domains across our DNS dataset. Identify high-traffic domains, their popularity, monitor visibility trends, and support threat intelligence with real-time DNS insights.
1
0
2
RT @noc_org: Have you looked at our DNS database?. DNS Archive has over 200m domains, IP addresses and historical DNS data:. .
dnsarchive.net
DNSArchive is a domain, DNS, RDNS and IP intelligence feed and DNS repository. We have over 220 million domains archived.
0
2
0
Big loss for Apple, big win for everyone else:. Hopefully next is the freedom to easily install Apps from anywhere - outside of the app store.
theverge.com
The judge called Apple’s insubordination a “gross miscalculation.“
0
0
2
It is not always DNS, but close. On April 16, between 2:25 P.M. ET and 4:12 P.M. ET, the domain was not available due to a server block by GoDaddy Registry. This block was the result of a communication error between Zoom’s domain registrar, Markmonitor,.
zoom.com
Modernize workflows with Zoom's trusted collaboration tools: including video meetings, team chat, VoIP phone, webinars, whiteboard, contact center, and events.
0
2
4
Anyone with a contact at @Quad9DNS ? They are blocking our Mastodon instance noc[.]social incorrectly.
3
0
1
RT @piuesportes: PRISCILA CID É OITAVA EM ASPEN! 🏂8️⃣. Hoje foi realizada a Copa Norte-Americana Premium de Snowboard Halfpipe, em Aspen, c….
0
2
0
RT @logwithtrunc: Linux tip:. Did you know that "nstat" clear the counters between each run, so you only see the data since the last time t….
0
1
0
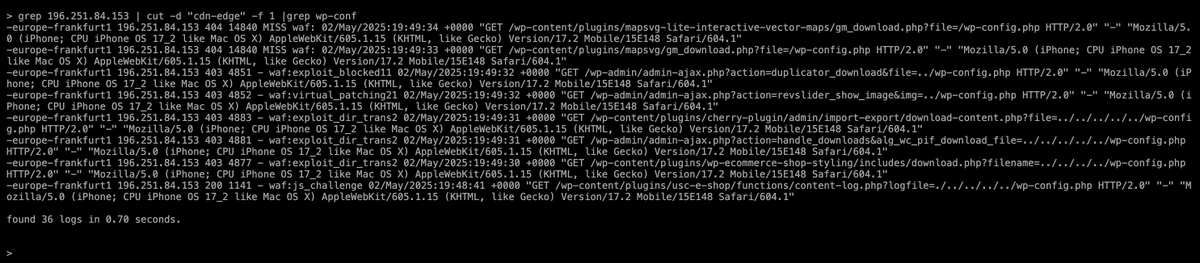
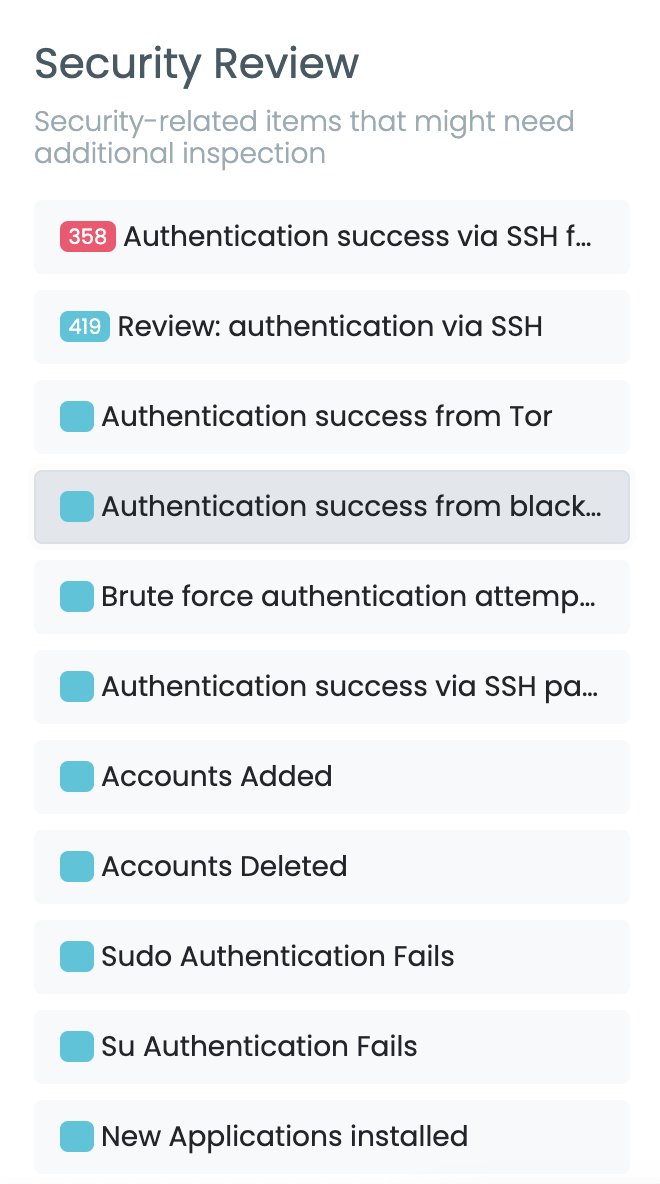
Threat Hunting by using Log Analysis - the basics. Some ideas on what to look for:. -system user logins.-login to unauthorized locations.-logins outside of "business" hours.-password ssh logins.-login from proxies/vpns/tor. Quite a few more.
trunc.org
Learn how to proactively identify cybersecurity threats through log analysis. This guide covers essential threat-hunting techniques, from detecting suspicious logins to flagging anomalies, ensuring...
0
1
2
Interesting article by the Drupal founder on Makers vs Takers. He exposes the impact when "takers" start to profit from the work of the "makers" (open source devs) without contributing much to that project. The problem I see on his argument is that the Internet and most of what.
In light of the recent discussions within the #WordPress community, I decided to share my perspective on the 'Maker-Taker challenge' in open source, drawing from my experience with #Drupal.
1
1
13
RT @logwithtrunc: Greg performance analysis. Grep is fast, but how fast? Some numbers we found on how much data it can parse per second -d….
trunc.org
Grep Performance - Grep is the goto command to search for content on Linux and Unix systems. How fast can it go? And at what point you need a a different way to look for logs.
0
1
0
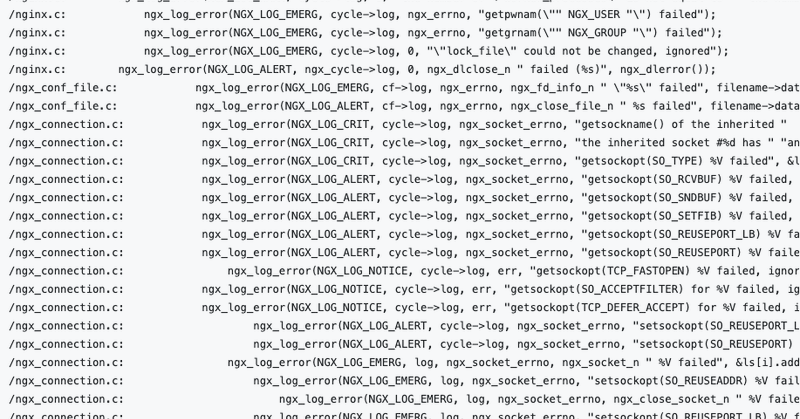
Spent quite a bit of time studying and documenting everything you probably don't need to know about nginx error logs:. If you use NGINX it might be interesting to know all those details, but likely useless. But if you like logs, it could be a fun read.
trunc.org
Everything you probably don't need to know about NGINX error logs.
0
1
8