CyberWave
@cyb3rw4v3
Followers
253
Following
57
Media
37
Statuses
62
Information security training and services platform https://t.co/VkT6KLnWSX
Joined October 2020
🎌The Cyberpunks CTF is now finished ! . We hope you had fun during this event. Congrats to the top-3 winners ! 🎉. Huge thanks to our sponsors @offsectraining and @OSINTindustries 🙏
2
3
15
🏴☠️ Les hackers personnalisent des outils publics pour contourner les antivirus. Dans cet article, nous démontrons comment il est possible de contourner Windows Defender en modifiant quelques lignes dans le code source d'un malware. Blog : #redteam
0
0
3
Ever tried to "shutdown" an EDR during an engagement but failed miserably ? . Here’s why (with SentinelOne as an example). #redteam
0
0
4
Curious about how EDRs work ? Here’s the second part of the series. This time, we talk about Kernel, Callbacks, Minifilters and other mechanisms used by EDRs on a Windows system. #redteam
0
0
5
Ever wondered what an EDR is and how it works ? Here’s a series of blog posts that lay out the foundations. Available in multiple languages (French, English, Italian, Spanish, Arabic, Russian…). #redteam 🏴☠️.
0
3
5
🚩 CyberWave est référencé parmi les Activateurs France Num !. 🌐 📧 Pour en savoir plus : contact@cyberwave.network
0
1
5
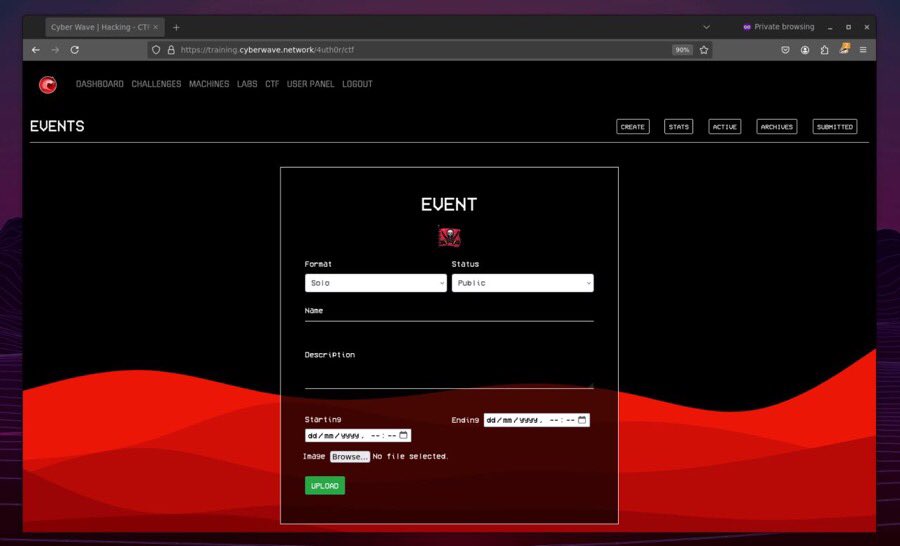
Create and host your own CTF event on our platform for free !. 👾 Main features : .- Build and host your own (solo/team) CTF event.- Upload challenges.- Monitor statistics and scoreboards. 🌐 📧 contact@cyberwave.network
1
1
6
RT @VirtualSamuraii: Salut 👋🏼 Voici un petit article qui explique comment il est possible de personnaliser des outils publics pour contou….
virtualsamuraii.github.io
Personnaliser un outil pour contourner les antivirus
0
2
0