CryptoMuseum
@cryptomuseum
Followers
2K
Following
32
Media
0
Statuses
306
Crypto Museum is all about historical cipher machines, spy radio sets, covert equipment, radio direction finders, intercept, spy cameras and much, much more.
Eindhoven
Joined March 2011
RT @VirtualColossus: As well as working on modelling & animating the complex paper feed mechanism, I've been having a play adding a few ext….
0
3
0
This receiver from Watkins-Johnson played an important role in the Watergate Scandal (1972-1974) that eventually led to the resignation of US President Nixon in 1974.
cryptomuseum.com
Watkin-Johnson RS-111 surveillance receiver, introduced in 1963 by CEI and produced until 1980. Played an important role in the Watergate Scandal.
0
0
10
RT @VirtualColossus: I broke more than fixed this week! I'd placed a few items in the machine out of line so last few bits didn't fit in. H….
0
1
0
This device was used by the German Army to capture and decode Yugoslav telegraphy signals in Kosovo:
cryptomuseum.com
Rohde & Schwarz GA-082 FSK analyzer, used from 1983 onwards for interception and analysis of telegraphy signals.
0
14
32
RT @VirtualColossus: I've been learning about the SG-41, a mechanical pin-wheel cipher machine, developed as a replacement candidate for En….
0
3
0
Check out this power supply unit of 1965. It was used with the Fialka cipher machine (M-125) and proves that the Russians were well aware of TEMPEST and side-channel attacks.
cryptomuseum.com
Fialka power supply unit with TEMPEST features
1
4
22
Full description of the recently rediscovered 'Condenser PBJ' rotor-based cipher machine (1922-1924), now on the Crypto Museum website:
cryptomuseum.com
This is the first rotor-based cipher machine used in Czechoslovakia, developed between 1922 and 1924 and used until 1934.
1
3
7
New discovery: the 'Condenser PBJ' rotor-based cipher machine was developed between 1922 and 1924 and was used until 1934 by the Czechoslovak Army. Full reconstruction now online in Cryptologia (free access)
tandfonline.com
Condenser PBJ is a mechanical cipher machine developed by Pavel Baráček-Jacquier (1885-1969). It was created between 1922 and 1924, and was used by the Czechoslovak diplomatic service until 1934. T...
0
2
3
Introducing Enigma D: manufactured in 1926, this the father of all later Enigma cipher machines, including commercial Enigma K and military Enigma I
cryptomuseum.com
This extremely rare model of the Enigma cipher machine was sold in 1926. It is the predecessor of Enigma K and Enigma I, the famous machine that was used during WWII.
2
3
12
RT @electrospaces: Former #Wirecard-CEO Jan Marsalek and a former officer of the Austrian security service gave the Russian #FSB a laptop….
0
38
0
RT @VirtualColossus: Lots of work done this week on #VirtualM209, the casing is now almost completed. The ghosted part is a CT scan of a re….
0
7
0
30 years ago, CIA and FBI used this type of equipment for wireless overhearing and recording of conversations and evidence gathering. Now fully functional again.
cryptomuseum.com
Digital VHF surveillance receiver with 60 freely programmable channels, with covert body transmitter, used by US intelligence and law-enforcement.
1
19
70
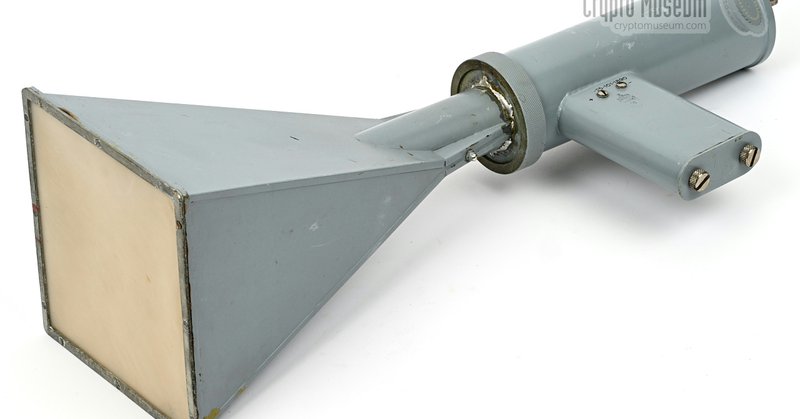
Check out this passive covert listening device that was developed around 1963 and was used by MI6 to spy on German industrials: If anyone has further information about these devices, please let us know.
cryptomuseum.com
Microwave receiver for passive covert listening device (bug), used by the British intelligence service MI6 to spy on its allies (and others).
2
14
38
Meet the ultimate rotor-based cipher machine, developed between 1952 and 1963 by Boris Hagelin:
cryptomuseum.com
Hagelin HX-63, the ultimate rotor-based cipher machine.
2
8
33
Who can help us to identify this spy radio set. It is believed to be from 1962 and was captured in China more than 30 years ago.
cryptomuseum.com
Two-piece valve-based clandestine radio set, probably built around 1963 by an unknown country
0
15
30
In 2018, this sophisticated bug was found inside a CryptoPhone used by WikiLeaks in London, around the time of the Snowden Revelations. In this article we analyse the bug:.
cryptomuseum.com
A sophisticated bug was found inside this CryptoPhone that was used by WikiLeaks between 2012 and 2016. Experts think it was planted by the CIA.
1
51
115