hi^^
@collysucker
Followers
227
Following
3K
Media
42
Statuses
766
Joined June 2009
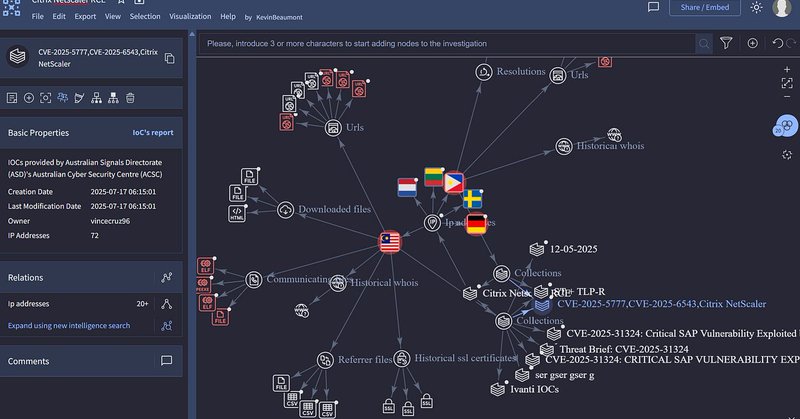
RT @cyb3rops: Citrix forgot to tell you CVE-2025–6543 has been used as a zero day since May 2025 | by Kevin Beaumont. .
doublepulsar.com
A look into what action Netscaler customers need to take ASAP.
0
155
0
. that they are finally working on it and making it transparent. Source: (2/2). #Microsoft #azure #infosec.
2
8
88
Microsoft Azure Portal CVE-2025-53792 CVSSv3.1 9.1. Afaik Microsoft claims the vulnerability was not public and no customer was affected. However Microsoft does not answer if they would have to logs/forensics to answer that. #infosec #azure #microsoft.
0
1
4
RT @Mandiant: 🛡️ Then read the next blog post to learn how to defend:
cloud.google.com
The anatomy of UNC3944's vSphere-centric attacks, and a fortified, multi-pillar defense strategy required for mitigation.
0
15
0
RT @albinowax: It's easy to bash vulnerabilities with logos but. I couldn't resist, say hello to :).
http1mustdie.com
Upstream HTTP/1.1 is inherently insecure, and routinely exposes millions of websites to hostile takeover. Join the mission to kill HTTP/1.1 now
0
89
0
RT @fabian_bader: This is big. In #XDR there is now a new table in preview:. GraphApiAuditEvents. It's the "free" version of the Microsoft….
learn.microsoft.com
Learn about the GraphApiAuditEvents table in the advanced hunting schema, which provides information about Microsoft Entra ID API requests made to Microsoft Graph API for resources in the tenant.
0
56
0
RT @malmoeb: I don’t know how many times I’ve discussed this topic before, but due to recent events, I'm bringing it up again: One of our c….
0
51
0
RT @cyb3rops: Windows SMB Client Elevation of Privilege Vulnerability. CVSS Score: 8.8. Attack Vector: Network.Attack Complexity: Low.Privi….
0
125
0
CISA guidance for SIEM - with details about with which logs to start, from your AD, EDR, OS, Virtualization, Azure, AWS, GCP, Hardening, etc. Really useful 👍.
cisa.gov
This guidance is intended for organizations seeking to procure SIEM and SOAR platforms.
0
0
1
RT @cyb3rops: Google just patched a serious ⚠️ vulnerability (CVE-2025-4664) that allows attackers to steal sensitive tokens (like OAuth or….
0
177
0
If it doesn't —> take action (e.g. contact Microsoft support & adjust backup parameters/rethink your desaster recovery process) (3/3). #azure #backup #desasterrecovery.
0
0
0
Tip: Test Azure backups & region failover. There is a known issue after an Azure region failover —> backups can become corrupted. That means in the event of a disaster affecting an Azure region, you may have no usable backup, putting you in a doubly bad situation. (1/3) #azure.
1
0
0
RT @DebugPrivilege: I often get asked what to do after running !analyze -v on a kernel memory dump. If you're wondering what steps you coul….
0
32
0
RT @cnotin: Microsoft hardened the Entra ID synchronization feature last year:.- restricted permissions on Directory Synchronization Accoun….
tenable.com
Microsoft synchronization capabilities for managing identities in hybrid environments are not without their risks. In this blog, Tenable Research explores how potential weaknesses in these synchron...
0
32
0
RT @DrAzureAD: If you haven't blocked device code authentication flow yet, do it now. Please, just do it! . @fabian_bader tells how to do t….
cloudbrothers.info
Deploy a conditional access policy that blocks device code flow
0
28
0
RT @nas_bench: Introducing 🚀Eventlog Compendium 🚀. A new Streamlit app, that aims to be the go-to resource for understanding and playing wi….
0
106
0
RT @olafhartong: Dear @MicrosoftAzure or @azuread teams, can you please make sure the casing of logged items is consistent?. Apart from wei….
0
11
0