Chris Norman
@chr_norm
Followers
248
Following
416
Media
25
Statuses
222
Building developer-focused security tools
London, England
Joined February 2017
Delighted to share that we’ve raised $3.1M for @CommonFateTech from @Work_Bench @haystackvc @EssenceVenture. Our mission is to empower teams with security tools that developers love and this funding will help realize it.
4
3
38
Full details including how to get started can be found here
commonfate.io
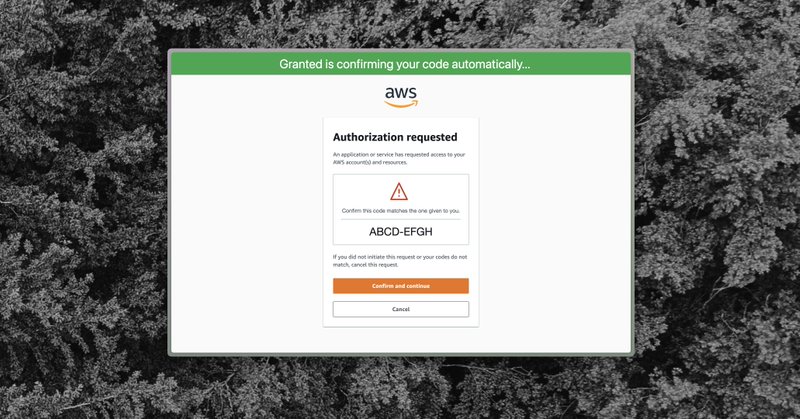
Today we're releasing a new browser extension for Granted which makes authenticating to AWS IAM Identity Center faster and more secure.
1
0
1
@christophetd has also published a deep-dive into this issue in 2021 (yes, it’s been a problem for 3+ years!) https://t.co/m8bYFBYdd2
blog.christophetd.fr
AWS SSO is vulnerable by design to device code authentication phishing, providing a powerful phishing vector for attackers.
1
0
0
Some background on the extension: I spoke with @ramimacisabird at @fwdcloudsec EU last month and Rami suggested we build it into Granted. Rami has a great article on AWS SSO phishing here https://t.co/fPp7xp2ZYX
ramimac.me
In AWS Phishing: Four ways, I mentioned the potential for AWS SSO Device Authentication Phishing.
1
0
0
Our browser extension protects against this by disabling the Confirm button if the code doesn’t match the one in the Granted CLI ( https://t.co/3NLzFWoRfF) Even better, when the code *does match*, logging in is much faster.
1
0
0
Attackers can abuse the device code login flow used by IAM Identity Center to steal credentials. This attack works *even if you’re using phishing-resistant MFA* like WebAuthn.
1
0
0
New article from me on the @cedarpolicy blog: validating Cedar policies using @github actions. If you use an authorization framework like Cedar, you will probably store policies as source code. My GitHub action validates these and annotates pull requests. Article link below!
1
2
7
I spoke at @fwdcloudsec EU 2024 on how we are using @cedarpolicy to protect our services in the cloud, including implementing our very own CloudTrail-like audit logs. The talk recording is now live!
1
0
1
LOVE this new policy language from @Resourcely, it’s concise and reads just like SQL
Today we’re introducing Really, an infra policy language that doesn’t suck. Writing and reading policy-as-code today is complex, and I’d love your thoughts! Give it a read and let me know what you think. 🧵 https://t.co/So2iE9ScKj
1
0
5
Granted v0.20.3 is now out! 🎉 🔍 Generate JSON output for SSO token expiry 🔧 What's Fixed: • Resolved IAM in secure storage + MFA issue • Fixed granted containers for Firefox Dev Edition Thank you for your support! 😊 Check out the full changelog at:
github.com
Generate JSON output for SSO token expiry Run granted sso-tokens expiry --json to print the SSO token expiry in JSON. Additionally, you can use jq to filter and display only the expired tokens in J...
0
2
4
Check out our latest updates at Common Fate! 🚀 📝 Profile Registry 🛠️ New Toolbar 🔐 Pop-up Code for AWS Login Details and full changelog 👇 https://t.co/ygVXkd7pZ3
3
2
5
Here's what we've shipped the past week at Common Fate: - Integrated Terminal ✅ - Built-In Support ✅ - Browser Selection ✅ Details and full changelog 👇
1
1
4
☁️ Glide Automate permissions to your cloud and critical applications By @CommonFateTech
https://t.co/6xwHqr6rcP
github.com
Automate permissions to your cloud and critical applications. - common-fate/glide
0
4
14
a question we ask ourselves daily: what would AWS look like if it had good UX and a useable console here’s our answer:
We’re excited to announce our new product, Common Fate. Common Fate extends on the wins we’ve had Granted, a CLI application which provides the world’s best DX for finding and accessing cloud roles to multiple AWS accounts. Why we built it and how to get access ⬇️
0
0
9