c0dejump
@c0dejump
Followers
535
Following
162
Media
51
Statuses
252
I had fun looking at which backup extensions were the most common on which tech & here's a short list:. WP: .tar/.zip.Joomla: .tar/.zip.Drupal: .tar/.zip.PrestaShop: .tar/.zip.Apache: .tar (.tar.gz, .tar.bz2).Nginx: .tar.IIS: .zip/.cab.Tomcat: .war/.jar. #bugbountytips #BugBounty.
2
5
21
RT @kevin_mizu: I'm happy to release a script gadgets wiki inspired by the work of @slekies, @kkotowicz, and @sirdarckcat in their Black Ha….
0
158
0
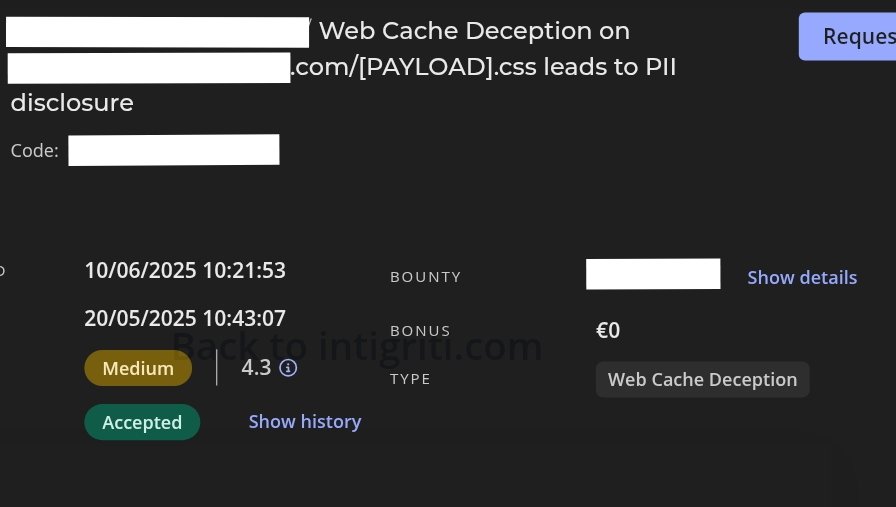
First bounty from Intigriti ! .- Vuln: web cache deception.- Tool: HF !.#BugBounty #intigriti
6
26
242
Plop !. Here's a new script to test the web cache deception, don't hesitate to contact us if you have any feedback or comments :). #bugbountytips
1
1
14
Hey,. Here's a python script to check the cve "CVE-2025-29927" by @zhero___ while waiting to add it to HExHTTP:. Thank you @zhero___ for feeding me so much ahah and excellent research and article as usual ! 💪.
github.com
script to check cve "CVE-2025-29927" while waiting to add it to HExHTTP - c0dejump/CVE-2025-29927-check
1
3
44
Plop ! . Happy new year !. For the new year, here's a little hexhttp update:. v1.7.2:.- New module for multiple headers cache error based on @0xrth observations.- New module for "human" scan, personal timesleep or random (0-5s) to each requests. HF !.
github.com
Header Exploitation HTTP. Contribute to c0dejump/HExHTTP development by creating an account on GitHub.
0
2
16
Plop !. HExHTTP v1.7:.News:.- Logging management.- Error logs management.Updated:.- ANSI banner at startup.- Fixed bugs.- Cache tag color.- Big linting and refactoring.- News payloads. & BIG thanks to @KharaTheOne for the help ! 😁. HF !.
2
1
14
Just got a reward for a high vulnerability submitted on.@yeswehack. - Vuln: DoS via web cache poisoning .- Payload: {Content-Type: text/html; charset=invalid-charset, Content-Encoding: xxxx}.- Tool: HExHTTP: & top 200 now ! 😁. #YesWeRHackers #BugBounty
8
18
143
Just got a reward for a high vulnerability submitted on @yeswehack . - Vuln: DoS via web cache poisoning.- Payload: "Max-Forwards: 0" (Or "foo").- Tool: HExHTTP: #YesWeRHackers #BugBounty
4
10
85
Plop ! . All the biggest news from HExHTTP !. - Many CP/CPDoS techniques added.- Code refont & many fixs.- Some checks on various technologies (CDN. ).- Github makeover. Thanks all & especially @Nishacid for help ! 🤝. HF ! 😁. #YesWeRHackers #BugBounty.
1
3
21
RT @Fransosiche: Yo les chefs,. Aujourd'hui, j'aborde le :. 🪄 Web Cache Poisoning🪄. Vulnérabilité pas super connue et peu exploitée en feat….
0
5
0
Just got a reward for a vulnerability submitted on @yeswehack. - Vuln: DoS via web cache poisoning (Host Header case normalization) .- Payload: "Host: .- Doc: - Tool: HexHTTP (. #YesWeRHackers #BugBounty
1
12
86
We're ending the year on a good vibe ! .Thx @yeswehack !. - Vuln: Cache Poisoning leads to link modification and potential DOS.- Payload: X-Forwarded-Port: 1234.- Tool: HexHTTP (. #YesWeRHackers
2
6
60
Hi hunters !. I've cache poisoning with the "Referer" header reflected in a script tag (see screenshot). Any ideas for poc an xss or similar ?. For info: .WAF: AkamaiGhost (console.log seem's ok). #BugBounty
1
0
4