Beyond Identity
@beyondidentity
Followers
19K
Following
2K
Media
1K
Statuses
3K
The only IAM platform architected to stop unauthorized access. Guaranteed to eliminate successful phishing attacks.
Joined March 2020
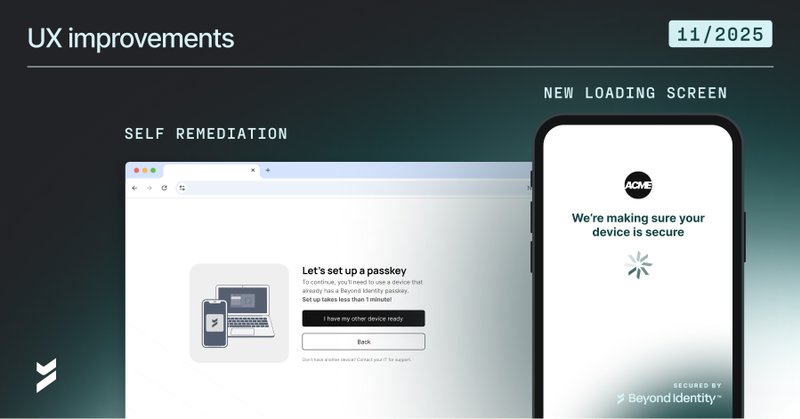
IT teams spend 40% of their time on account lockouts. It's not just costly, it’s avoidable. Not only is Beyond Identity passwordless (no more password resets!) we're also keeping customers ahead of the game with a new self remediation feature:
beyondidentity.com
Beyond Identity continues to simplify secure access and our latest updates, Self-Remediation and a New Loading Screen, take another step toward making passwordless authentication effortless for...
0
0
0
AI accelerates both defender and adversarial workflows. Great breakdown!
Google Threat Intelligence Group details the ways threat actors are misusing AI tools, including how they are generating and executing AI-enabled malware. 🔗 Read this latest report on our blog: https://t.co/VfvwpLFQXn
0
0
0
Low upfront cost and predictable monthly payments for your solar and Powerwall.
4
11
70
AI agents run 24/7 with broad access. They're vulnerable to prompt injection and spawn more identities faster than you can track them. In this world, continuous authentication must be a core part of identity defense for the future. Read more here:
beyondidentity.com
Non-human identities (NHIs) — devices, workloads, APIs, and AI agents — are now the fastest-growing attack surface. Learn why compromised NHIs fuel breaches, why traditional IAM fails, and how Beyond...
0
0
2
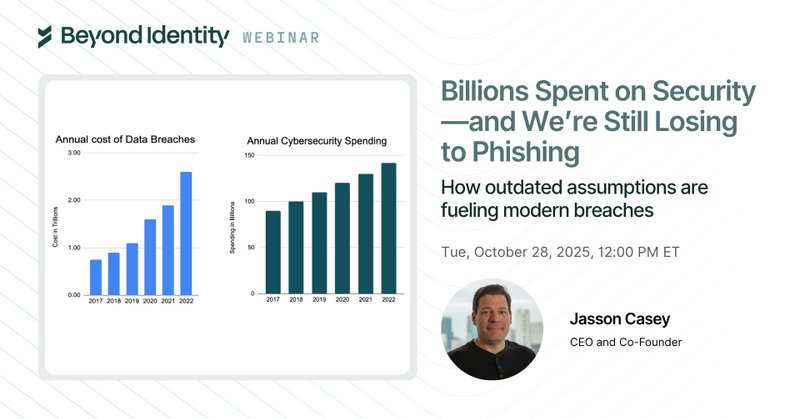
Cybersecurity spending ⬆ but breach frequency ⬆ Is this what winning looks like? We don't think so. Join @jassoncasey for his webinar to question the identity security assumptions that are holding defenders back...and what to do about it. https://t.co/szCtfr7rLR
insights.beyondidentity.com
Despite billions of dollars spent on security, attackers are still bypassing defenses quickly and effectively. Learn how to overcome breach defeatism.
0
0
2
Join us for this RSAC Webcast to explore the huge wide world of agentic auth with @Beyondidentity's Director of Product Strategy @sarah_cecc. Register: https://t.co/1y3nLZTCMM November 7 | 1:00 PM ET
2
2
3
The F5 breach just proved what security teams have been saying: perimeter defenses aren't enough. Continuous, Zero Trust defense is the answer, but most teams don't know where to start. This guide breaks down the 5 practical steps to get there 👇 https://t.co/cHnLQ29C1g
beyondidentity.com
The F5 breach highlights the need for a proactive security model. Learn how to implement dynamic identity defense against sophisticated threats to achieve Zero Trust.
0
0
0
We get it, there are a lot of Beyonds. Contrary to popular belief, we’re not the same company. 😅
0
0
1
⚠️ Your “passwordless” login might be weaker than your old password. Synced passkeys share your cloud account’s risks — recovery abuse, extension hijacks, and downgrade attacks. 🔒 Fix it: use device-bound passkeys that never leave secure hardware. Learn more →
4
53
168
.@beyondidentity's FedRAMP-authorized authentication platform is now available through our contract vehicles, helping agencies implement phishing-resistant MFA & meet #zerotrust goals. Explore how this supports identity-first security strategies: https://t.co/vo51x5lN44
0
1
1
We’re excited to announce our partnership with @Carahsoft! Together, we’re making Beyond Identity’s secure-by-design identity and access management platform more accessible to government agencies. Read the details: https://t.co/0GgLISjWbb
#ZeroTrust #IdentitySecurity
1
0
1
📢 @Microsoft is retiring legacy MFA & SSPR policies today. The unified Authentication Methods policy is here. But is it enough? Beyond Identity takes your Entra ID further, with passwordless, phishing-resistant access that ensures only trusted users & devices get in. Learn
0
0
0
#Zoomtopia is in full swing today and we are proud to be involved in the security and trust ecosystem for @Zoom! Deepfakes and AI impersonation are on the rise and detection tools can’t keep up. That’s why we built RealityCheck: to prevent deepfakes on your calls with
0
0
0
Attackers love legacy systems. We just ruined their fun. Beyond Identity now integrates with @CrowdStrike Falcon ITDR, bringing uncompromising identity defense to your on-prem environment. https://t.co/yaMl7MzdSI
0
0
0
🚨 Attackers didn’t hack your server—they stole a login. $1M ransom later, it was too late. Modern identity tools can block risky logins in real time, using signals your security stack already collects. Don’t wait until after the breach. See how →
thehackernews.com
Ransomware demand of $1M followed stolen credential login; legacy defenses missed it, proving identity is today’s perimeter.
0
9
29
Peanut butter & jelly. Batman & Robin. Beyond Identity & CrowdStrike. Some pairings are the perfect match. At #FalCon2025, see how our @CrowdStrike integration turns detection into immediate defense by extending endpoint risk signals into access policies.
0
0
0
Most orgs still secure people. But the fastest-growing attack surface isn’t humans — it’s non-human identities. Devices, workloads, and AI agents run with elevated privileges. Once compromised, they’re powerful entry points for attackers. Want to learn how to protect from this
0
0
1
Episode 89 - Beyond Passwords: Making Identity-Based Attacks Impossible in the Age of AI In this episode, Jasson Casey, CEO & Co-Founder @ Beyond Identity, and I dissect the growing threat of identity-based attacks, which now account for nearly 80% of breaches.
0
1
1
We’re headed to #FalCon2025 as a GOLD sponsor! Stop by Booth #1423 to see how Beyond Identity enhances your @CrowdStrike investment: ✔️ Extend risk signals to access policies ✔️ Quarantine non-compliant devices ✔️ Gain visibility into unmanaged devices Explore all our Fal.Con
0
0
0