J.D. Bean
@bean_jd
Followers
91
Following
26
Media
4
Statuses
943
Views are my own. RT ≠ Endorsement. Principal Security Architect, Amazon EC2
NYC
Joined July 2008
RT @colmmacc: It's long been hard to do secure fast Open Source cryptography and FIPS. Libraries would omit compatibility, or use slow and….
aws.amazon.com
AWS Cryptography is pleased to announce that today, the National Institute for Standards and Technology (NIST) awarded AWS-LC its validation certificate as a Federal Information Processing Standards...
0
21
0
Hot off the presses — Delivering on the AWS Digital Sovereignty Pledge: Control without compromise, a new blog post from Matt Garman.
aws.amazon.com
French | German | Italian | Spanish At AWS, earning and maintaining customer trust is the foundation of our business. We understand that protecting customer data is key to achieving this. We also...
1
0
1
Excited to share that EC2 now supports a new confidential computing capability, AMD Secure Encrypted Virtualization-Secure Nested Paging (AMD SEV-SNP).
aws.amazon.com
0
0
0
RT @evervault: Thanks to recent advances, like the @awscloud Nitro platform and Nitro enclaves, utilizing this game-changing technology is….
0
1
0
RT @mjasay: Amazon’s quiet open source revolution. AWS finally sees open source obsession = customer obsession, and has accelerated invol….
infoworld.com
After years of getting a free ride from open source projects, the company is developing its own obsession with contributing.
0
14
0
RT @MikeScops: It’s been 18 months I’m developing this project from R&D to release, what a journey! . The challenge to make confidential co….
0
5
0
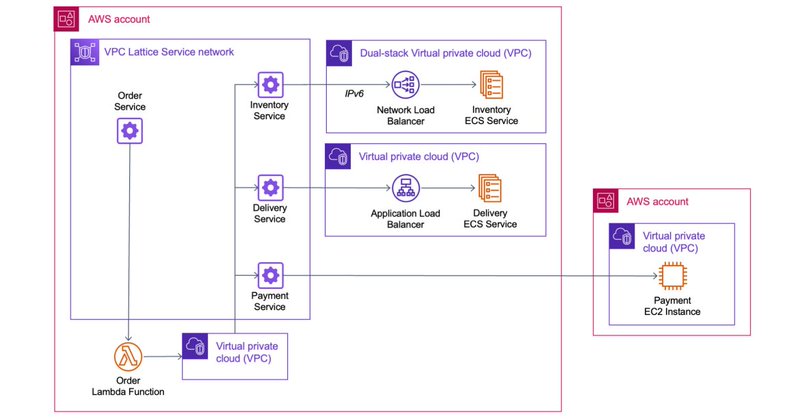
RT @_joemag_: I'm stoked that VPC Lattice went GA today! I'll do a longer thread on what lead to the creation of Lattice and how we are thi….
aws.amazon.com
At AWS re:Invent 2022, we introduced in preview Amazon VPC Lattice, a new capability of Amazon Virtual Private Cloud (Amazon VPC) that gives you a consistent way to connect, secure, and monitor...
0
22
0
RT @AlexGrinman: Just launched part 2 of our series on how @Footprint_HQ's vaulting infrastructure leverages Nitro Enclaves to secure sensi….
onefootprint.com
This post delves into the workings of Nitro Enclaves, their assurances, and Footprint's practical application of them.
0
3
0
RT @brave: Protecting users' information is a top priority for Brave. This blog post explains the technology that allows Brave to process….
brave.com
An overview of how Brave is able to process sensitive data without actually seeing the data, while also empowering users to verify our claims.
0
25
0
RT @kurtopsahl: Late contender for worst take of the year: NYT oped argues @signalapp is bad because users might not know it strongly prote….
0
259
0
So glad to end the year with the release of this Security Design of the AWS Nitro System whitepaper. Many thanks to the team of brilliant collaborators who made it possible!.
AWS recently released a whitepaper on the Security Design of the #AWSNitroSystem. See how we use the Nitro System to help secure your most critical workloads 🔒
0
1
3
RT @colmmacc: No better day than today to watch @abbyfuller's great talk about how Amazon responded to log4shell. Super interesting breakdo….
0
29
0
RT @mjasay: 👀 Look what just happened: @amazon (Capital "A" Amazon) just joined the Open Invention Network: What d….
openinventionnetwork.com
Durham, NC (December 6, 2022) – Open Invention Network (OIN), the organization formed to safeguard Open Source software (OSS) and the largest patent non-aggression community in history, announced...
0
8
0
RT @nithyaruff: The Open Invention Network does important work to sustain open source technologies for all, and we are proud to join them t….
0
4
0