atc1441
@atc1441
Followers
13K
Following
5K
Media
1K
Statuses
4K
Hack the planet! my biggest passion is to run a custom firmware on as many devices as possible
Hamburg, Deutschland
Joined May 2019
RT @hackaday: Playing DOOM on the Anker Prime Charging Station.
hackaday.com
At this point the question is no longer whether a new device runs DOOM, but rather how well. In the case of Anker’s Prime Charging Station it turns out that it’s actually not too terrib…
0
5
0
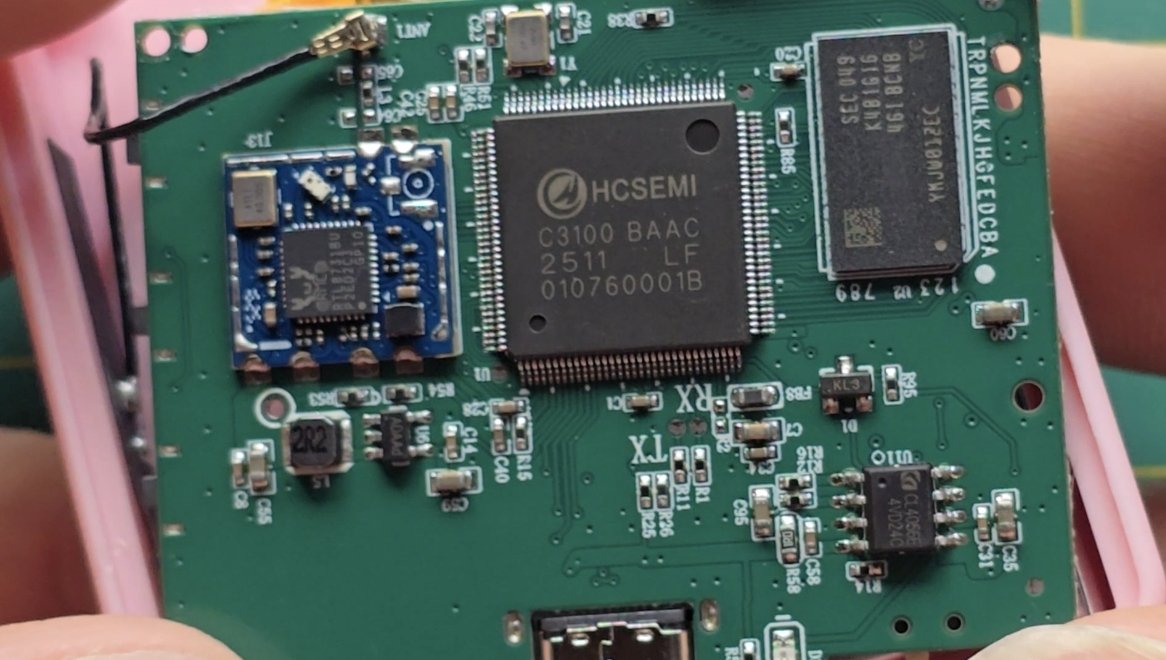
Debugger aquired, custom firmware runs🙌.Time to dump the firmware out of the 2€ Hörmann Remote clones SoC
Aha! So something along the lines of CA51F55_FM on the SoC of the Hörmann remote Fob Clone. Checking out google with this information again turns up the wanted result 🥳 and even the strange pinout fits. Its an CACHIP CA51F551M2 8051 8KB Flash 768 Byte RAM SoC. Nice journey
3
15
264
Sooo Anker also has this stationary "Anker Prime A2345" Charger, it includes BLE as well, and FCC Shows it consists an ESP32-C3 as well as an Synwit SWM34S so technically that could finally run DOOM(Just low FPS)😅.
Fun fact 50% of the (Latest)Firmware in the.BLE Enabled Power Bank Anker Prime 27650mAh.is just to for OTA checking and encryption. Fw version prior to 1.6.2 do not verify OTA at all so better update😅. Did take a look inside and reverse engineered it.
8
17
191
RT @hackaday: Hacking the Bluetooth-Enabled Anker Prime Power Bank.
hackaday.com
Selling power banks these days isn’t easy, as you can only stretch the reasonable limits of capacity and output wattage so far. Fortunately there is now a new game in town, with ‘smart&…
0
5
0
Here is the "More".
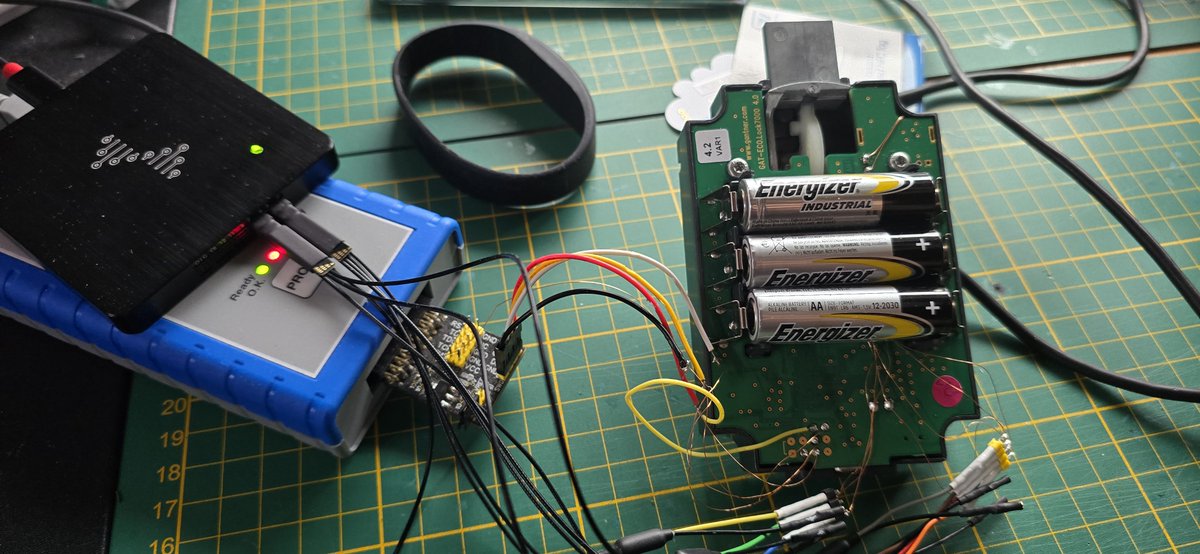
That's a success 🥳. Glitched and fully Dumped MSP430F417 in a non destructive way. Doing a Read data CMD and glitching the check if the password was entered we can dump 240bytes at once. By dumping the pass(vctr) area we can read the full flash after one glitch.@travisgoodspeed
0
0
19
@travisgoodspeed Some info's. It was important to separate DVcc and AVcc as much as possible to prevent resets and glitch on DVcc. All expect the last byte of the read CMD was send and the glitch timed to the last byte to prevent any big jitter. After position was found a glitch takes ~1minute.
0
1
7
That's a success 🥳. Glitched and fully Dumped MSP430F417 in a non destructive way. Doing a Read data CMD and glitching the check if the password was entered we can dump 240bytes at once. By dumping the pass(vctr) area we can read the full flash after one glitch.@travisgoodspeed
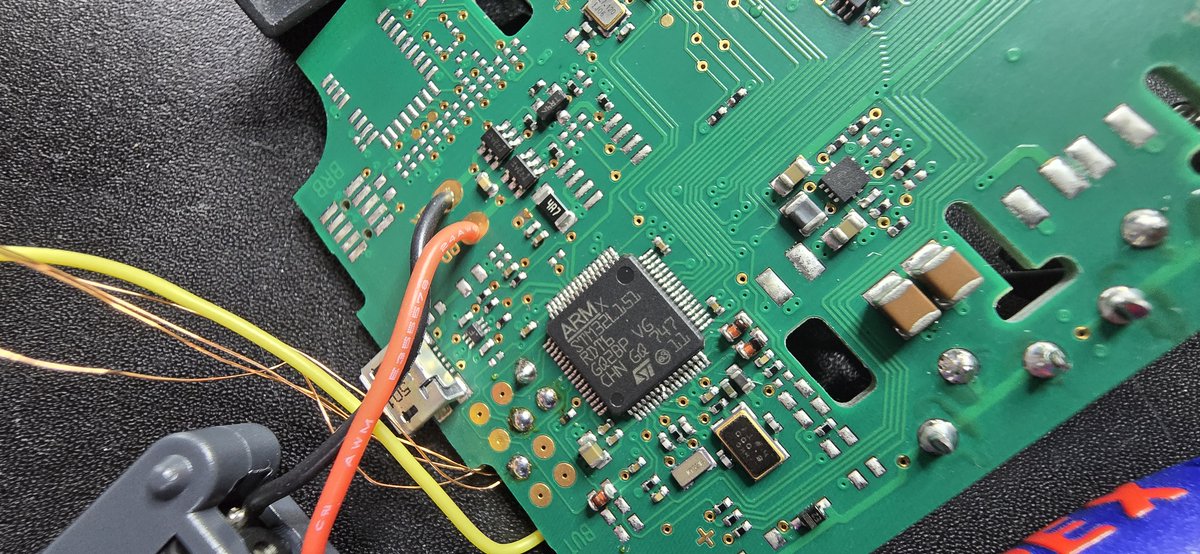
Custom firmware on an Heat cost Allocator. No use but funny to look into it and its WMBUS RF Packets. Next step is to dump the stock firmware via the ages old Timing attack from @travisgoodspeed (MSP430F417)
3
17
192