Arsenii P
@ars3n11
Followers
135
Following
156
Media
3
Statuses
13
All things red team. 🇨🇦 Opinions are my own.
Toronto
Joined October 2012
High-impact projects. Individual training budget. Dedicated R&D time. In-house vuln research and exploit dev team.
0
0
1
🇨🇦🚀 RBC Adversary Emulation is hiring! We're looking for a mid- to senior-level penetration tester / red team operator with a strong consulting background. 📍Toronto (preferred) or anywhere in Canada https://t.co/ioX9R4Qb1I
2
0
8
My personal favourite: - links only to core Windows libraries (msvcrt.dll and kernel32.dll) - links to msvcrt.dll using @mqudsi brilliant msvcrt.lib generator ( https://t.co/jYhR7CcAWZ)
github.com
msvcrt.lib for linking against msvcrt.dll on all versions of Windows - neosmart/msvcrt.lib
0
8
12
MineSweeper - a tool for Windows user-land hooks manipulation. - enumerate - unhook - re-hook - supports any x64/x86 Windows DLL - x64 -> x86 support - available byte-by-byte comparison - cautious (self-unhook first) mode - written in C https://t.co/a9KQKKkUKp
github.com
Windows user-land hooks manipulation tool. Contribute to ars3n11/MineSweeper development by creating an account on GitHub.
3
110
255
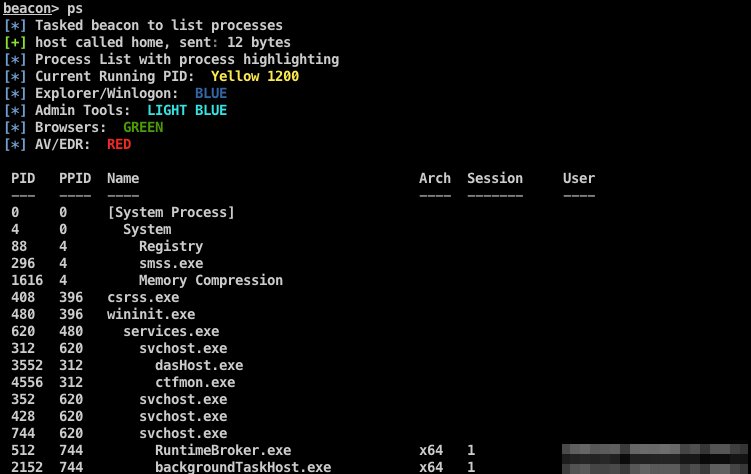
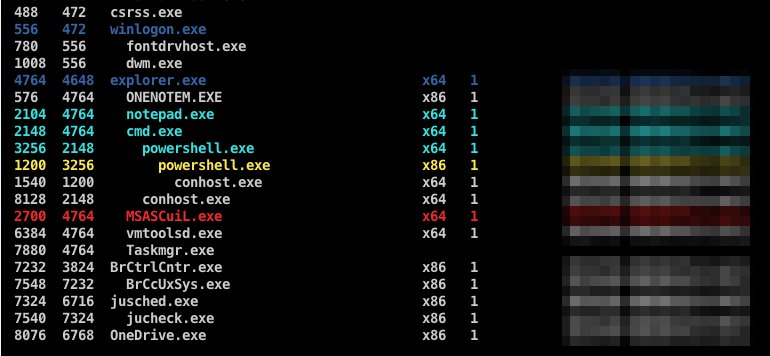
ProcessTree.cna - #cobaltstrike aggressor script to build a process tree. Based off @r3dQu1nn's ProcessColor.cna for better session prepping and OpSec. https://t.co/k94x2VMyRw
3
74
143
If you use MSBuild for your payload delivery, make that pop-up look legit with /noconlog /nologo flags and a simple Console.WriteLine() in the project file itself.
0
0
2