Ahmed L Shnawy
@AhmedLShnawy2
Followers
18
Following
121
Media
1
Statuses
274
Security Engineer | CRTP | OSCP (in Progress)
Joined April 2020
Just earned the Certified Red Team Professional (CRTP) from Altered Security A 24-hour, hands-on exam compromising modern Active Directory environments using real-world techniques Big thanks to @AlteredSecurity and @nikhil_mitt
#CRTP #RedTeam #CyberSecurity #ActiveDirectory
2
2
6
Created a private bookmarklet packed with features to extract hidden paths, URLs and endpoints. It fetches data from HTML elements, inline scripts, quoted strings, performance logs and even external JavaScript files for deep reconnaissance.
11
46
307
use this payload everywhere.simple but effective '"><svg/onload=prompt(7);>{{7*7}}
4
55
310
try this amazing FFUF Oneliner that i use mostly to bypass WAfs and for good & refine results for information disclosure bugs oneliner shared in tg channel: https://t.co/x9BSUPtcYL
7
52
307
Hey @AhmedLShnawy2, congratulations for finding all the flags on the VulnForum challenge! #ctf #hacking #infosec
0
1
2
If your API consumes XML, check out this XML Attacks mindmap by @harshbothra_ for the list of potential exploits to be aware of and links to further reading. XMind version: https://t.co/rHxF1t5LLP PDF:
drive.google.com
1
53
117
Checklist and Cheatsheets WAPT- https://t.co/YTtemCZoGJ Authenication- https://t.co/VB2zj0HVhg Oauth Misconfiguration- https://t.co/pNDaiQXXWX File Upload- https://t.co/DnGZb0eidJ IDOR- https://t.co/d7p8mqlewi XSS- https://t.co/c4wPY9eQec
#bugbountytips
github.com
Collection of methodology and test case for various web vulnerabilities. - KathanP19/HowToHunt
9
376
687
How Github recon help me to find NINE FULL SSRF Vulnerability with AWS metadata access https://t.co/P1nJsogj6c
notifybugme.medium.com
Hi, everyone
0
48
153
Guys check out my latest talk with @trouble1_raunak where he has shown his research in cloud pentesting where he found Illicit Consent Grant Attack on Azure. 🔥 https://t.co/mQoSvSVEIg
#cloudpentesting #infosec #bugbounty
0
15
50
Subdomains brutforce wordlists collection:- https://t.co/UyA6WuXXg5
github.com
Contribute to emadshanab/Subdomains-brutforce-wordlists-collection development by creating an account on GitHub.
0
67
152
A collection of my favorite Bug Bounty Resources & Disclosed reports ordered by Vulnerability Types Hopefully useful for both starters and experienced Bug Bounty Hunters Check out my repo: https://t.co/bX2LCAJ8iv
#BugBounty #BugBountyTip #BugBountyTips #InfoSec
9
220
537
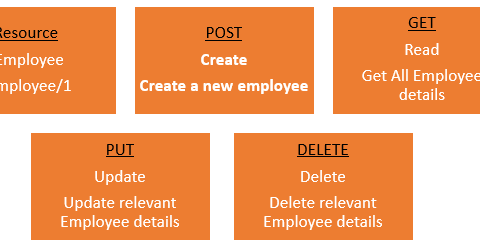
Web API Testing Interview Question & Answers:- https://t.co/Z9GwEAU9db
https://t.co/TYGu77Rtc5
https://t.co/hjhbuR9G7S
https://t.co/EMa81uH1jX
https://t.co/CWnFZbgTHr
https://t.co/8GaMosdDvK
https://t.co/uHk55yNy4x
https://t.co/WrGeA4wCKu
guru99.com
1) Explain what is REST and RESTFUL? REST represents REpresentational State Transfer; it is a relatively new aspect of writing web API. RESTFUL is referred for web services written by applying REST ar
0
71
122
API Checklist,Tips,Wordlists Collection:- https://t.co/BahItApfM2
https://t.co/75NegPEhRK
https://t.co/Ol5rwGosnr
https://t.co/WLZhQ5veWk
https://t.co/Bhr9PGHbQh
https://t.co/DBzofvFbBD
https://t.co/3LRipGY8ok
https://t.co/Uk9KGzQCbC
https://t.co/BMHIIboBdV
wordlists.assetnote.io
Wordlists that are up to date and effective against the most popular technologies on the internet.
1
193
380
API Security Testing – How to Hack an API and Get Away with It:- Part 1:- https://t.co/mY0benPtHG Part 2:- https://t.co/UG9JSYyvd4 Part 3:- https://t.co/FANcUGVFjI
2
106
247
Xss in asp pages reflected inside span and < blocked. Payloads: %u003Csvg onload=alert(1)> %u3008svg onload=alert(2)> %uFF1Csvg onload=alert(3)> #bugbounty #bugbountytips
7
124
322
New attacks on OAuth: SSRF by design and Session Poisoning by @artsploit
portswigger.net
Intro The OAuth2 authorization protocol has been under fire for the past ten years. You've probably already heard about plenty of "return_uri" tricks, token leakages, CSRF-style attacks on clients, an
8
430
890