UselessChris
@aUselessChris
Followers
3K
Following
2K
Media
452
Statuses
3K
Blockchain stalker and high risk investor.
Scandinavia
Joined July 2009
Okay so I've received a ton of questions since starting to post these delayed honeypots. Mainly these two:. - How can it be a honeypot when every scan is showing a clean/safe when renounced contract?. - How can I find out that it's a honeypot when the scanners doesn't show it?
38
48
176
With @VictusGlobal_ seemingly out of the picture, these would be the final stats:. @WChainNetwork received:.$1m. Victus received:.3,023,342,146 $WCO. 30.23% of total supply.51.8% of circulation. Market value of $WCO on delivery:.$1,758,937.88. Discount given to Victus:.43.15%.
4
6
19
Add @INFAICommunity $INFAI to tokens to avoid. LP will get drained later on, and I suspect that any real users buying among the fake volume until then will get their bag siphoned. 0x756d2c966eF280D84b1c17dA185146Bb1Aa78B3f.
Scammers always try to get ahead and it looks we have a string of new projects that manage to trick most standard automated audits. So avoid @MarginAiNet $MARGIN as the LP will get drained. LP being burnt is irrelevant in this case. 0x7135476F3D048c97C3E9007f2848372fd8765184.
2
1
4
Scammers always try to get ahead and it looks we have a string of new projects that manage to trick most standard automated audits. So avoid @MarginAiNet $MARGIN as the LP will get drained. LP being burnt is irrelevant in this case. 0x7135476F3D048c97C3E9007f2848372fd8765184.
2
1
5
Been a while since I did any predictions on fresh tokens, but barring any panic moves from the team side I'd expect @maze_chat $MAZE to be pushed hard the upcoming week or so before a quick exit on team wallets. Stay safe. 0x4b5AaE28e585a7C28d1A7Bba70BBb5fD376Eabb9.
3
0
7
Any #Globiance users might want to be vigilant about sharing too much information here. Your personal deposit txns and addresses are not needed to figure out where your funds went.
@saveourplanet_9 @B3lle888 @moberito @Frankixdc @WalterW64317879 @MichelCrypto1 @AmanAze369 @XSwapProtocol @XDC_Network_ @globiance @Oliver_LaRosa Blame games aside, let's get to the bottom of this . and figure out what @Oliver_LaRosa really did with user funds. If you'd like to help, please share (here or via DM) any addresses you know to be associated with Globiance/Oliver, and any other data+information you have.
3
13
26
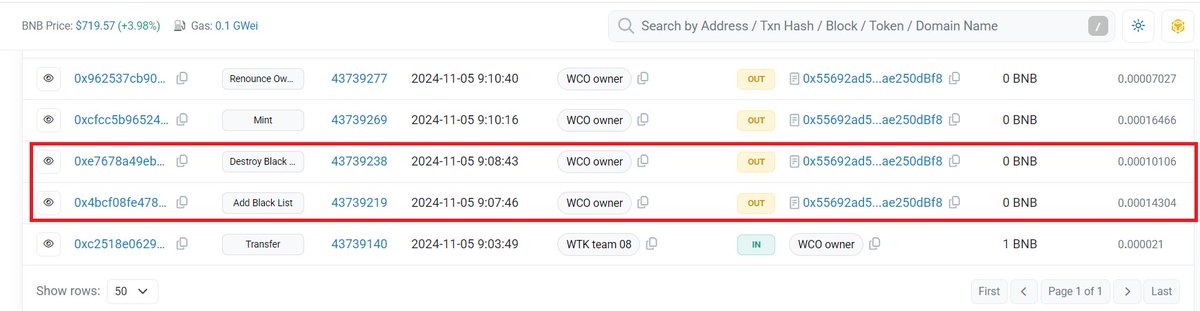
14/ On the positive note for $WCO supporters, this does show that 15m $WCO was indeed recovered from the hack, intentional or not. It is however far from the 375m claimed that we have previously concluded would be a mathematical impossibility.
16/ 375m $WTK recovered?. Hard no. With 1.17b sold, it would not even be possible to seize more than 161m. On top of that, any blacklisting done can be seen on-chain. Not a single hacker wallet ever got blacklisted.
0
1
1