prodigiousMind
@_prodigiousMind
Followers
18
Following
0
Media
28
Statuses
38
PROGRAMMER | FULL-STACK DEVELOPER | CYBERSECURITY
Joined June 2021
Would you rather click on a suspicious link in an email or download an unknown attachment from an email?. #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking #ethicalhacking #programming #programminghelp #CyberSecurityAwareness #Tips #CyberSecurity #Quiz #Analytics.
0
0
0
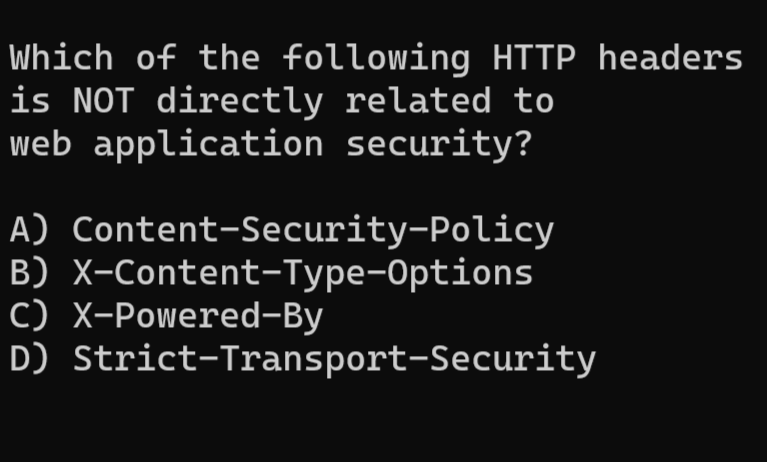
#spot_the_bug.What is the correct option?.Don't forget to Like ❤️, Retweet 🔃, Follow 🤝.#CyberSec #cybersecuritytips #infosec #Hacking #ethicalhacking #CodingChallenge #programming #programminghelp #SQL #database #javascript #HTML
0
0
0
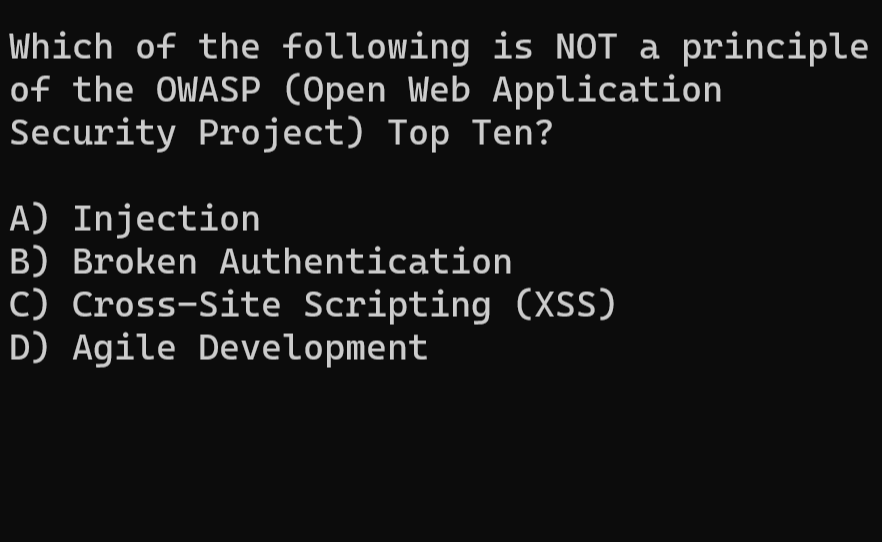
#spot_the_bug.What is the correct option? .Don't forget to Like ❤️, Retweet 🔃, Follow 🤝. #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking #ethicalhacking #CodingChallenge #programming #programminghelp #SQL #Database
0
0
2
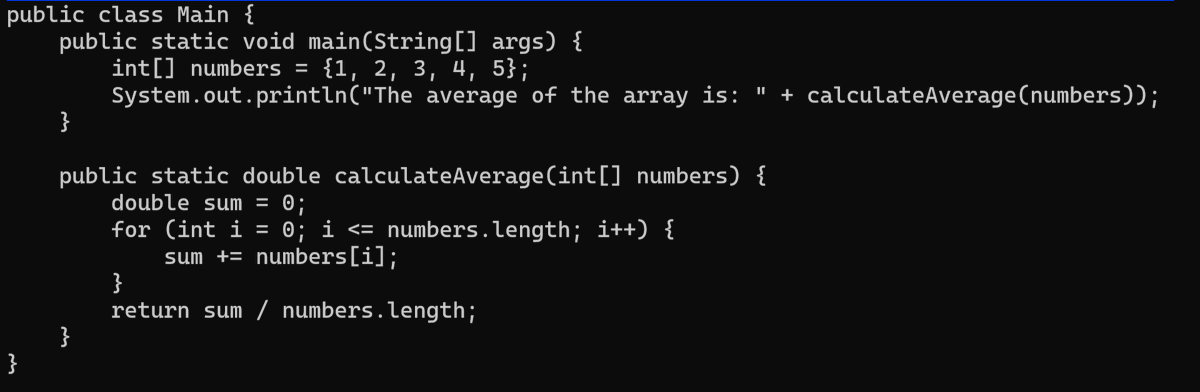
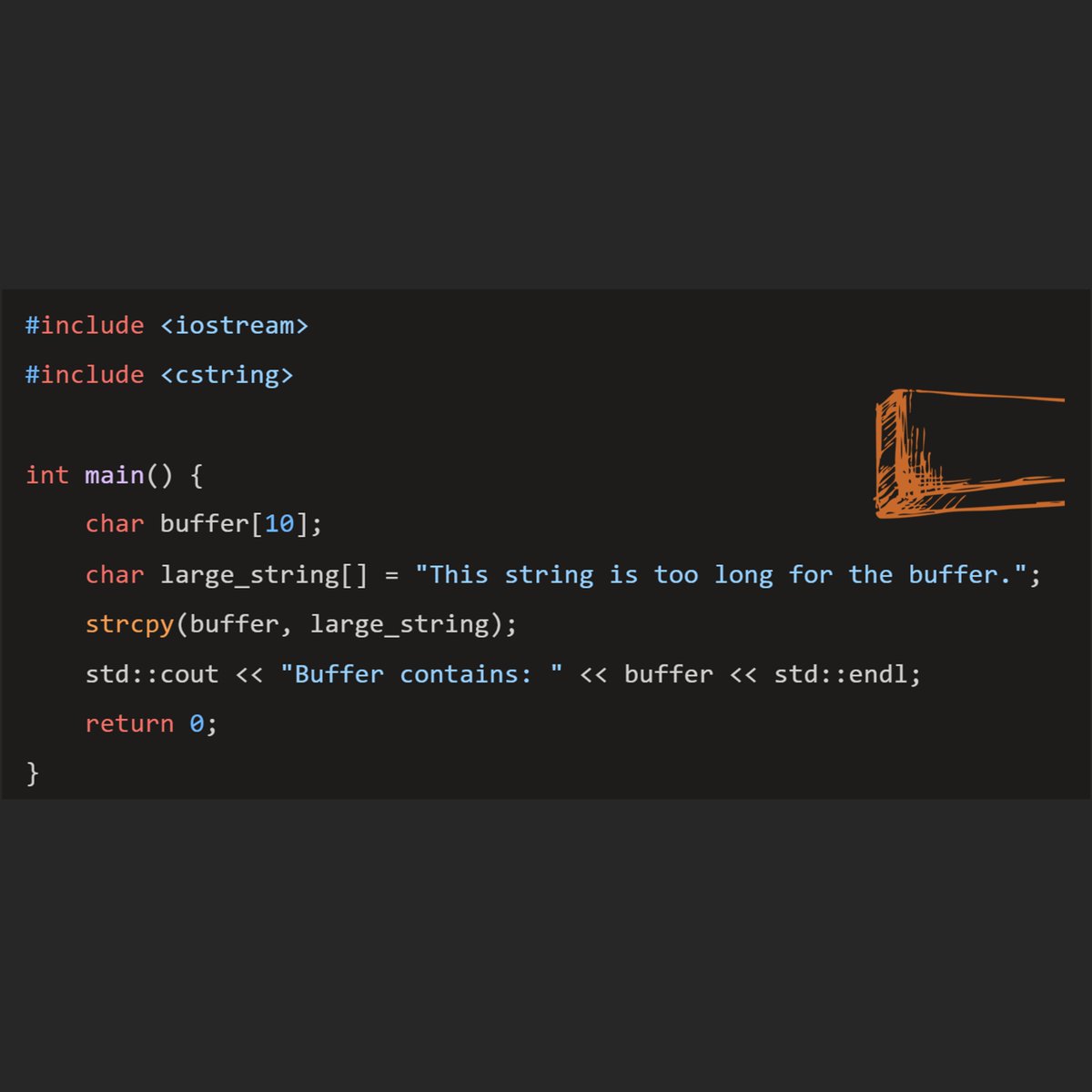
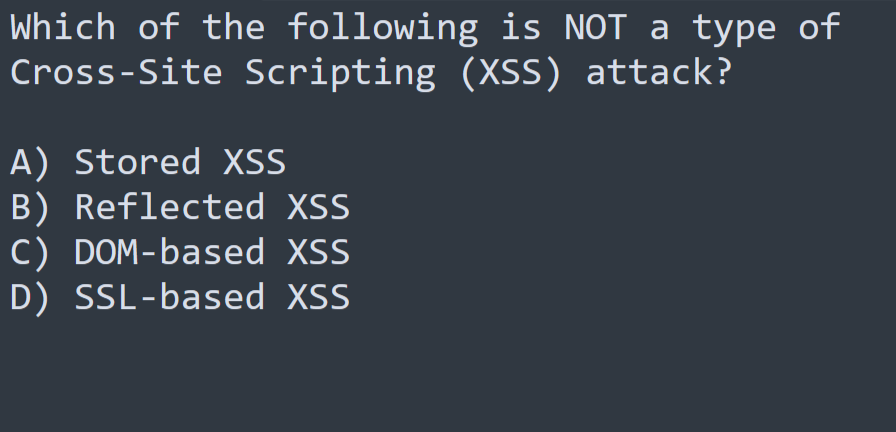
#spot_the_bug.What is wrong with this code?. Don't forget to Like ❤️, Retweet 🔃, Follow 🤝 .#bugbountytip #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking #ethicalhacking #CodingChallenge #programming #programminghelp
0
0
0
- Introduction to Cyber Attacks, New York University. - Cryptography I at Stanford. - Pen Testing at Charles Sturt University. - RITx: Cybersec Fndmntls & RM.
itmasters.edu.au
This course will help you gain an in-depth understanding of the security posture of your IT environment through penetration testing.
0
0
0
Free Online Cybersecurity Courses. #ethicalhacking #CyberSec #infosecurity #freecourses #onlinelearning #onlinecourse #cybersecuritytraining #courses
1
0
0
Don't forget to Like ❤️, Retweet 🔃, Follow 🤝.#websecurity #bugbountytip #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking #ethicalhacking #CodingChallenge #programming #programminghelp #spot_the_bug
0
0
0
Explanation with Demonstration of ARP Poisoning Attack: ARP spoofing is possible because ARP is a stateless protocol and does not have a method for authenticating the origin of ARP replies. #ethicalhacking #networking #infosecurity #cybersecuritytips.
0
0
0
Don't forget to Like ❤️, Retweet 🔃, Follow 🤝. #websecurity #infosecurity #CyberSecurity #cybersecuritytips #infosec #Hacking #ethicalhacking #Security
0
0
0
Don't forget to Like ❤️, Retweet 🔃, Follow📷. #websecurity #infosecurity #CyberSecurity #cybersecuritytips #infosec #Hacking #ethicalhacking #Security
0
0
0
Comment to answer Don't forget to Like ❤️, Retweet 🔃, Follow 🤝. #websecurity #bugbountytip #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking #networking #CyberSecurityAwareness
0
0
0
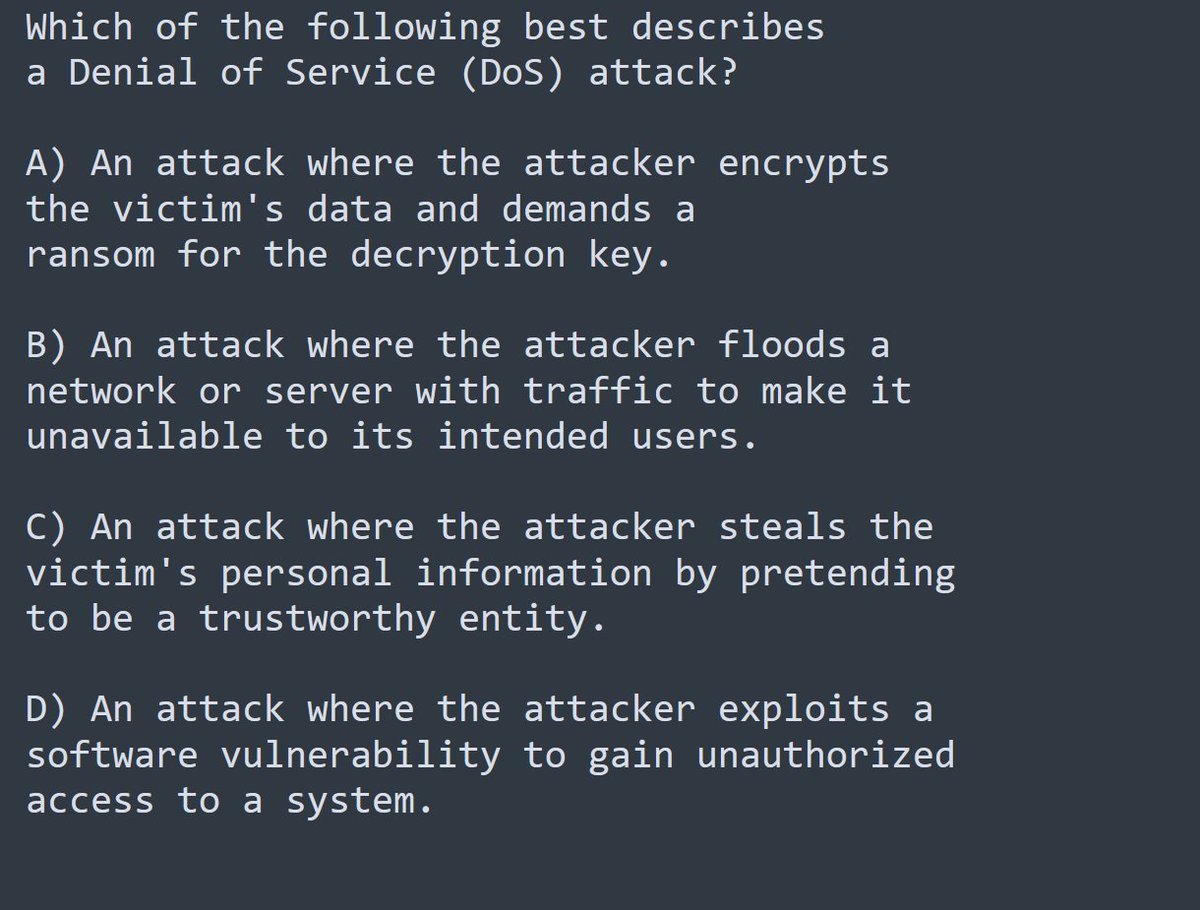
In the context of Cybersecurity, what does CIA triad stands for. A) Confidentiality, Identification, Authorization.B) Contextualization, Integrity, Authentication.C) Confidentiality, Integrity, Availability.D) Contextualization, Indentation, Availability. #CyberSecurity #Hacking.
0
0
0
Comment to answer.Don't forget to Like ❤️, Retweet 🔃, Follow📷 🤝. #websecurity #bugbountytip #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking
0
0
0
Comment to answer.Don't forget to Like ❤️, Retweet 🔃, Follow🤝. #CyberSecurity #websecurity #bugbountytip #infosecurity #CyberSec #cybersecuritytips #infosec #Hacking
0
0
0
Comment to answer.Don't forget to Like ❤️, Retweet 🔃, Follow 🤝. #ethicalhacking #CyberSecurity #websecurity #bugbountytip #infosecurity #CyberSec #cybersecuritytips
0
0
0
One Liner to extract all the links from a file & URL using Grep. 1. From URL.curl [URL] | grep -o 'http[s]*://[^"]*'.2. From File.cat [FILE] | grep -o 'http[s]*://[^"]*'. #bugbountytip #ethicalhacking #SecurityCode #CyberSecurity #bug #hunting #bash #grep.
0
0
0
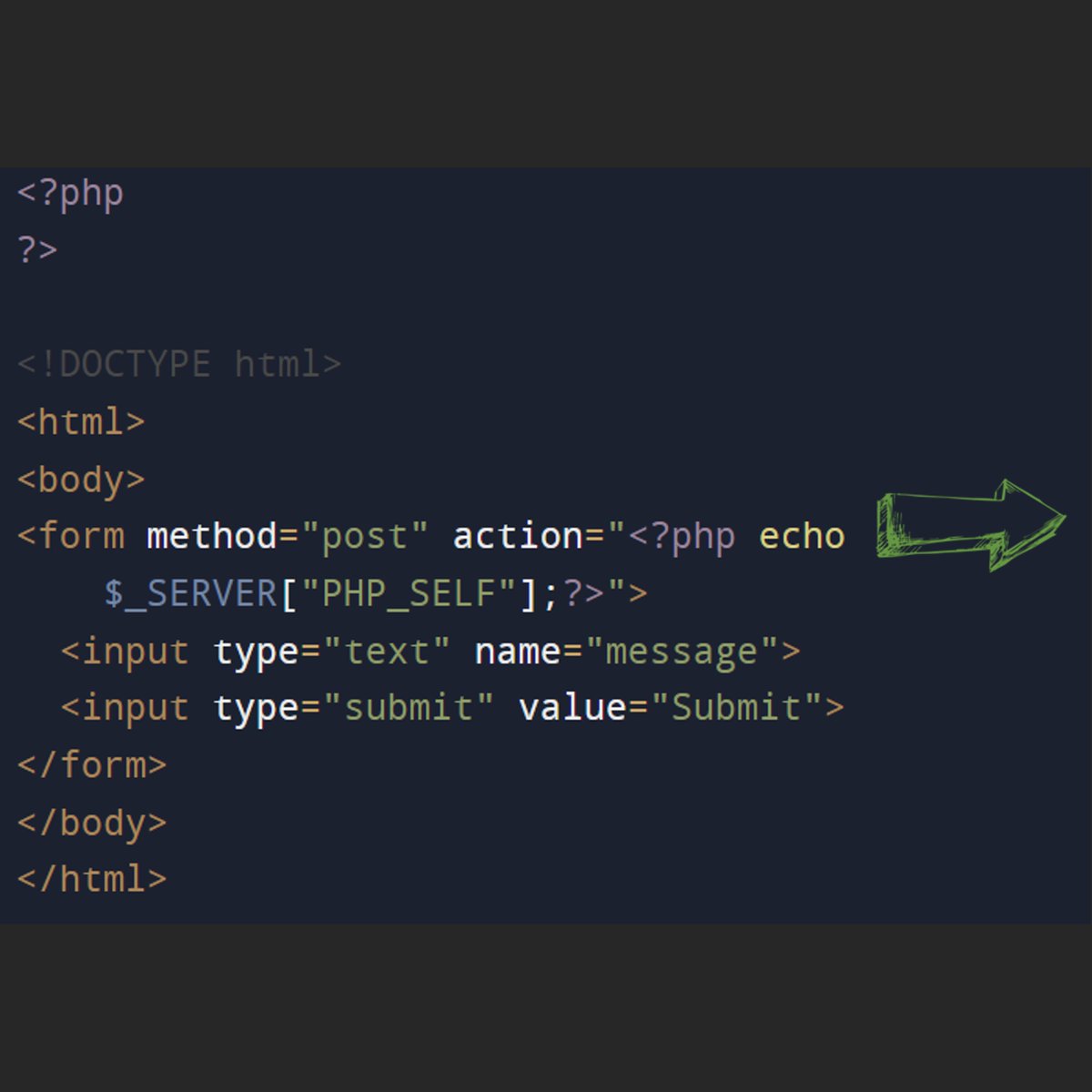
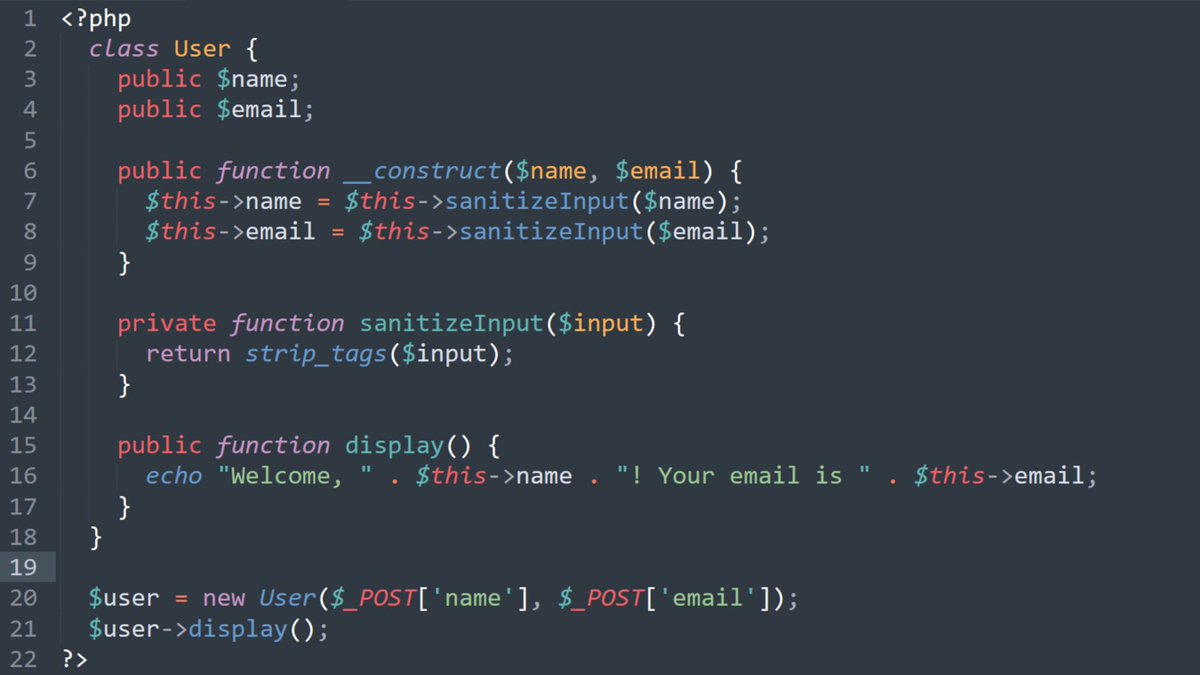
#SPOT_THE_BUG #learn_Programming. The below PHP snippet is vulnerable to which type of vulnerability and at which line it is present?. #ethicalhacking #bugbountytip #infosecurity #CyberSecurity #CyberSec #programming #php #Coding
0
0
0
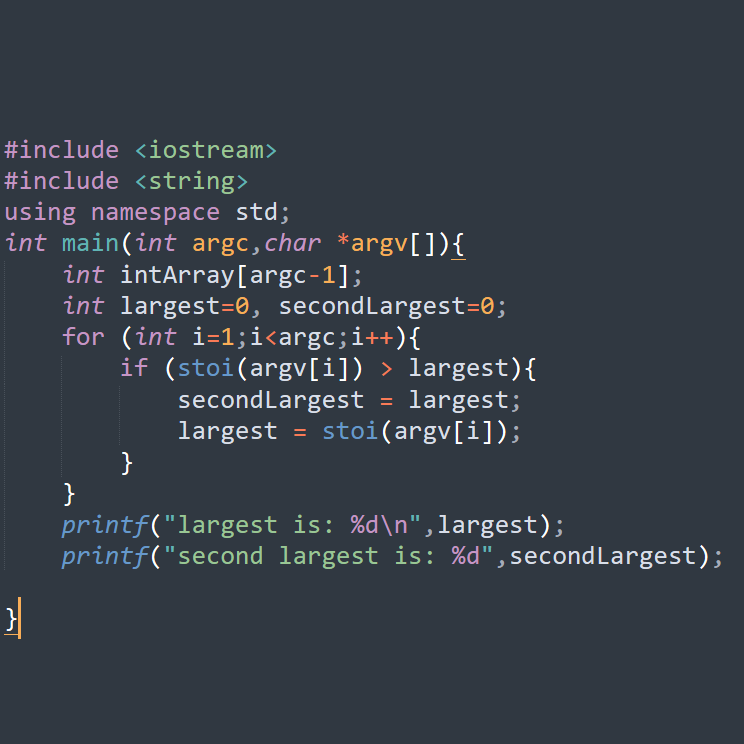
#SPOT_THE_BUG.#learn_Programming. In the below C/C++ program, where is the bug?.If you can catch, comment your answers down below with the bypass input arguments. [HINT]: IF condition. #programming #ethical_hacking #cybersecurity #ethicalhacking #infosec #cplusplus #coding
0
0
1
#learn_Linux2.From the options given below, choose the most appropriate one to view modified files (in /) within last 30 mins. > find / -type -f -time 30.> find / -type f -time -less 30.> find / -type f -mmin -30.> find / -type f -mmin 30. #cybersecurity #ethicalhacking #Linux.
0
0
0
#learnLinux_1.From the options given below, which one represents a hidden file (file1) in a Linux directory?.> _file1.> .file1.> +file1.> ./file1. #cybersecurity #ethicalhacking #linuxOS #Linux #infosec #learnLinux #informationsecurity.
0
0
0