Medusa
@_medusa_1_
Followers
462
Following
320
Media
3
Statuses
38
Joined May 2013
Super glad to have collaborated on @albinowax’s research this year with @bsysop and @_medusa_1_. Funny enough, it all started with a random Slack DM that revealed a potential research collision with James, and things took off from there.
8
6
113
I'm thrilled to announce "HTTP/1 Must Die! The Desync Endgame" is coming to #DEFCON33! This talk will feature multiple new classes of desync attack, mass exploitation spanning multiple CDNs, and over $200k in bug bounties. See you there!
10
89
526
I've recently put more work into my ffuf fork, uff, and I think every ffuf user should at least give it a try - and maybe even switch to it. Here's why, in a #bugbounty 🧵
12
76
475
I’m excited to introduce Namespace Confusion, a novel attack discovered during Gareth's and mySAML Roulette: The Hacker Always Wins research. We uncovered a brutal attack on XML signature validation that destroys authentication in Ruby-SAML!
You might have noticed that the recent SAML writeups omit some crucial details. In "SAML roulette: the hacker always wins", we share everything you need to know for a complete unauthenticated exploit on ruby-saml, using GitLab as a case-study. https://t.co/Ywj2Y7rkIu
1
29
168
Super happy to see our research ranking #3 in @PortSwigger Top Web Hacking Techniques of 2024! 🚀 This one was a wild ride! Huge thanks to @_medusa_1_ & @sw33tLie for the amazing teamwork and to @Bugcrowd, who supported us! ❤️ What next? Keep tuned 👀🥷🏻 #BugBounty #Hacking
10
9
96
Huge news! Our research just ranked #3 in @PortSwigger’s Top Web Hacking Techniques of the Year! 🎉 Biggest lesson: ever assume something isn’t exploitable—test it. Smuggling attacks are far from dead! Massive thanks to my research partners @bsysop & @_medusa_1_ 🙌 #bugbounty
8
8
138
🏆 Top 10 Web Hacking Techniques of 2024 nominations are live, and this time, we’re participating! Our technique is "TE.0 HTTP Request Smuggling" affecting thousands of servers. Vote in https://t.co/PDJYFFoKTK Questions? CC: @_medusa_1_ @sw33tLie
#BugBounty #InfoSec
portswigger.net
Welcome to the community vote for the Top 10 Web Hacking Techniques of 2024.
1
12
89
How novel HTTP request smuggling techniques led to an in-depth investigation and a substantial payout... 🤯 After extensive research and failed attempts, @sw33tLie, @bsysop, and @medusa_1 uncovered a new HTTP Request Smuggling vulnerability 🧩:
bugcrowd.com
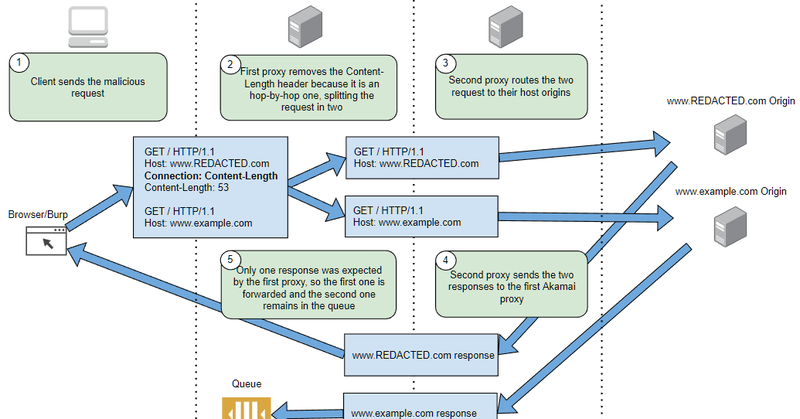
We later discovered we had a powerful exploit affecting thousands of Google Cloud-hosted websites that were using their Load Balancer.
0
5
30
🐝 Hive Five 181 - What the Dying Teach the Living --- 🔍 Innovative recon tool alert: Lemma, a Python-based AWS Lambda package for executing command-line tools in a scalable, remote environment. @defparam 🕵️ Unveiling TE.0 HTTP Request Smuggling: A critical vulnerability
2
5
10
It’s been a while since last publication on the hop-by-hop vulnerability affecting Akamai. Special thanks to @bsysop, @sw33tLie, the Google team, and @Bugcrowd for their invaluable support. https://t.co/Ys3FssSxSM
bugcrowd.com
We later discovered we had a powerful exploit affecting thousands of Google Cloud-hosted websites that were using their Load Balancer.
0
12
61
Servers with top-notch security measures like authentication, authorization, and ZeroTrust can still fall prey to HTTP Smuggling 🏴☠️. Proud to work with @_medusa_1_ and @sw33tLie on this discovery. Genius guys! 🚀🧠 https://t.co/TpUFG7ckS3
#BugBounty @Bugcrowd
bugcrowd.com
We later discovered we had a powerful exploit affecting thousands of Google Cloud-hosted websites that were using their Load Balancer.
4
38
126
BIG round of applause for this BIG find! 👏🐛📈
This is one of the most widespread and impactful bugs I've ever found in my career. Great collab with @bsysop and @_medusa_1_ Smugglings are still out there—stay vigilant! #bugbounty @Bugcrowd
https://t.co/9bxshffknF
0
2
27
This is one of the most widespread and impactful bugs I've ever found in my career. Great collab with @bsysop and @_medusa_1_ Smugglings are still out there—stay vigilant! #bugbounty @Bugcrowd
https://t.co/9bxshffknF
13
67
277
0
1
5
I just published a post on Medium about the most relevant vulnerability I have found in my life so far. "Worldwide Server-side Cache Poisoning on All Akamai Edge Nodes ($50K+ Bounty Earned)":
medium.com
Introduction And Context
6
92
266
https://t.co/WN2iD4wQow TL;DR: Overall bounty of USD 46,000! 😱🥳 First post by @_medusa_1_ showing the outcomes of his most recent #bugbounty activity which led to the detection of an HTTP Request #Smuggling #vulnerability on several big Corp. #cybersecurity #bugbountytips
5
99
252
really it's not fun for me, some @Hacker0x01 trigger team don't care about reports without understand the report quickly close it as N/A or dups, i had 4 reports it was closed as dups and i talked with them to closer look at these reports and they was mistake it was not dups.
20
9
175