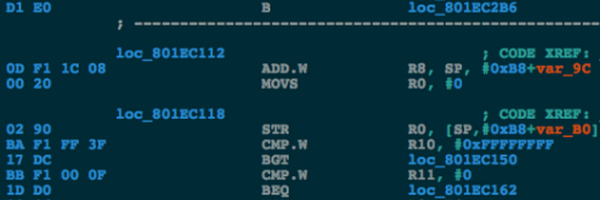
argp
@_argp
Followers
18K
Following
1K
Media
621
Statuses
15K
Hacker. Ascetic. Phrack author. The most technical boy in town.
0x29A
Joined January 2010
Slide deck (PDF) from my #CanSecWest2019 talk "Vs sandbox" on reverse engineering the Apple iOS sandbox kernel extension:
18
110
260
RT @halvarflake: It is pretty interesting that as I age and geohot ages, I end up noticing that we agree on more things than I thought in t….
geohot.github.io
I signed up for Hinge. Holy shit with the boosts.
0
38
0
RT @halvarflake: I would not have dropped out of my PhD if this had been the culture or advice. I left when the process was: look at the c….
0
1
0
RT @spendergrsec: Vibe coding has no place in Linux kernel maintenance. The vulnerability inserted into 5 LTS kernels at once apparently w….
0
23
0