Nenad Zaric
@ZaricNenad_
Followers
2K
Following
805
Media
135
Statuses
593
The @trick3st mission was always to create a "Photoshop" for hackers and bug bounty hunters, enabling them to unleash their creativity. Thank you @PhillipWylie, for having me on your podcast and letting me showcase the power of Trickest!. Enjoy 🥳🥳🥳.
3
9
34
RT @trick3st: ToolShell coverage has been all over the place. We held off publishing until we could reconcile the discrepancies between th….
0
2
0
RT @trick3st: Why spend hours building in-house security workflows when you can deploy proven ones instantly?. Trickest's workflow library….
0
2
0
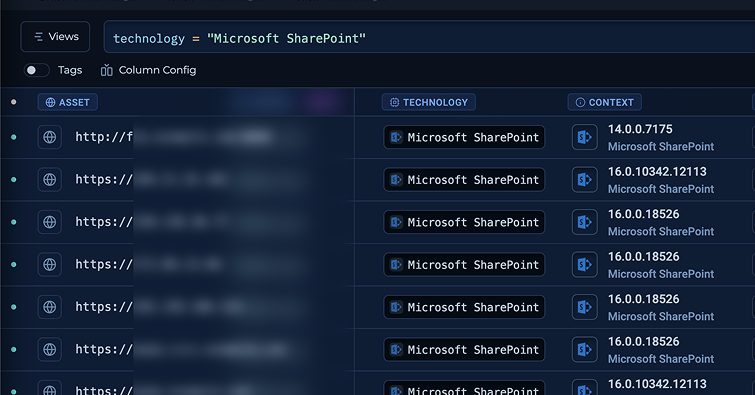
RT @trick3st: Modern attack surface management means having your security data at your fingertips. Query, filter, and analyze your externa….
0
1
0
RT @trick3st: Our top Vulnerability Scanning tools:. - ZAP: Web app vulnerabilities.- Nuclei: Precise scanning, no false positives.- Sqlmap….
0
9
0
RT @trick3st: Trickest Editor now delivers a complete IDE experience for offensive security teams. With unified command line, advanced fi….
0
3
0
RT @trick3st: Impressive work from Verizon's security team on AI-specific Burp extensions.
github.com
Verizon Burp Extensions: AI Suite. Contribute to Verizon/verizon_burp_extensions_ai development by creating an account on GitHub.
0
6
0
RT @trick3st: Managing an evolving attack surface requires visibility, automation, and customizability. Our latest video demonstrates how T….
0
3
0
RT @trick3st: Uncover deeply nested subdomains within your infrastructure using our Recursive DNS Subdomain Discovery module. By emulating….
0
3
0
RT @trick3st: Security infrastructure changes aren't just technical updates—they're your defense timeline. Track them. Learn from them. Wit….
0
3
0
RT @trick3st: "The offensive security world is broken. We spend countless hours installing tools, managing infrastructure, and wrestling wi….
0
3
0
RT @trick3st: Stuck in the classic “build vs. buy” dilemma for your cybersecurity automation projects? . Our latest blog reveals the hidden….
0
3
0
RT @trick3st: Trickest Modules are built for real security work, fully customizable, and scalable without limits—enabling security teams to….
trickest.com
Automate, customize and scale your offensive security operations using top open-source and professional tools, custom scripts, and pre-built workflows.
0
3
0