Dara_Sleuth🛡
@XtopherJoy
Followers
196
Following
3K
Media
46
Statuses
619
Cybersecurity educator | Community builder + content strategist | Social media sales girlie | Music lover 🎵 | Let's talk security, sales & securing the 💰
Port Harcourt, Nigeria
Joined November 2019
70% of the tweets I come across everyday is all about cybersecurity. I followed every single person I noticed was doing good in the cyberspace. People like @ireteeh @sisinerdtweets @CyberSecFalcon @RealCyberDoctor and many other person's that have made it an obligation to help.
DAY 4: Cybersecurity can be challenging. What struggles did you face as a newbie, and for the experts, what challenges are you still tackling today? Let’s share and learn from each other. Best comments win some #Bitcoins 🪙🔥 #RealCyberNation #CybersecurityAwarenessMonth
2
3
15
RT @RealCyberDoctor: AI is coming for your lunch and most are still asleep. It’s not just blue-collar jobs. AI is replacing analysts, co….
0
1
0
Day 34/100.All I can say today is that network security humbled me. I had to go over different terminologies again and again, and I took my quiz multiple times. To all the network Engineers out there you all are doing well🙌 @segoslavia @ireteeh .#100daysofcybersecurity.
0
3
8
This journey is going to be truly worthwhile with you guys💯.
I just got off a call with these amazing people @XtopherJoy @BlessingMo38646 @ojaeagles .We are preparing for the Cyblack mentorship cohort pitch and we shared ideas. It felt like we have been friends for a long while ❤️💯🔥.@TemitopeSobulo @ireteeh @segoslavia @h4ck3r__g1rl
0
0
5
RT @An_gelos_07: Cybersecurity professionals: Don't share your location or activities in real time. Also us cybersecurity people: I'll be a….
0
8
0
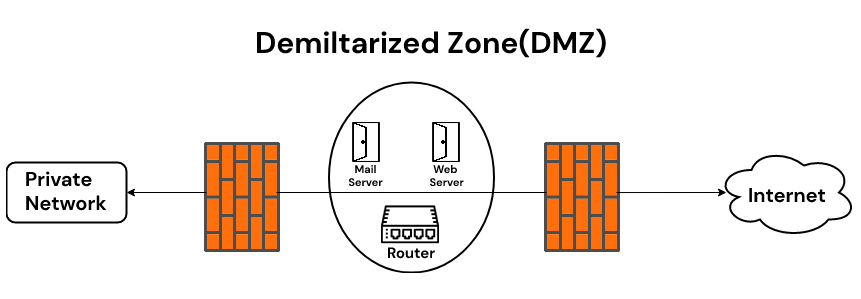
DMZ gets its name from a military concept (a physical area where military forces are prohibited). In cybersecurity, a network DMZ is a segmented zone between your private internal network and untrusted external networks.@segoslavia @ireteeh @elormkdaniel.#100daysofcybersecurity.
1
1
2
Day 32/100:.WPA2 is a security protocol that protects wireless networks from unauthorized access. In today's lab, I first troubleshot internet connectivity issues, then configured WPA2 security for Laptop 1 to secure the wireless connection. @segoslavia .#100daysofcybersecurity
0
3
9
Day 31/100:.This diagram explains how wireless communication occurs without any form of collision through a process called CSMA/CA.RTS – "Can I talk?".CTS – "Yes, go ahead.".Data – "talks".ACK – "Got it!".@segoslavia @ireteeh @elormkdaniel.#100daysofcybersecurity
0
2
14
Using AI for work projects, recipes, learning new skills is fantastic. But your relationship drama, health fears, family issues? Keep those conversations with real humans you trust. Your future self will thank you. Happy new month cyber friends☺️.#dataprivacy.
0
0
1
Day 30/100:.Today's learning was on the key differences between WLAN and wired Ethernet, focusing on why enterprises still prefer wired connections for critical operation. Emphasis on performance consistency & security @ireteeh @segoslavia @elormkdaniel .#100daysofcybersecurity.
1
2
14