Wessel Hissink
@WesSec_
Followers
235
Following
2K
Media
51
Statuses
308
Things I say on Twitter are personal opinions and views. Team Blue | DFIR | Bug bounties Full time Blood Glucose manager
Joined February 2016
PopOS! is underrated.
Some of you need to hear this. Just because @pewdiepie installed Arch Linux doesn’t mean you need to. Ubuntu is fine. PopOS! Is fantastic. Only go down the Arch path if you have a lot of time on your hands or you want to be better than everyone else. :).
0
0
1
It's a great idea to submit your whole AD forest to Claude!! (/s). I feel sorry for the peeps testing this in production (with write rights) and see their AD being demolished in seconds.
Managing Active Directory just got easier. I built Koppla, a local MCP server that lets you interact with AD using natural language. No scripting, no hassle—just clear results. Works with Claude Desktop & GitHub Copilot. Let me know what you think!.
1
0
1
With this KQL query, quickly check if apps with Mail.Send permission actually are sending mails or if they're overprivileged. Is there a repo combining permissions with graph endpoints? Could be interesting.
gist.github.com
Get overpermissioned Mail.Send applications. GitHub Gist: instantly share code, notes, and snippets.
0
0
1
"When eM Client is first granted permissions within a tenant, a service principal is created in Entra ID.". It's good practice to monitor for all service principal creations, here is a simple KQL query to do so:.(exclude automated/non user stuff).
gist.github.com
Monitor service principal accounts. GitHub Gist: instantly share code, notes, and snippets.
0
5
28
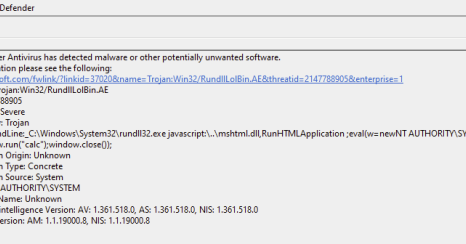
Do you work with ASR? This is a great little blog post that explains a bit about the inner workings of ASR.
l--k.uk
I’ve worked a lot with Microsoft Defender Antivirus, and particularly with the Attack Surface Reduction feature. Having built up some understanding of its inner workings with the help of othe…
0
4
10
Today is a good day to check who and what as access to your data. Google: Microsoft:
Welcome to the era of the token. In the past, attackers had to breach networks, bypass security controls, escalate privileges, and evade detection just to reach confidential data. Now? A single OAuth authorization - granted with one click - can hand over access to emails, files,.
0
0
1
We need to stop calling everything a critical vulnerability. You're only vulnerable if you have VerifyHostKeyDNS enabled (it's disabled by default and only enabled in specific situations).
🚨 Critical OpenSSH Vulnerabilities – Patch Prioritization. KQL to identify all your internet facing OpenSSH servers vulnerable to CVE-2025-26466 and CVE-2025-26465. Get your engineers prioritize patching these servers to version 9.9p2 that is released today. Shields Up Scotty!
0
0
4
@BertJanCyber BTW: the neat trick used by attackers is that Microsoft AD Graph activity is not logged, when the Microsoft Graph API is used, you should be able to detect the actual activity (beyond authentication) via MicrosoftGraphActivityLogs table.
2
0
2