timbMSFT
@TimbMsft
Followers
2K
Following
27
Media
48
Statuses
152
Partner Research Director, Microsoft Security Research
Cheltenham, United Kingdom
Joined April 2017
Trust underpins securing identity - trust in MFA devices, your admins, ... A critical area is your certificate server -- if you can't trust those certs then your entire environment is at risk. Read more at https://t.co/askR6gugvb & use #MDI to protect your ADCS servers
0
6
16
Big news on the work front! Today is my last day at @Secureworks, and I’d like to thank you for the opportunity to work with such fantastic people to make the world safer! My journey continues in January with #Microsoft as a Principal Identity Security Researcher. I’ll be working
82
26
567
Noteworthy to see this cybercrime threat group pivoting across cloud and on-premises environments #ThreatIntelligence #cloudsecurity #Identity
In this episode of THE Microsoft Threat Intelligence podcast, we talk Octo Tempest (0ktapus, scattered spider, unc 3944). https://t.co/5nKwOIWcks
0
0
4
... and a timely reminder that passwordless is now even easier - deploy policies to remove passwords from your users' Windows 11 experience https://t.co/apUA7pix9X
0
0
0
Credit to Alexander Sverdl from @atlant_security for reminding me of this sketch https://t.co/TInNbYevOY
facebook.com
You Should Probably Change Your Password! Michael McIntyre’s Brand New Netflix Stand Up Comedy Special Showman Launches 15th of September 2020.
1
0
0
A key question in identity-related investigations is WHAT did that user or service principal do? So super happy to see 🔥 Microsoft Graph activity logs now in public preview 🔥 #dfir #EntraID #MicrosoftSentinel
https://t.co/pJvFY9oo0O
0
1
12
Security is a team sport - working together🤝to 🔥expose threat actors🔥and keep people safe online https://t.co/BonwSaif5Z
blogs.microsoft.com
Microsoft, Amazon, and international law enforcement have come together to send a strong message to perpetrators of tech support fraud: There will be consequences for their actions.
0
2
4
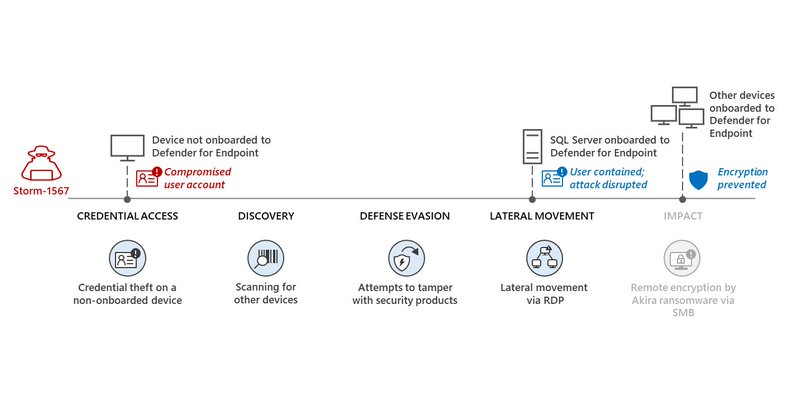
Identity surfaces across the kill chain -- eg initial access in phishing; and (to devastating effect) lateral movement using compromised user creds as ransomware actors spread across a victim environment. Read about MDE user containment & disruption:
microsoft.com
User containment is a unique and innovative defense mechanism that stops human-operated attacks by limiting ability to move laterally.
0
2
16
Your new favorite podcast is here! The Microsoft Threat Intelligence Podcast has behind-the-scenes tales about uncovering attacks, threat actors, malware, exploits, etc. from researchers & analysts. Hosted by @sherrod_im. First 3 episodes are live!
thecyberwire.com
Hear directly from the Microsoft Threat Intelligence community as they navigate the evolving threat landscape, uncovering untold stories of APTs, malware, and other weird and cool tools and tactics...
1
43
148
Read more about #Zeek's open-source integration with Windows resulting in #MDE customer detection value! https://t.co/MNkK6aZPOW
techcommunity.microsoft.com
Microsoft Defender for Endpoint is now integrated with Zeek, a powerful open-source network analysis platform.
0
1
0
Read how NetworkProtection and #threatintel combine to proactively block c2 connections #MDE #Ransomware
https://t.co/RhCccDx27Y
0
1
1
Read how Raspberry Robin malware fits into the wider cybercriminal ecosystem, & how turning on attack surface reduction rules, enabling tamper protection, and a range of #MDE alerts can help defend against these attacks. #Microsoft365Defender
https://t.co/rwrh9dmSOj
0
0
2
Now you can see that the same user being flagged for #AzureAD unfamiliar sign-in had just clicked a suspicious URL (#MDE #EDR) - all from within the #Microsoft365Defender portal :) https://t.co/y8rTRAqf0b
0
0
3
🧵We are excited to share that @Zeekurity is now a component of @Microsoft @Windows ! An incredible development that truly establishes Zeek as the de facto standard for #networkevidence: https://t.co/jM8b0AZ8d3 1/4
corelight.com
Zeek, world’s leading open source network security monitoring platform, now deployed on more than one billion global endpoints via Microsoft Windows
5
130
346
Microsoft Defender for Identity can monitor ADFS signals -- or put differently the crossover point between on-premises & cloud identity, repeatedly targeted by NOBELIUM to pivot from on-premises to cloud -- read how to use #MDI to detect such threats
techcommunity.microsoft.com
Using a recent example of a hybrid identity attack, learn how to protect against them!
0
2
6
Expose hidden corners of your network through device discovery 🔥now augmented with signal from Microsoft Defender for Identity🔥 https://t.co/Y1BmPuFllp
#MDE #MDI #MicrosoftDefender
0
0
3
Microsoft Detection and Response Team (DART) was engaged to lead the investigation on destructive cyberattacks launched against the Albanian government in mid-July. We assess that the attack was launched by an Iranian state-sponsored actor. Full report:
3
157
337
"The cold, cruel war is raging wildly but I will sow seeds of peace again and again. Garden of hope I foresee and spring is always lovely." -- Bhuwan Thapaliya
0
0
4
Here are the technical details from @MsftSecIntel on the destructive (faux-ransomware) malware targeting multiple organizations in Ukraine https://t.co/pQJiKgkEW5
microsoft.com
Microsoft Threat Intelligence Center (MSTIC) has identified evidence of a destructive malware operation targeting multiple organizations in Ukraine.
BREAKING: Ukrainian officials now linking defacement to Belarusian actor UNC1151/Ghostwriter. Some have tied the group to Russia as well and they could be a joint unit. They also claim there was a destructive component possibly linked to APT29! 11/x
1
19
84