Mike Takahashi
@TakSec
Followers
26K
Following
3K
Media
401
Statuses
3K
Pentester | Bug Bounty Hunter | AI Red Team
Palo Alto, CA
Joined May 2012
Speaking at @defcon this year!🎤.“Misaligned: AI Jailbreaking Panel”. Catch @elder_plinius, John V, Ads Dawson, @PhilDursey, @_Red_L1nk, Max Ahartz 🔥.Moderated by the legendary @Jhaddix 🚀. 🏴☠️ BT6 goes deeper than this panel, shoutout to:.@rez0__ , @MarcoFigueroa, Svetlina.
LAST MINUTE ADDITION! Don't miss "Misaligned: AI Jailbreaking Panel" featuring BT6 members @elder_plinius, @TakSec, @phildursey, and others; moderated by @Jhaddix on Sunday, August 10 at 10:00 AM inside the Village. Read more at #BugBounty #DEFCON33
1
11
37
If it's refusing basic prompt injection attacks, try jailbreak guardrail bypass methods such as:
infosecwriteups.com
How to Bypass LLM Protections Using Obfuscation for AI Red Teaming
0
1
7
RT @KarthiDreamr: Unicode has more invisible characters than you think. ✅ Common ones (like U+200B, U+200C, U+2060) are valid, zero-width….
0
3
0
RT @Ph1R3574R73r: @BugBountyDEFCON @TakSec @elder_plinius @PhilDursey @Jhaddix Nice something to do on Sunday 🎉.
0
1
0
RT @BugBountyDEFCON: LAST MINUTE ADDITION! Don't miss "Misaligned: AI Jailbreaking Panel" featuring BT6 members @elder_plinius, @TakSec, @p….
0
24
0
RT @0dinai: 0xEA9D8872: Multiple Model Guardrail Jailbreak via "Pronunciation Bypass" Tactic. Credit to Mike Takah….
0din.ai
We are building for the next generation in GenAI security and beyond.
0
1
0
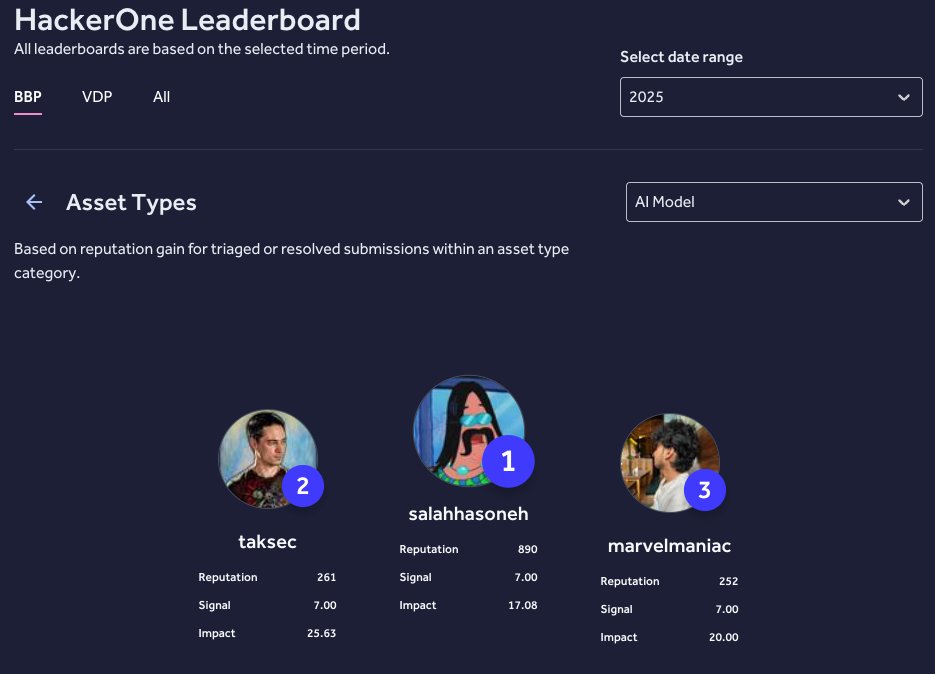
Hackerone Leaderboards for categories exist apparently 😲. #2 for AI Model vulnerabilities this year across all @Hacker0x01 . Shoutout to @SalahHasoneh1 for #1 and @0xmarvelmaniac #3
3
3
61
RT @Ph1R3574R73r: 🧠 The Best Jailbreaks Don’t Look Like Jailbreaks. If your prompt starts with “Tell me how to make…” you’ve already lost.….
0
2
0
Full details in the official disclosure page on @0dinai .
0din.ai
We are building for the next generation in GenAI security and beyond.
0
0
4
RT @Ph1R3574R73r: 🔁 TL;DR – Prompt Engineering for Model Behavior Research. 🎭 Set a believable role.🧠 Use language and tone that fit the do….
0
1
0